Encryption/decryption method, device and system for random data
A technology of random data and encryption device, applied in the field of big data network, can solve the problem of low security of encryption and decryption method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
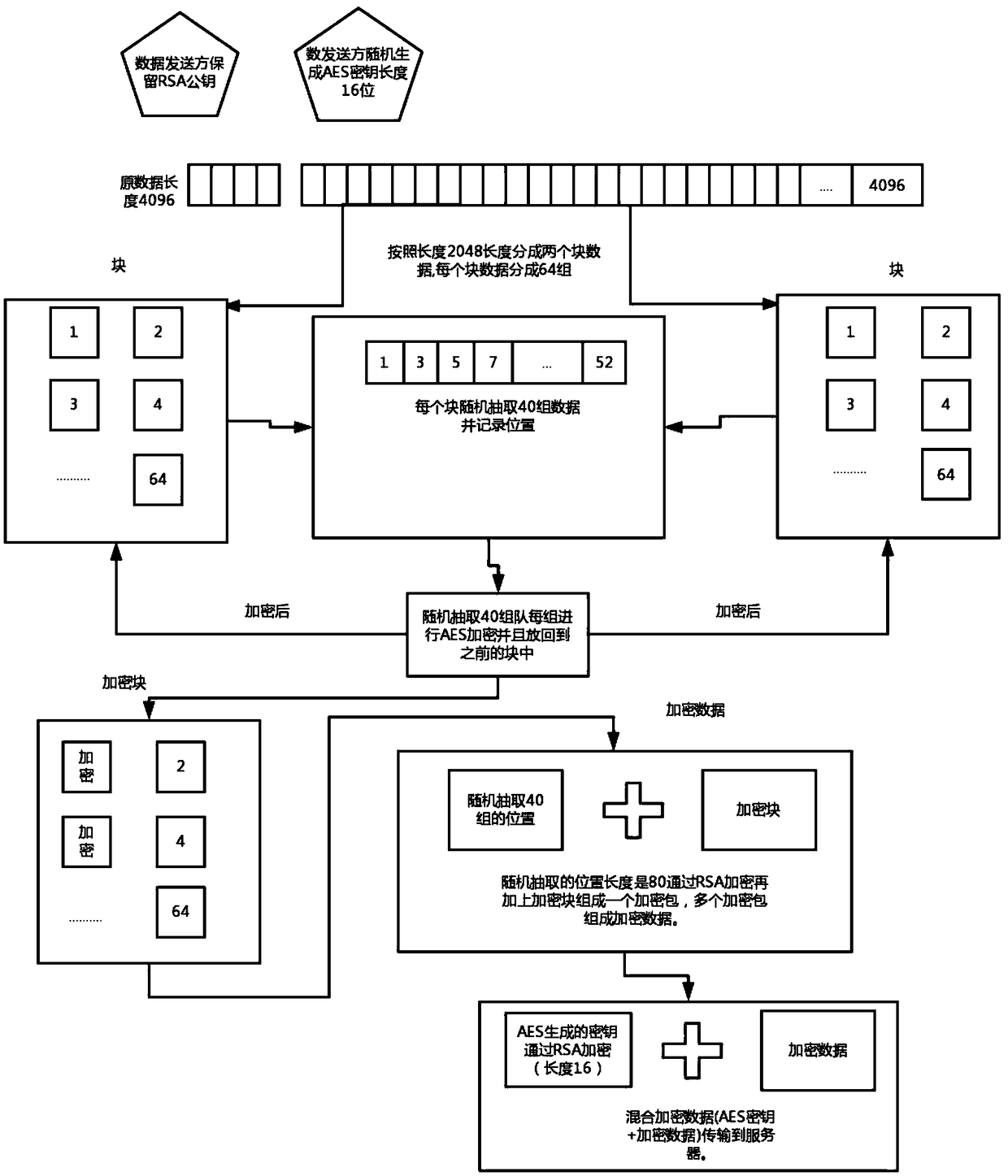
[0046] Such as figure 1 Shown, a kind of random data encryption method, this method comprises:
[0047] Randomly generate a character string with a fixed length of 16, and convert the character string into an AES key with a fixed length of 16;
[0048] If the data length of the encrypted source file is 4096, it is divided into 2 block data according to the preset length of 2048, and then the data in each block is divided into 64 groups, each group length is 32; the original file data is evenly divided into M blocks of data, and then divide each block of data into 64 groups according to the preset length 32;
[0049] Randomly extract 40 groups of data from each block of data, use the AES key to encrypt, record the position length S of the randomly extracted group, and the length of the randomly extracted position is fixed at 2 bits, if it is not enough, add 0 at the end; then encrypt the encrypted 40 The group data is put back into the original randomly selected position, and...
Embodiment 2
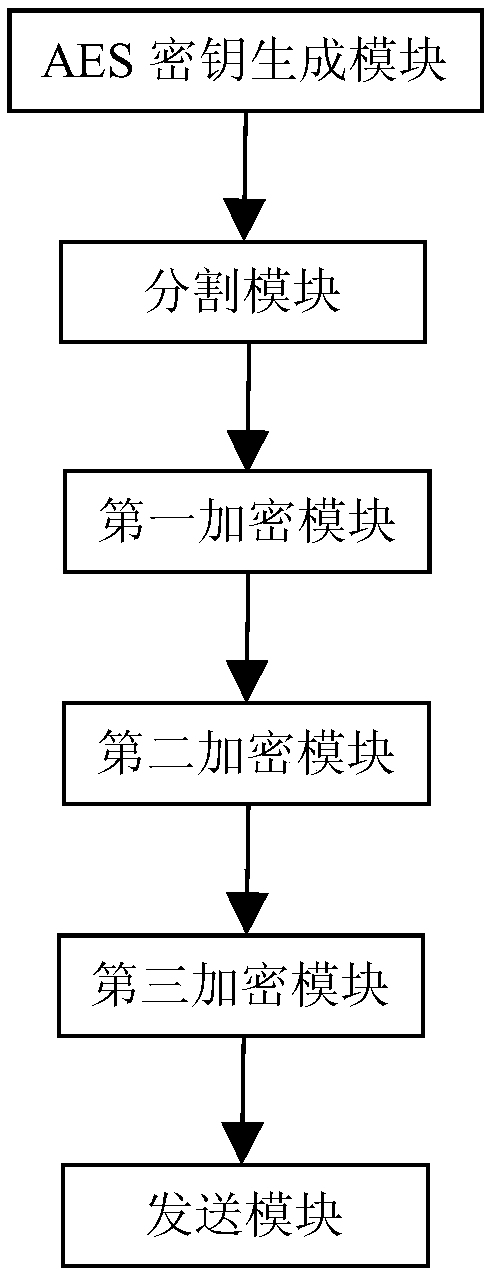
[0057] Such as figure 2 Shown, a kind of random data encryption device, this device comprises:
[0058] AES key generation module, is used for randomly generating the character string of fixed length 16, described character string is converted into the AES key of fixed length 16;
[0059] The segmentation module is used to divide the original file data into M block data according to the preset length L, and then divide each block data into P groups according to the preset length N; if the length of the encrypted source file data is 4096, then according to the preset Let the length 2048 be divided into 2 blocks of data, and then divide the data of each block into 64 groups, each group length 32; divide the original file data into M blocks of data according to the preset length L, and then divide each block of data according to the preset length L Let length 32 be divided into 64 groups equally;
[0060] The first encryption module is used to randomly extract 40 groups of dat...
Embodiment 3
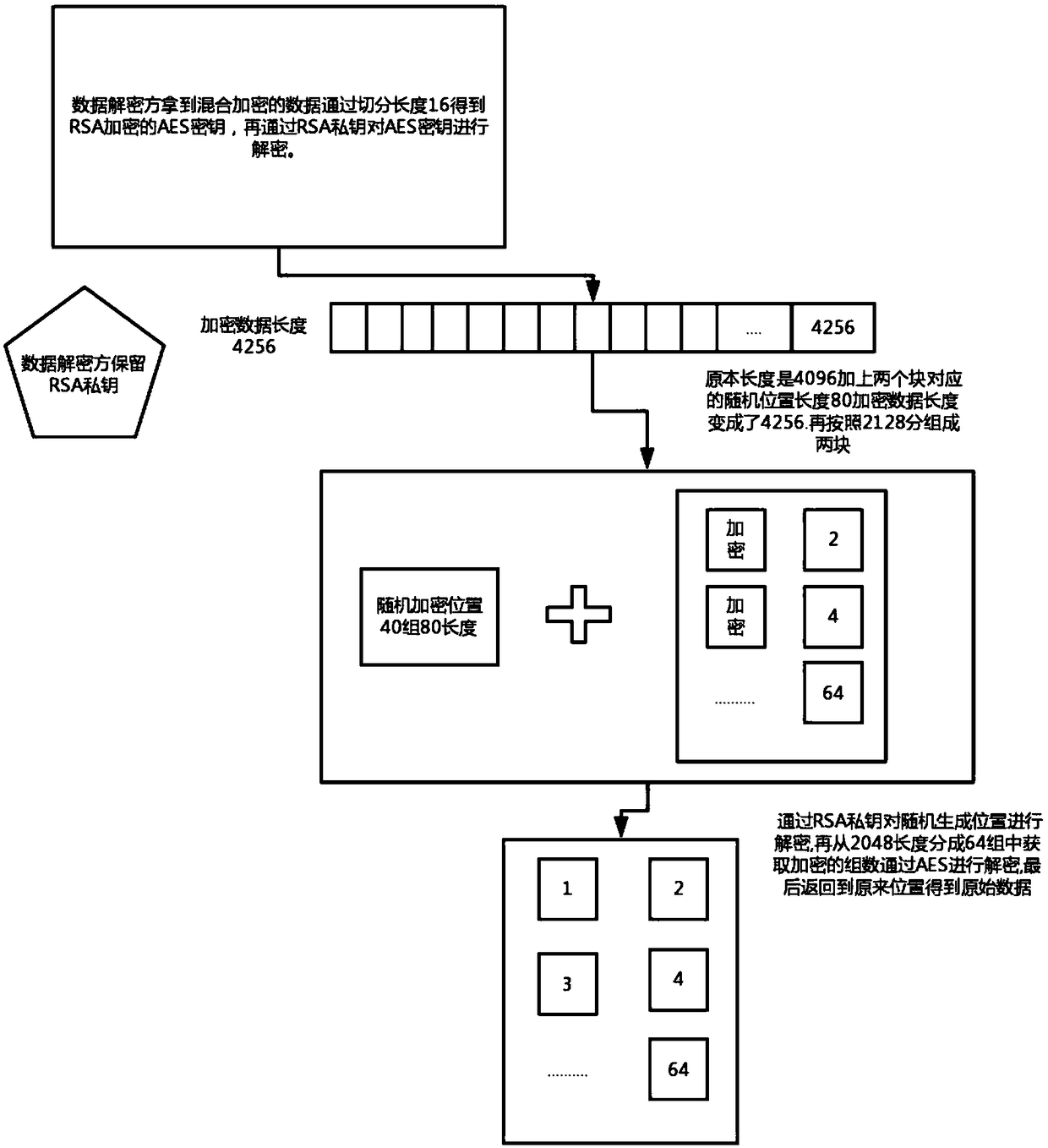
[0066] Such as image 3 As shown, corresponding to the encryption method in the specific embodiment 1, a random data decryption method, the method includes:
[0067] Receive mixed encrypted data;
[0068] Segment the mixed encrypted data according to a fixed length of 16 to obtain the AES key encrypted by the RSA public key and the remaining encrypted data;
[0069] Use the RSA private key to decrypt the AES key;
[0070] According to the total length 2128 of decryption, the remaining encrypted data is divided into 2 block data; the total length of the decryption is: the preset length 2048 plus the position length 80 of the previously randomly selected group;
[0071] Use the RSA private key to decrypt the randomly generated position length 80 in front of each block data;
[0072] Divide each block of data into 64 groups according to the preset length of 32, take out the encrypted data through the position length of the randomly selected group of 80, decrypt it with the AES...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com