A system and method for vulnerability locating and exploring for binary files
A binary file and binary technology, applied in the direction of instrument, program/content distribution protection, platform integrity maintenance, etc., to facilitate analysts, improve vulnerability information, and speed up vulnerability location
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
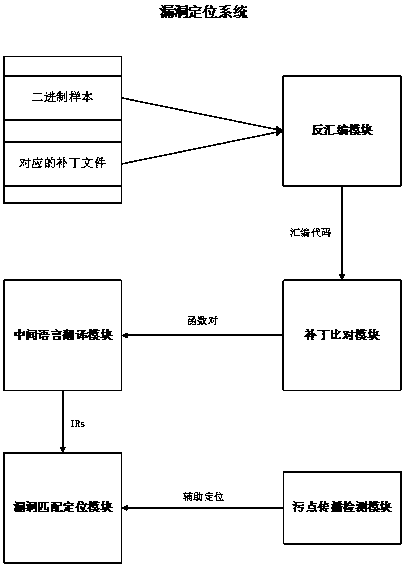
[0045]Patches for Windows, such as MS04-11 LSASRV.DLL binary samples and corresponding patched files. The specific system implementation is as follows:
[0046] A vulnerability location and discovery system for binary files, including:
[0047] Disassembly module: use one of the linear scan algorithm or recursive descent algorithm to disassemble the input MS04-11 LSASRV.DLL binary sample and the corresponding patched file from binary to assembly language respectively to obtain assembly code;
[0048] Patch comparison module: used for function-level fine-grained structural comparison analysis of assembly codes to obtain function pairs that meet the requirements. The structured comparison analysis uses string similarity comparison algorithms, string reference matching algorithms, and the number of instructions Matching algorithm, hash matching algorithm, call-reference matching algorithm, edge matching algorithm, entry-exit matching algorithm and the result of comprehensive co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com