A method for side channel analysis of hardware Trojan horses based on multiple ip cores
A side-channel analysis and hardware Trojan horse technology, applied in the field of third-party IP core trustworthiness verification, can solve the problems of model verification and formal verification incapable of doing, simulation verification difficult to achieve function/code coverage, limited small-scale circuits, etc. , to achieve the effect of easy operation, speeding up the practical process, reducing cost and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
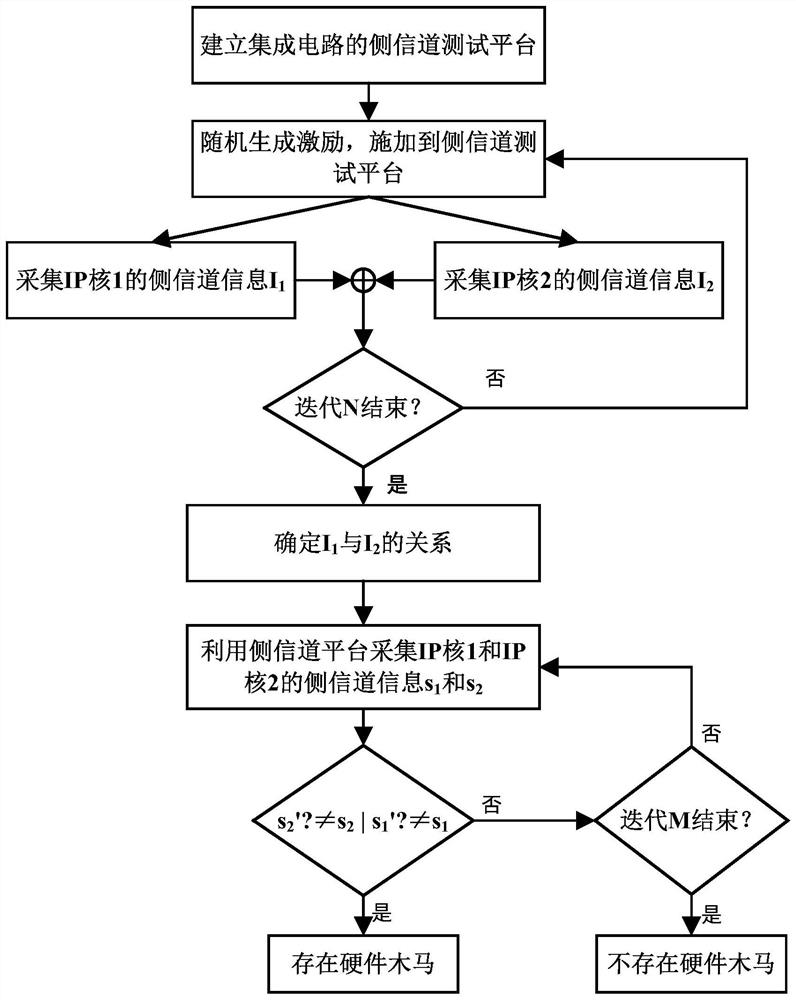
[0027] Aiming at the problem that the coverage rate of simulation verification is difficult to reach 100% and formal verification can only be limited to small-scale circuits, the present invention proposes a method for detecting hardware Trojans using the idea of side channel analysis, and determines the method based on side channel analysis technology The mutual deduction relationship between multiple IP cores, when the side channel information of one of the IP cores is different from the ideal side channel information, it is determined that there is a hardware Trojan horse. This method is not limited by the type of hardware Trojan and the scale of the circuit. It distributes the deduction relationship between multiple IP cores and assists each other in detection, which greatly improves the detection efficiency of hardware Trojan. In addition, the existing detection technology can be transferred to further Improve its detection efficiency, and distributed detection can effec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com