Communication protocol method for consensus authentication of blockchain common nodes
A technology of public nodes and communication protocols, applied in the field of communication protocols, to achieve the effect of wide application scenarios and simplified complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
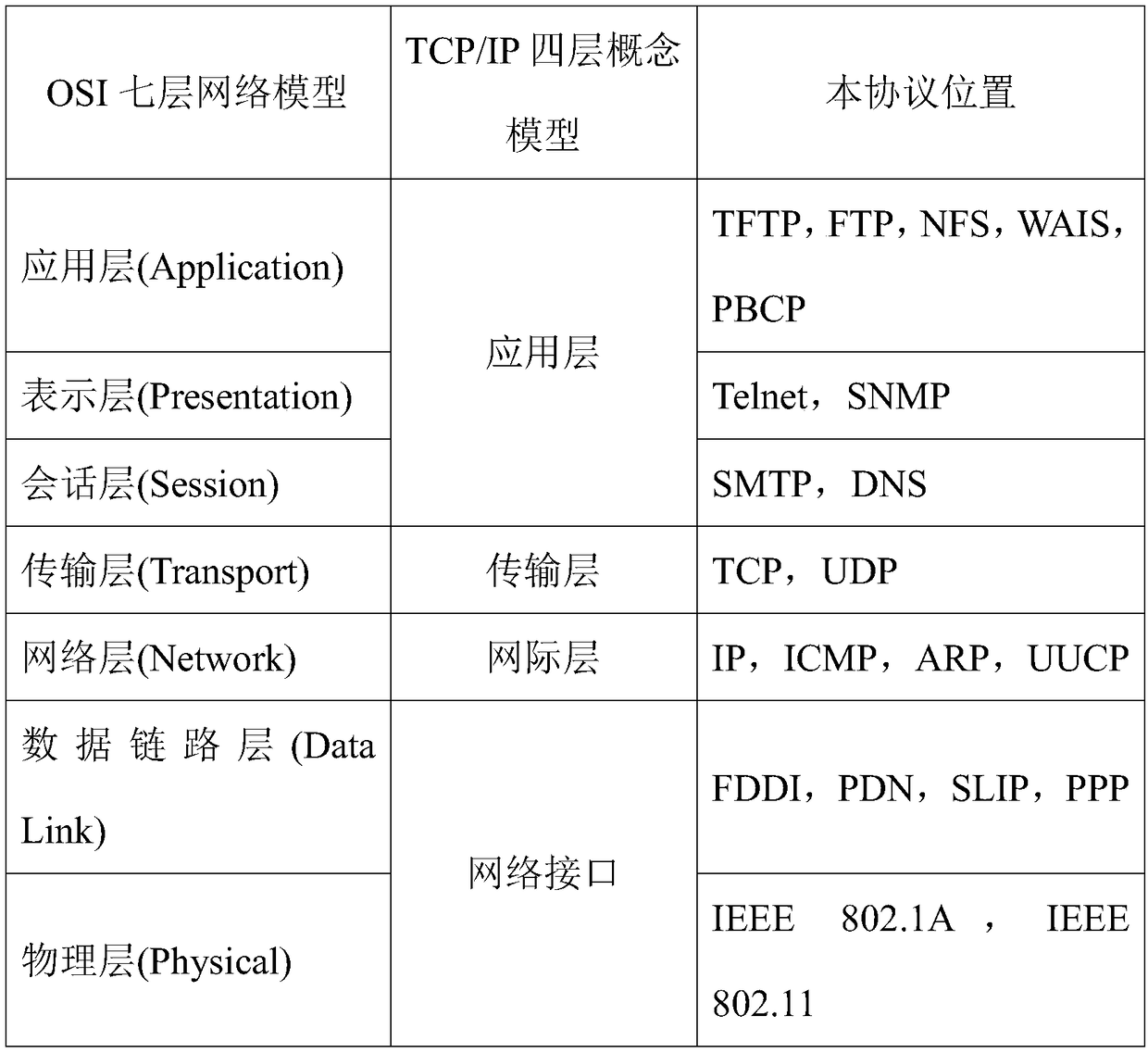
[0020] Embodiment 1, the communication protocol method of the blockchain public node consensus authentication, package PBCP at the application layer of the TCP protocol model. PBCP is the abbreviation of Peers'Blocks Consensus Protocol, which refers to the blockchain consensus protocol based on end-to-end communication. As shown in Table 1, the TCP protocol model in the prior art includes the application layer, the output layer, the Internet layer and the network interface from the perspective of the four-layer concept model, and the technical solution is to package the PBCP communication protocol on the application layer. From the OSI seven-layer network model, it includes application layer (Application), presentation layer (Presentation), session layer (Session), transport layer (Transport), network layer (Network), data link layer (Data Link) and Physical layer (Physical), and PBCP is packaged on the application layer (Application). It has its own communication protocol me...
Embodiment 2
[0034] The communication protocol method of block chain public node consensus authentication described in embodiment 2, comprises the following steps,
[0035] (1) The public node goes online and publishes an access request rqlg message. At this time, the authentication node starts to confirm the identity after receiving the message, and establishes an exclusive end-to-end dedicated line TCP connection channel with the requesting node, and then generates a request The identity authentication information corresponding to the node and return the rplg message to the requesting node;
[0036] (2) The public node confirms itself according to the received identity authentication information, if it is legal, it maintains the exclusive connection of the authentication node, and waits for the local main thread command or the call information sent by other nodes as a listening thread;
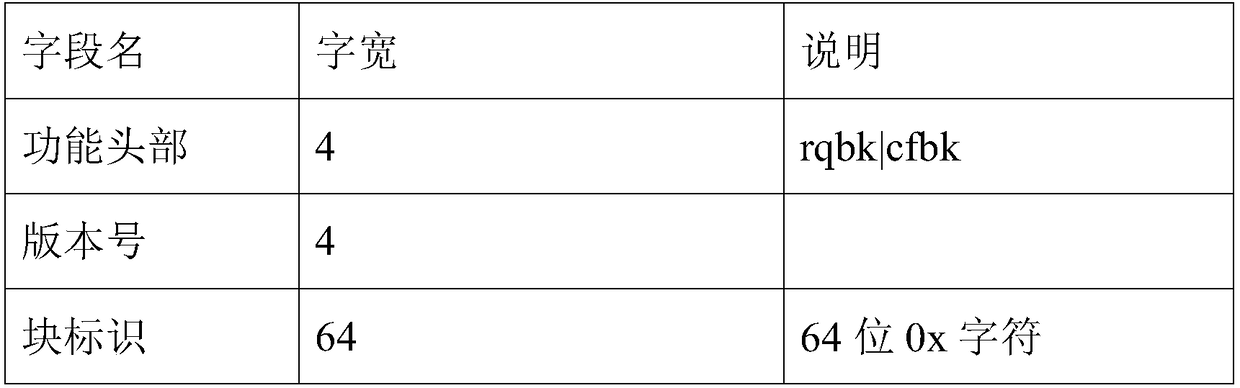
[0037] (3) After the public node receives the command to generate a new block, it will pack the new b...
Embodiment 3
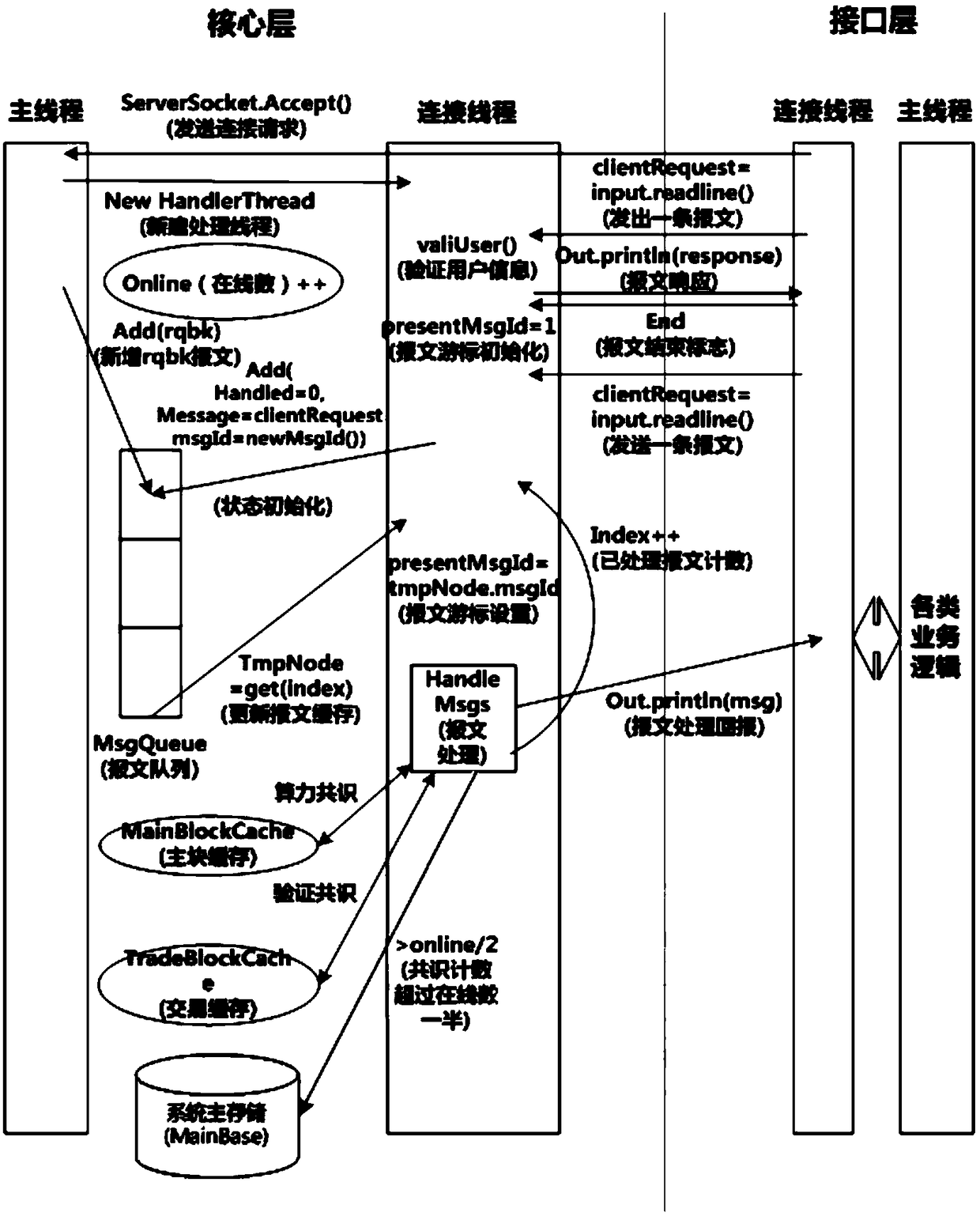
[0040] Example 3, such as figure 1 As shown, the communication protocol method for the public node consensus authentication of the block chain includes the following steps,
[0041] (1) The public node goes online and publishes an access request rqlg message. At this time, the authentication node starts to confirm the identity after receiving the message, and establishes an exclusive end-to-end dedicated line TCP connection channel with the requesting node, and then generates a request The identity authentication information corresponding to the node and return the rplg message to the requesting node;
[0042] (2) The public node confirms itself according to the received identity authentication information, if it is legal, it maintains the exclusive connection of the authentication node, and waits for the local main thread command or the call information sent by other nodes as a listening thread;
[0043] (3) After the public node receives the command to generate a new block,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com