Forensic and traceability method for integrated network attacks, system, equipment and storage media
A technology for network attack and forensics data, applied in the field of network security, can solve problems such as hidden security risks and complicated operations, and achieve the effect of solving cumbersome design and solving problems with hidden security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
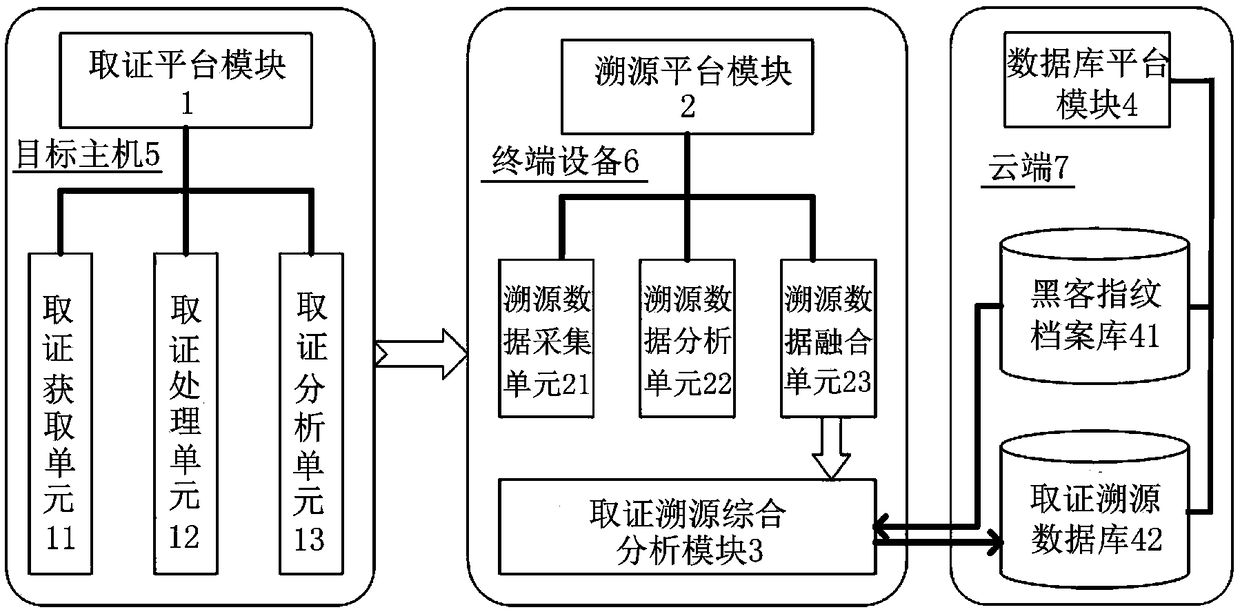
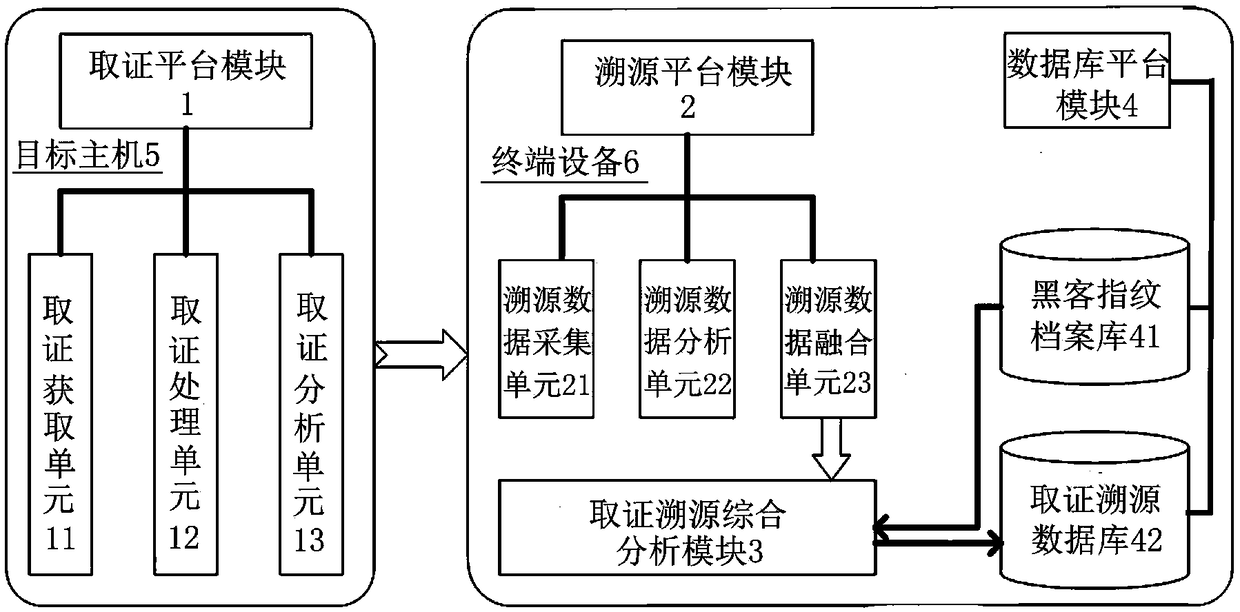
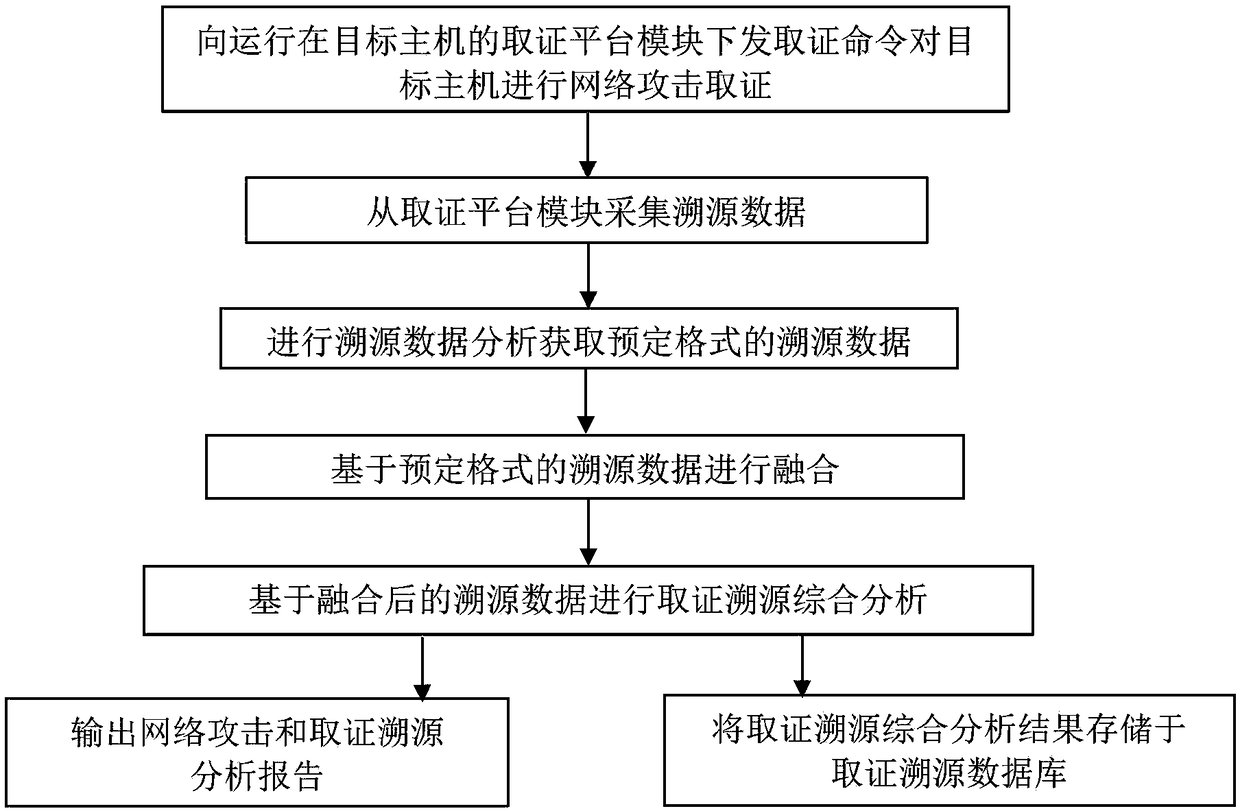
[0028] The embodiment of the present invention provides an integrated network attack forensics traceability system applicable to various application scenarios, which can discover, identify, audit, and trace the abnormal behavior and attack activities of the enterprise network and internal hosts, evaluate the enterprise network security status, clarify potential security threat. First, it has powerful malware identification capabilities, which can help users discover security problems and hidden dangers within the network; second, it solves the detection problem of APT (Advanced Persistent Threat, advanced persistent threat) attacks, and can help enterprises, institutions and countries The security department discovers the attack and traces the source.
[0029] The integrated network attack evidence collection and traceability system has a variety of product forms and supports multiple deployment methods. It can not only meet the needs of enterprise batch collection or normali...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com