A method for performing security check on a computer terminal
A computer terminal and security inspection technology, which is applied in the field of information security, can solve the problems of high pressure on the server to receive data, the inability to further improve management value, and the unfavorable expansion of security inspection standards, so as to improve real-time performance, participation and real-time performance , Guarantee the effect of configurability and scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
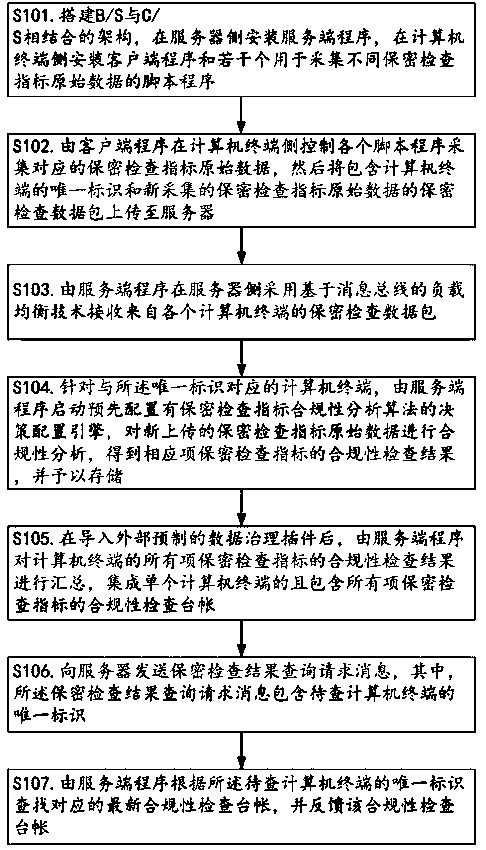
[0050] A method for checking the security of a computer terminal, the specific operation steps are as follows:
[0051] S101. Build a structure combining B / S and C / S, install a server program on the server side, install a client program and multiple script programs for collecting raw data of different security inspection indicators on the computer terminal side;
[0052] S102. The client program controls each script program on the computer terminal side to collect the corresponding original data of the confidentiality inspection index, and then uploads the confidentiality inspection data packet containing the unique identifier of the computer terminal and the newly collected original data of the confidentiality inspection index to the server;
[0053] S103. The server program adopts the message bus-based load balancing technology on the server side to receive the confidentiality inspection data packets from each computer terminal;
[0054] S104. For the computer terminal corre...
Embodiment 2
[0090] Such as figure 1 As shown, the method for checking the security of a computer terminal provided in this embodiment includes the following steps.
[0091] S101. Build a structure combining B / S and C / S, install a server program on the server side, install a client program and multiple script programs for collecting raw data of different security inspection indicators on the computer terminal side.
[0092] In the step S101, the B / S refers to the client / server, the C / S refers to the browser / server, and the original data of the confidentiality inspection index may include, but is not limited to, the device usage code of the computer terminal, Installation location string, MAC address, IP address, hard disk serial number, operating system version number, operating system installation time, operating system log, domain user list, software storage table, running process table, virus database version number of anti-virus software and Operating system patch update time, etc.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com