Wireless network equipment upgrading program and communication data encryption method
A technology for wireless network equipment and upgrading programs, which is applied in wireless communication, digital data protection, electrical digital data processing, etc. It can solve problems such as failure to achieve encryption, low encryption and decryption efficiency, and abnormal wireless network communication, so as to ensure security Sexuality, avoiding malicious duplication and the effect of copying
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
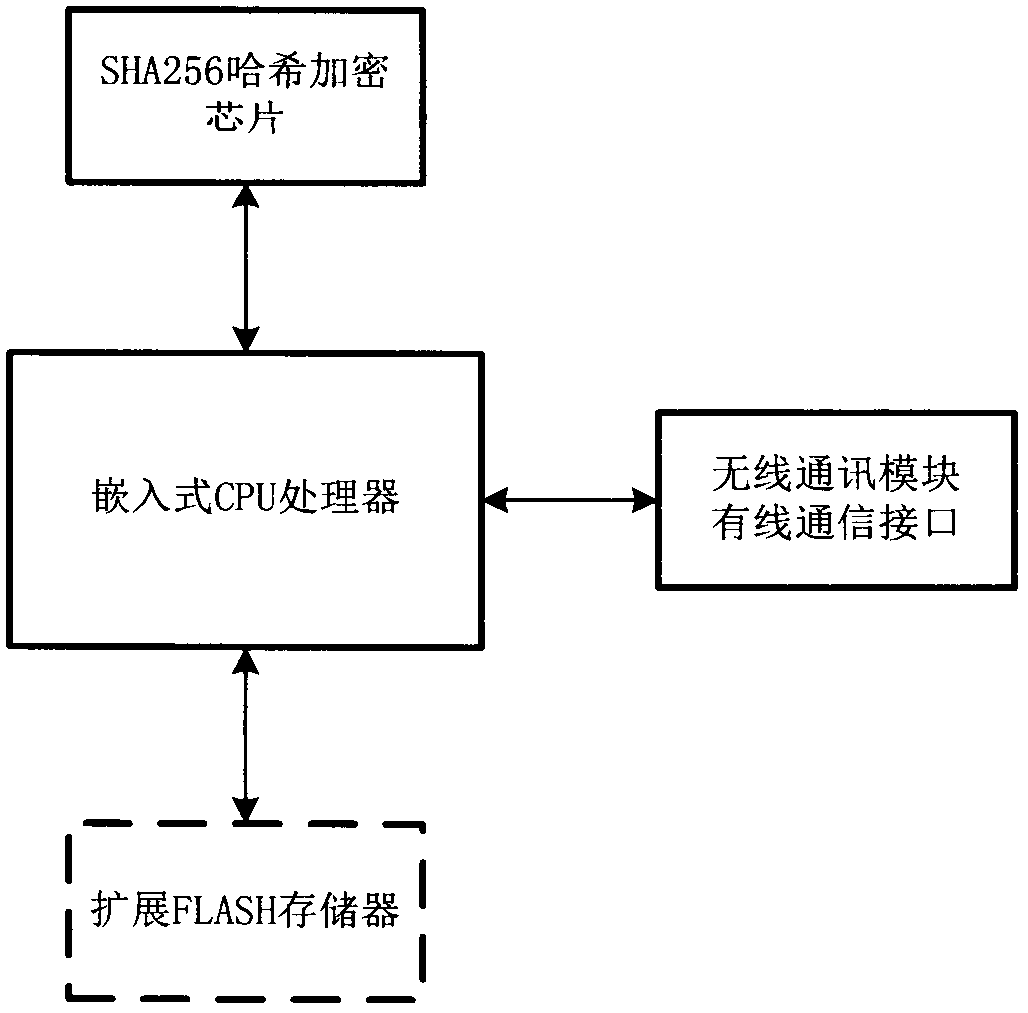
[0121] see Figure 8 , the wireless network device in this embodiment consists of the following parts:
[0122] 1, embedded CPU processor, present embodiment adopts STM32F103RD chip, this chip processor main clock is 72MHz, internal program code FLASH space 384Kbyte; This STM32F103RD CPU processor has internal FLASH read protection mechanism, can guarantee to store in CPU processor The program code in it is not readable by third parties;
[0123] 2, SHA256 encryption chip, present embodiment adopts ATSHA204 encryption chip as SHA256 encryption chip, this encryption chip communicates through I2C bus and CPU processor IO connection, can store 16 encryption keys of 32 bytes, and this encryption chip It also has a read protection mechanism, which can protect 16 encryption keys from being read out;
[0124] 3. Wireless communication interface, this embodiment adopts SI4463 wireless communication module to realize wireless communication of equipment;
[0125] 4. Wired communicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com