A chip security monitoring method and a security monitoring chip
A security monitoring and chip technology, applied in computer security devices, instruments, platform integrity maintenance, etc., can solve the problems of increasing the complexity of chip design and the integrity of verification cannot be guaranteed, and achieve security guarantees and avoid performance problems. The loss, the effect of large inclusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
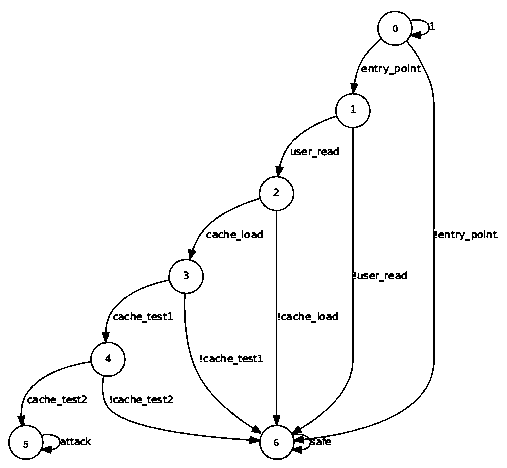
[0048] Embodiment 1 provides a chip security monitoring method. This embodiment includes the monitoring of known attack modes, and also covers unknown attack modes that can be ruled out. Specifically, this method includes the following steps:
[0049] A monitor embedded in the chip monitors the operation of the chip;
[0050] Wherein, the monitor includes a first state machine and / or a second state machine, the first state machine is corresponding to a model established by a known chip attack, and the second state machine is obtained by The security rules / security properties described by the assertion are transformed.
[0051] Wherein, in this embodiment, the function of the monitor is to give an alarm or interrupt the operation of the chip when the chip is attacked, so as to prevent confidential information from being leaked or tampered with.
[0052] The state machine model of the monitor is built into the chip as part of the chip design and tapeout.
[0053] There are tw...
Embodiment 2
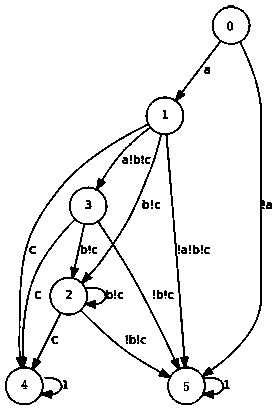
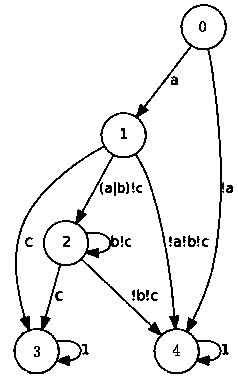
[0087] This embodiment provides a security monitoring chip. This embodiment has the same inventive concept as Embodiment 1, specifically, as image 3 As shown, the chips include:
[0088] chip body;
[0089] and a monitor embedded in the chip body, the monitor monitors the operation of the chip body;
[0090] Wherein, the monitor includes a first state machine and / or a second state machine, the first state machine is corresponding to a model established by a known chip attack, and the second state machine is obtained by The security rules / security properties described by the assertion are transformed.
[0091] Among them, such as image 3 As shown, the number of monitors is n.
[0092] More preferably, in this embodiment, the monitor includes an initial state and at least one tracking state, and the tracking state includes at least one error reporting state;
[0093] The monitoring of the operation of the chip body includes:
[0094] The monitor makes a judgment on the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com