Nonlinear double-image encryption method based on chaos and amplitude-phase encoding
An encryption method and dual-image technology, which can be applied to secure communication through chaotic signals, image communication, digital transmission systems, etc., can solve the imbalance of amplitude encryption and phase encryption image histogram, the ability to resist statistical attacks is weak, and the encrypted image is unbalanced. Problems such as uneven distribution of histograms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
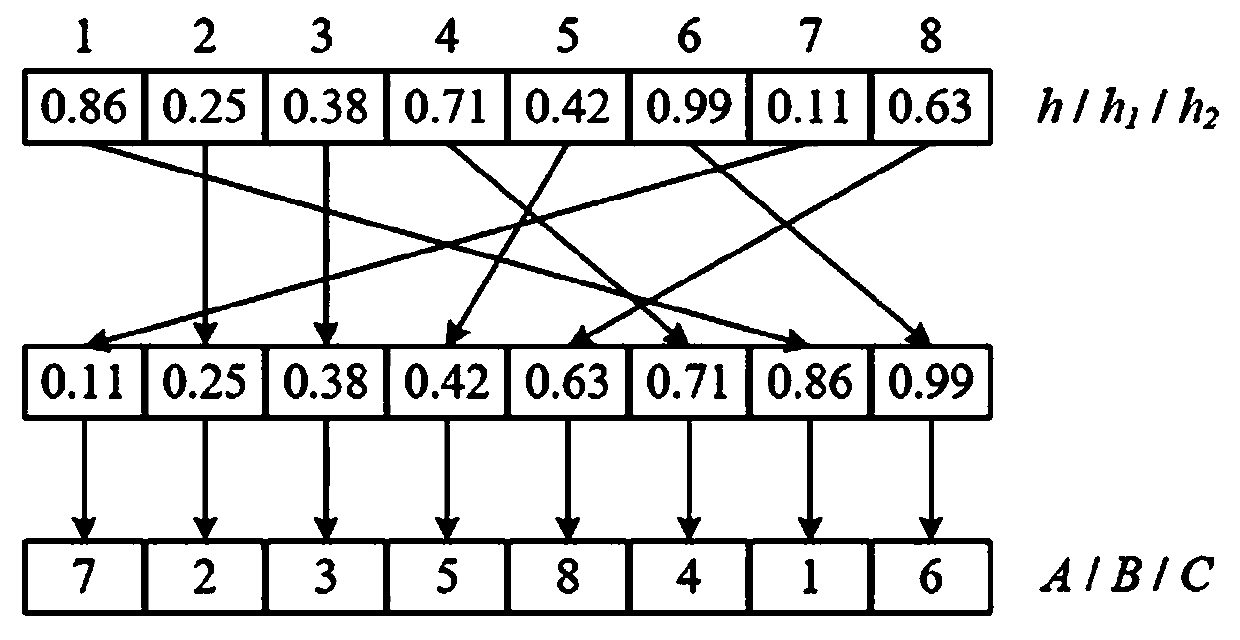
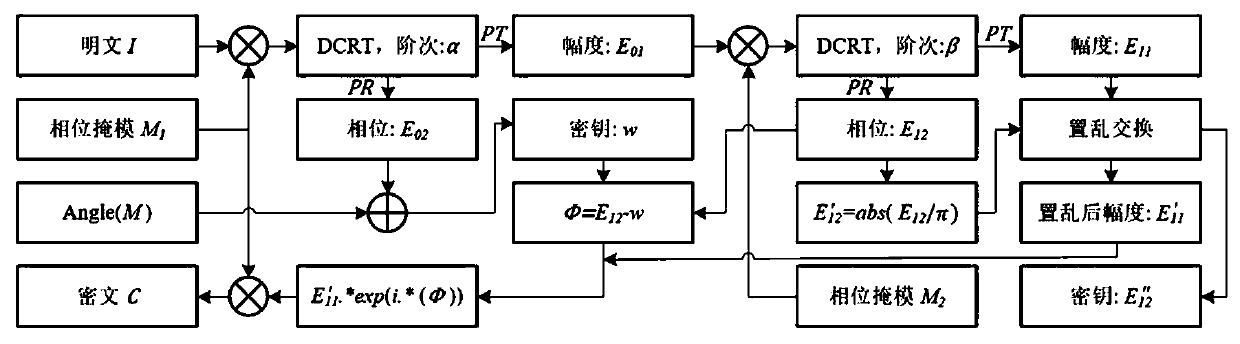
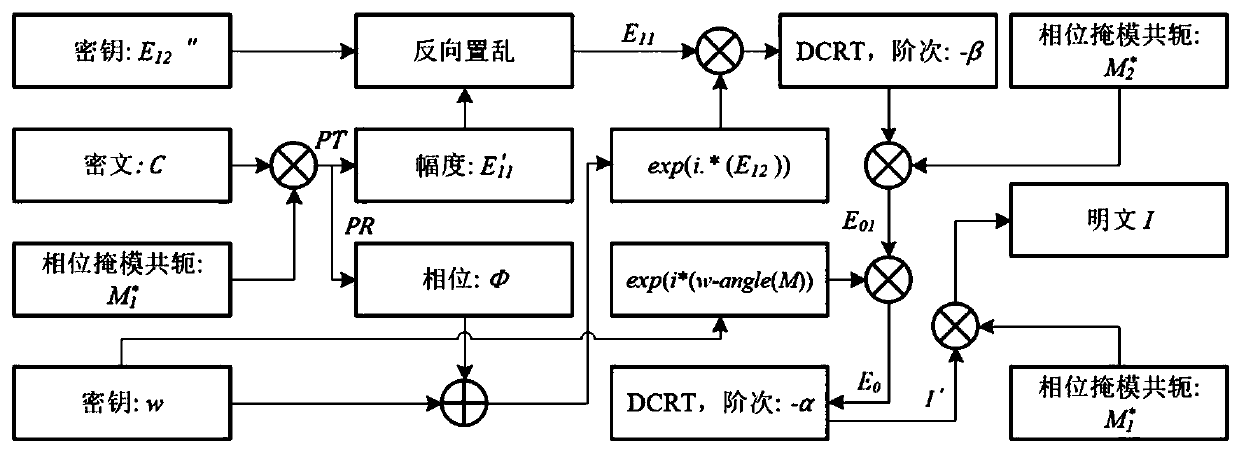
[0097] 1) Generate chaotic sequence and phase mask: Two chaotic systems are used to generate the phase mask M 1 and M 2 , 2D Logistic mapping is used to generate a random kernel matrix of discrete complex order random transformation, as follows:
[0098] ① First, set the adaptive adjustment parameters, apply the adaptive adjustment parameters to adjust the initial value of the chaotic system, and generate the corresponding chaotic sequence, assuming that the plaintext image is expressed as I 1 , I 2 , the size of the plaintext image is N×N, then the generation of adaptive adjustment parameters is shown in formula (1):
[0099]
[0100] where σ ad_init is the initial value of the Chen system, ranging from 0 to 1, which can be understood as the initial value x 0 ,y 0 ,z 0 = σ ad_init , the value range of the 2D Logistic random matrix is small, and the initial value of the 2D Logistic mapping system satisfies formula (2) and formula (3):
[0101] x' 0 =a+0.01σ ad_i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com