Method of safety access of power distribution wireless terminal
A wireless terminal, secure access technology, applied in electrical components, transmission systems, etc., can solve the problems of unencrypted communication, plaintext data easily stolen by attackers, lack of anti-replay attack mechanism, etc., to achieve confidentiality and The effect of integrity protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
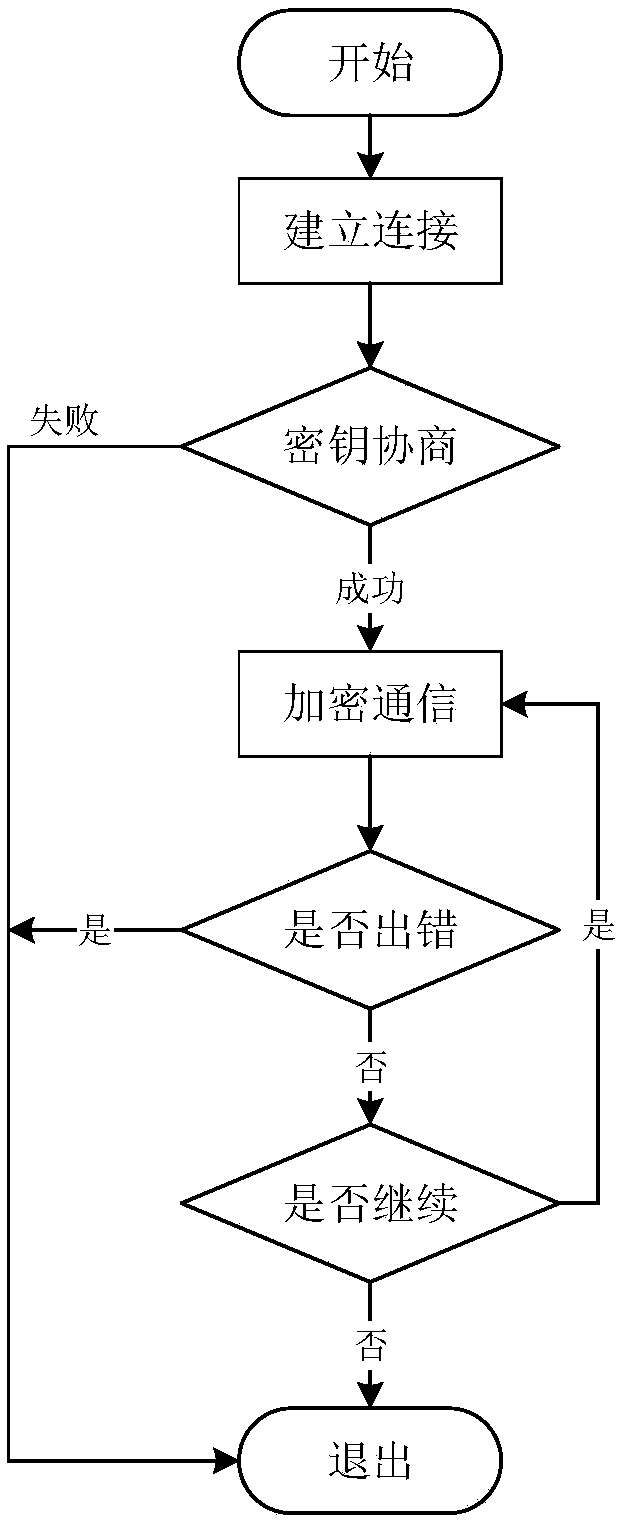
[0036] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
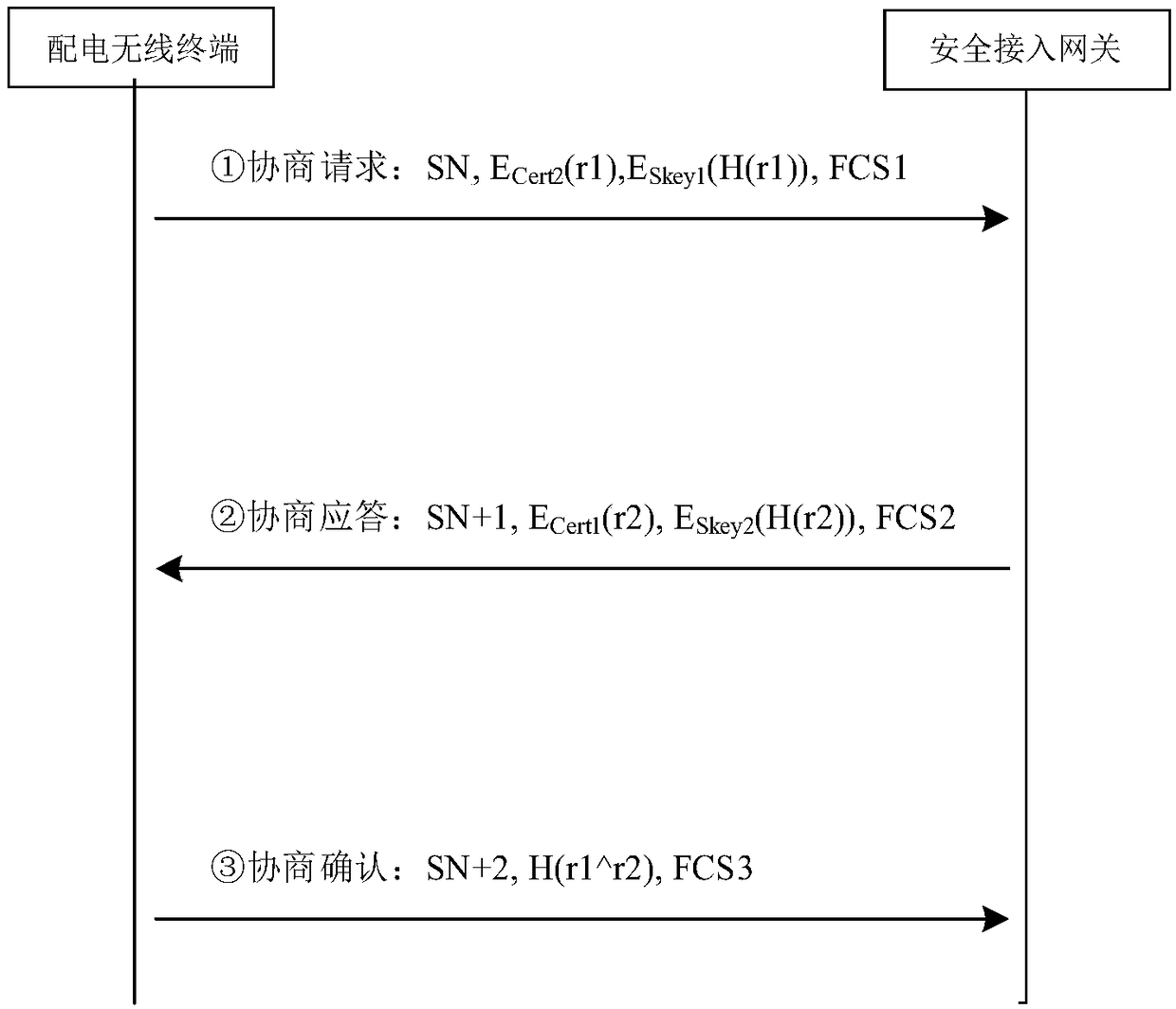
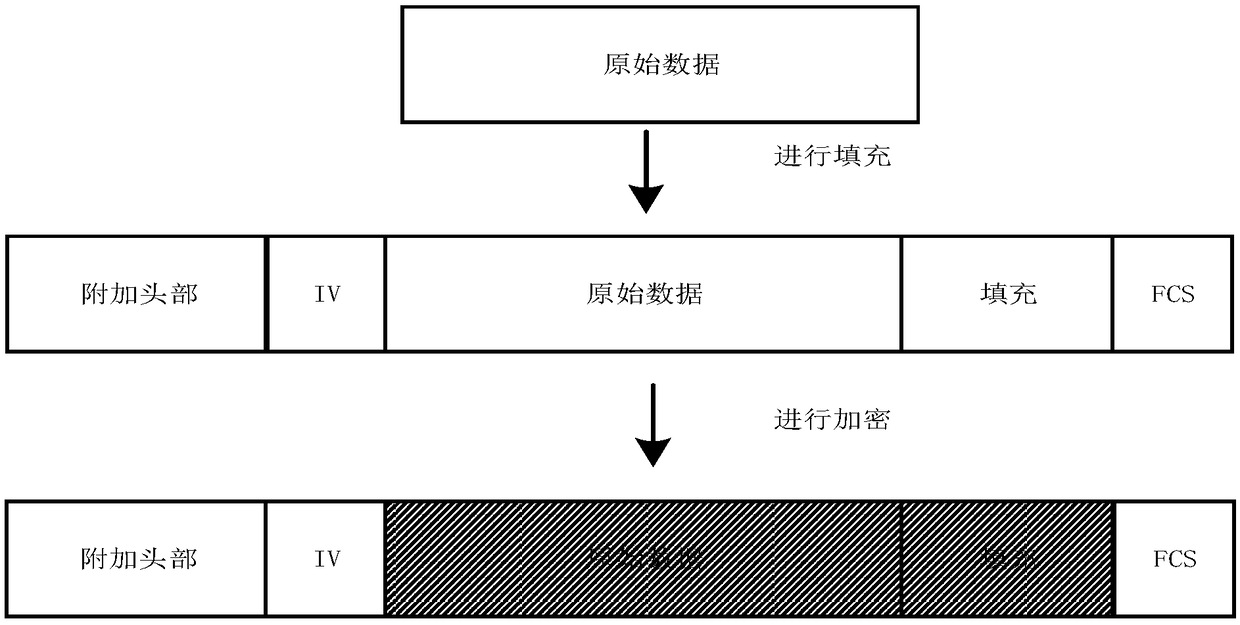
[0037] The invention completes the design of a safe access method for a power distribution wireless terminal based on a domestic commercial encryption algorithm. The power distribution wireless terminal needs to be equipped with an encryption chip, which uses the SPI interface for communication. The encryption chip has a built-in domestic commercial encryption algorithm module and supports SM1 / SM2 / SM3; the security access gateway is equipped with an encryption card, which uses the PCI-E interface for communication. Cipher algorithm SM1 / SM2 / SM3 support.
[0038] The secure access interaction protocol is used for communication between the power distribution wireless terminal and the secure access...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com