A content-centric network-based signature verification method, device and medium
A content-centric network and signature verification technology, which is applied in the field of content-centric networks, can solve problems such as network congestion, waste of node computing resources, and poor avoidance effect of non-compliant data packets, so as to avoid resource occupation, improve avoidance effect, and avoid The effect of network congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
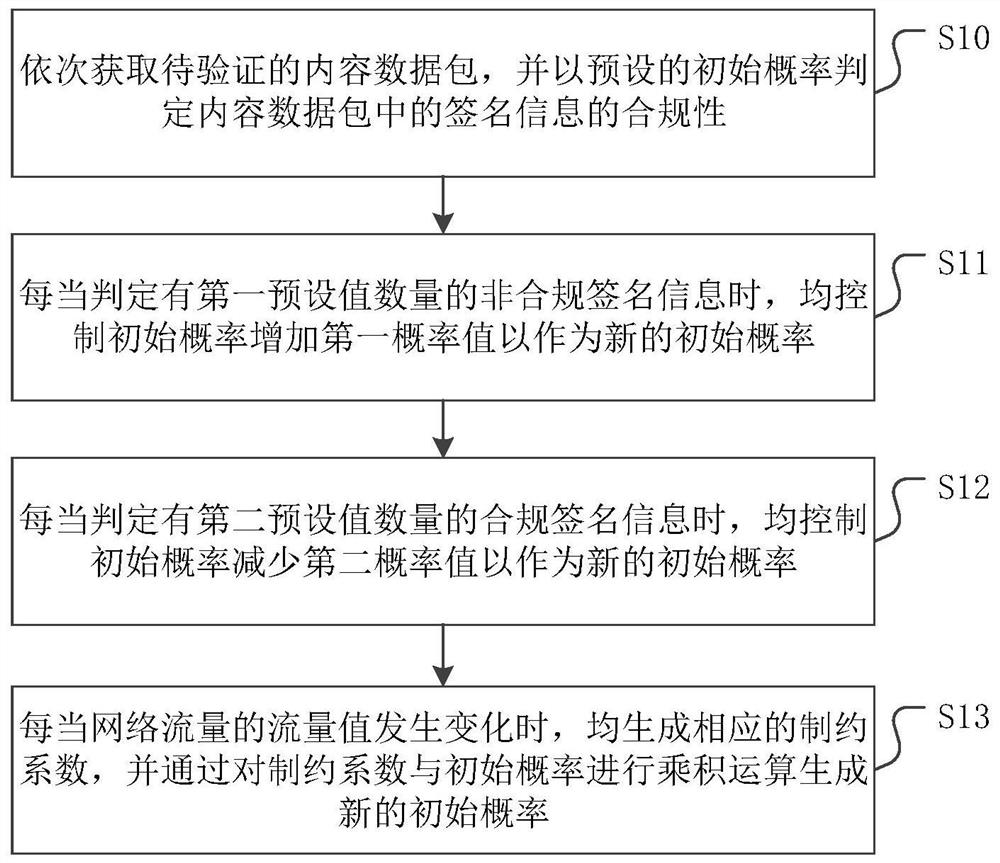
[0041] figure 1 It is a flowchart of a content-centric network-based signature verification method provided by an embodiment of the present invention. Please refer to figure 1 , the specific steps of the content-centric network-based signature verification method include:
[0042] Step S10: Obtain the content data packets to be verified in sequence, and determine the compliance of the signature information in the content data packets with a preset initial probability.
[0043] It should be noted that the execution subject of this step may be a router or a server with a routing function. The content data packet referred to in this step may be the content data packet pre-cached locally, or sent to the local content data packet by other device nodes, which should be determined according to the specific scenario and is not specifically limited here. However, those skilled in the art should know in which scenarios the signature information in the content data needs to be verifie...
Embodiment 2
[0054] On the basis of the above embodiments, the present invention also provides the following series of preferred implementation manners.
[0055] As a preferred implementation, after determining the compliance of the signature information in the content data packet with a preset initial probability, the method further includes:
[0056] When the signature information is non-compliant, remove the content data package;
[0057] When the signature information is compliant, it is judged whether the signature information is passed in by other nodes;
[0058] If yes, it is judged whether the content data packet is pre-stored in the CS buffer;
[0059] If yes, then replace the content data packets pre-stored in the CS buffer with the content data packets imported by other nodes;
[0060] Otherwise, cache the content data packet, and forward the content data packet to the destination node according to the forwarding information in the PIT table.
[0061] What needs to be explain...
Embodiment 3
[0074] The embodiment of the content-centric network-based signature verification method has been described in detail above, and the present invention also provides a content-centric network-based signature verification device corresponding to the method, because the embodiment of the device part and the method part The embodiments correspond to each other, so for the embodiments of the device part, please refer to the description of the embodiments of the method part, and details will not be repeated here.
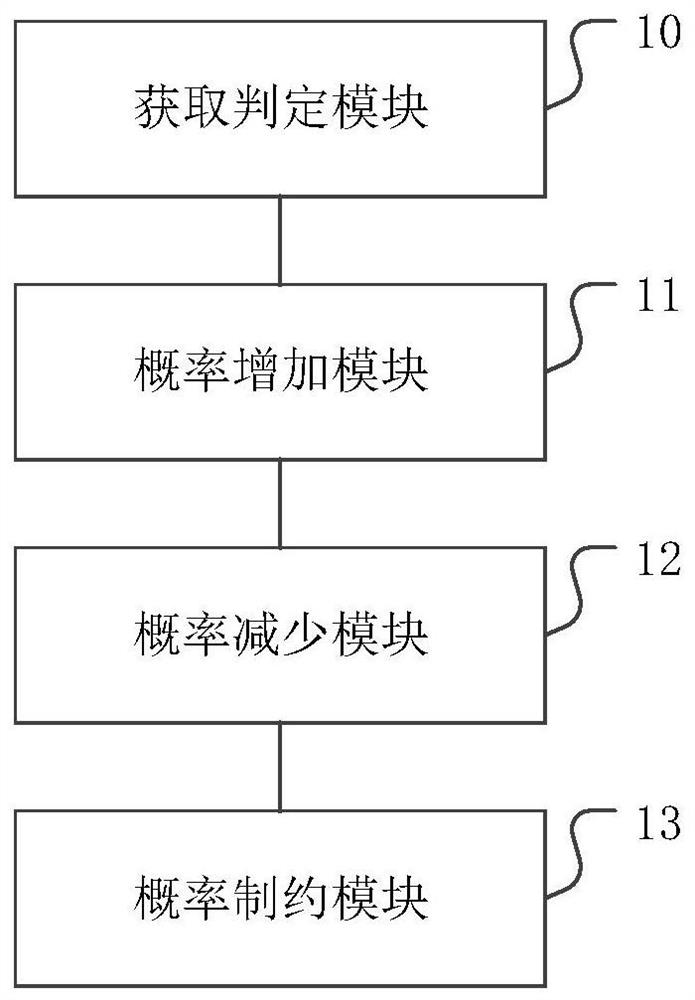
[0075] figure 2 A structural diagram of a content-centric network-based signature verification device provided by an embodiment of the present invention. The content-centric network-based signature verification device provided by the embodiment of the present invention includes:
[0076] The acquiring and judging module 10 is configured to sequentially acquire the content data packets to be verified, and judge the compliance of the signature information in the content d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com