Authentication method and system based on fog computing and used for enhancing communication security
A communication security and fog computing technology, which is applied in encryption authentication technology, fog computing, and Internet of Things security fields, can solve problems such as time and money loss, traffic signal confusion, production process delay, etc., to avoid time and bandwidth consumption and reduce burden , the effect of improving the accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
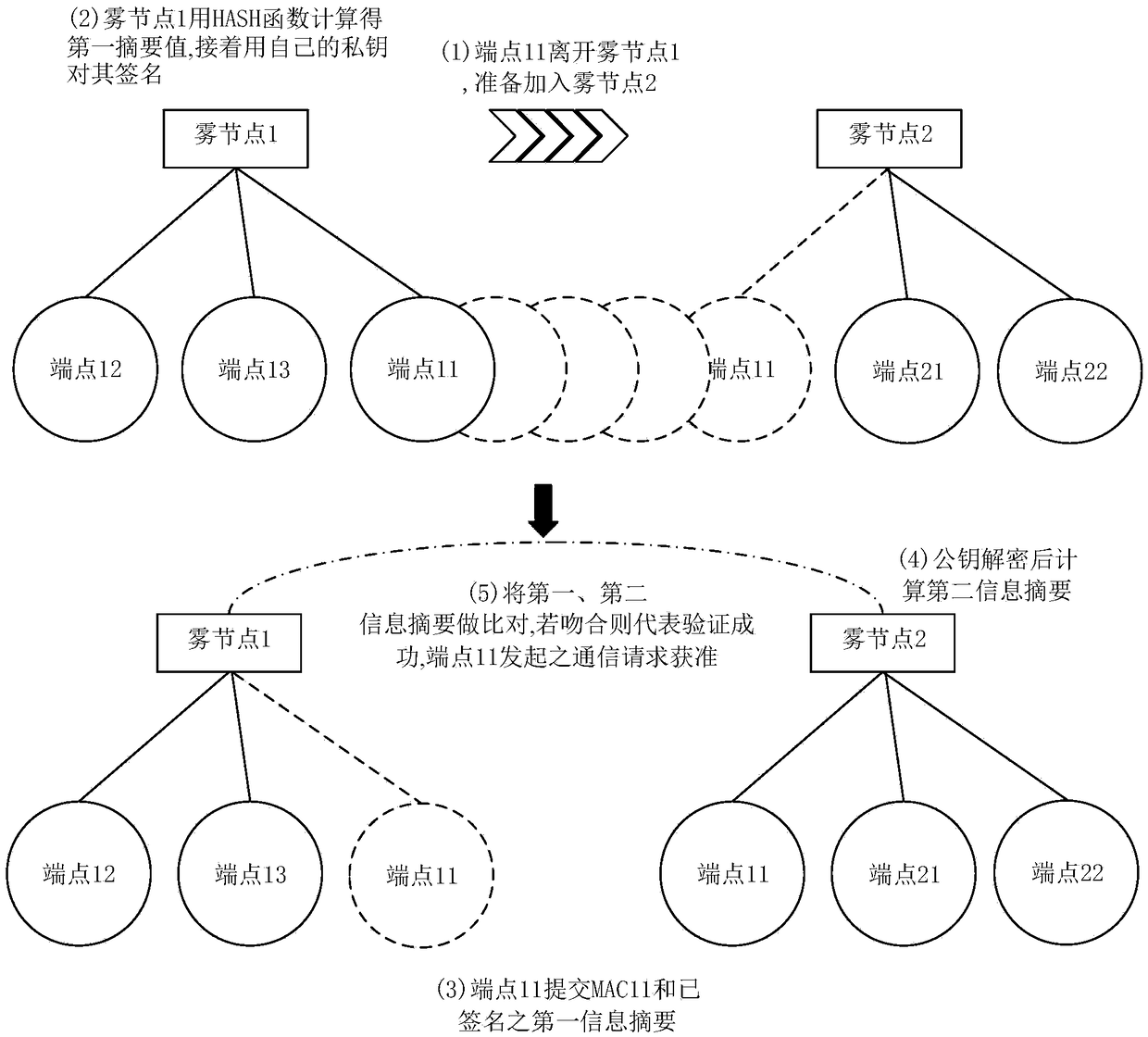
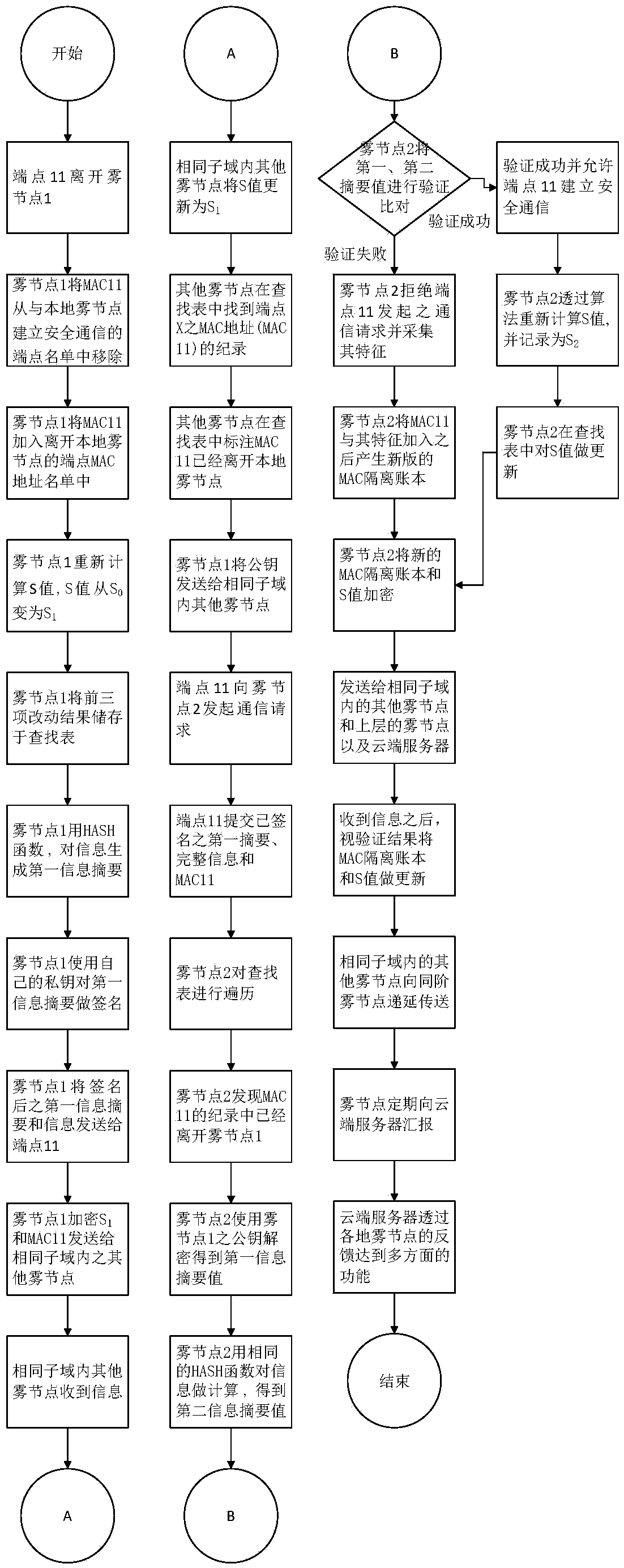
[0048] The present invention provides a method and system for improving communication security between nodes and endpoints and between nodes based on the fog computing framework. By analyzing the existing underlying work of fog computing, the security and privacy deficiencies in it are obtained. A method for enhancing authentication security mechanism and communication security between nodes and endpoints and between nodes is further proposed.
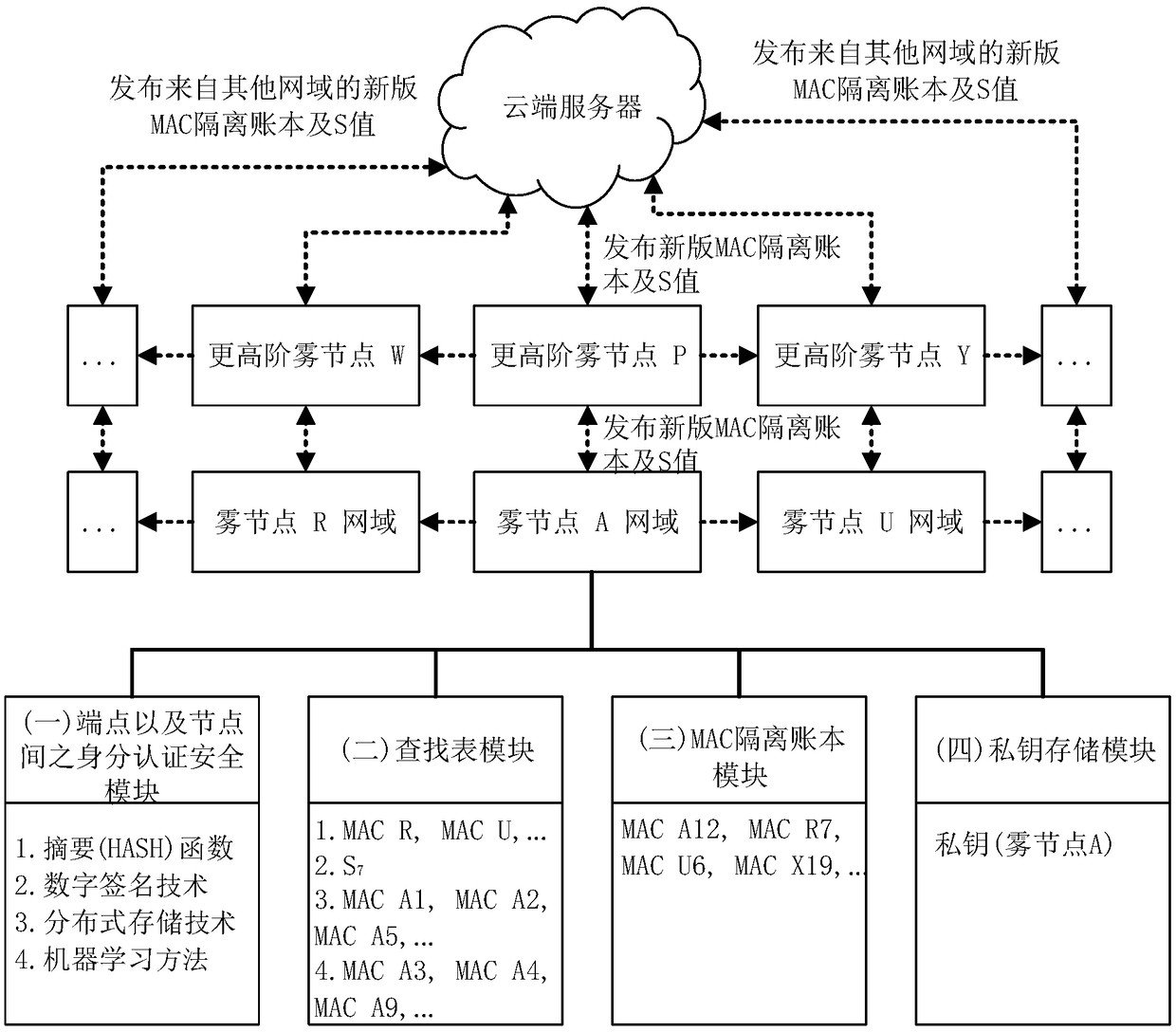
[0049] figure 1 It is a schematic diagram of the module system structure under the fog computing framework provided by the present invention. figure 1 In the network domain of each fog node, there are four modules: (1) endpoint and identity authentication security module between nodes, (2) lookup table module: responsible for saving the following four items ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com