Lightweight authentication equipment and an authentication method based on a feedback loop PUF
A lightweight authentication and feedback loop technology, applied in the field of PUF authentication, can solve problems such as the infeasibility of large-scale edge devices, and achieve the effect of improving flexibility and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
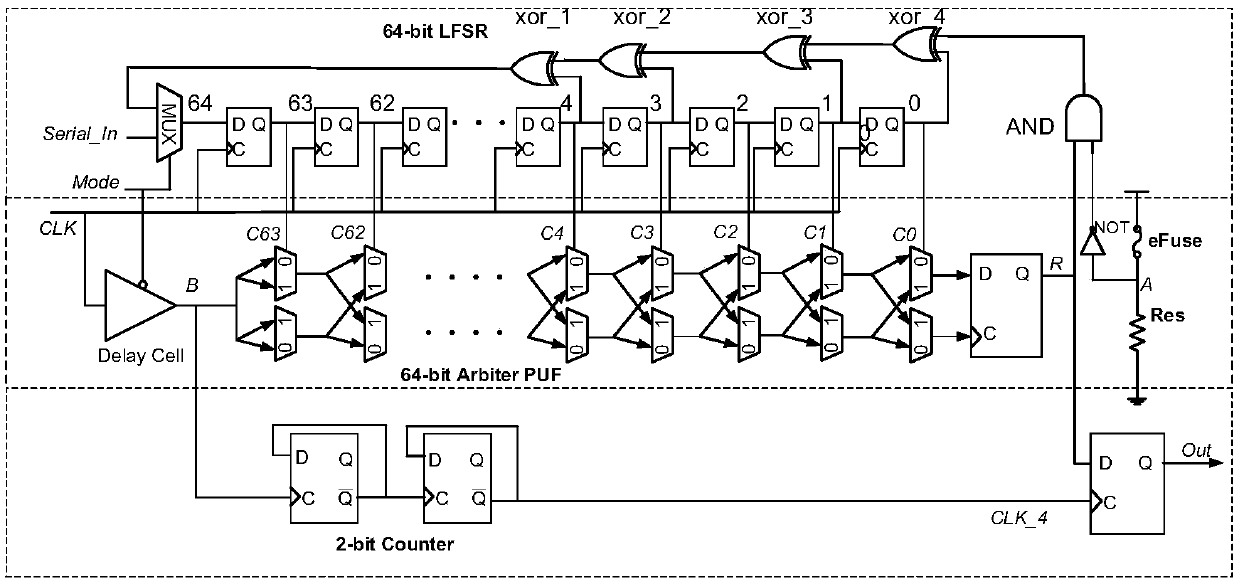
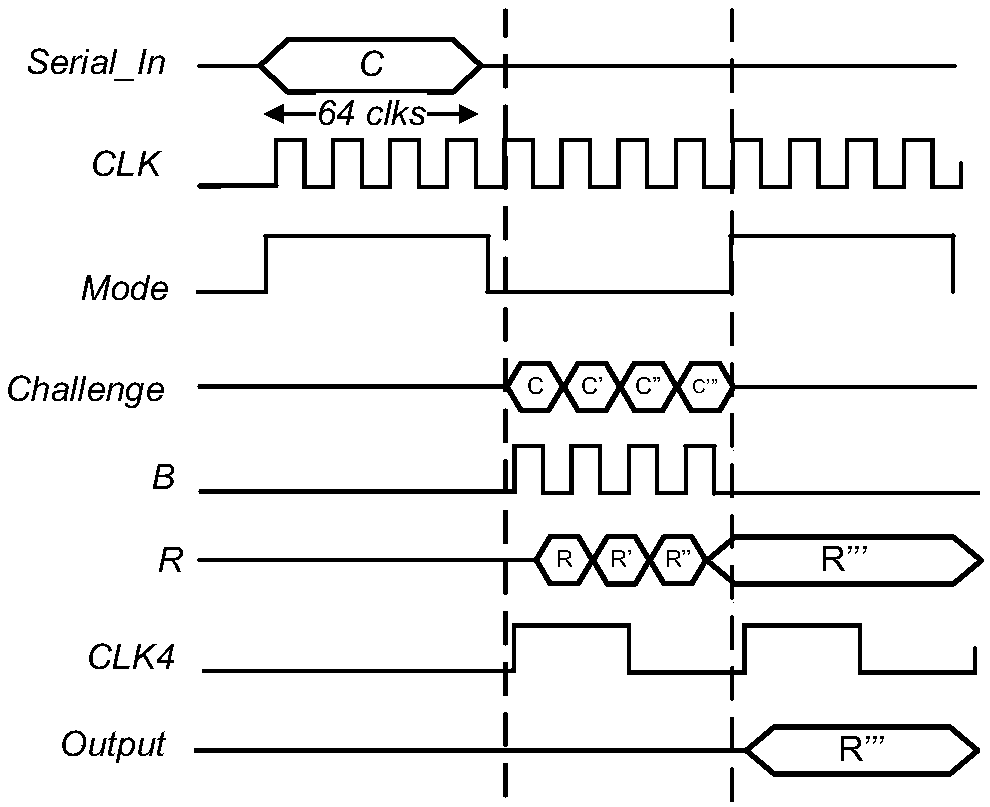
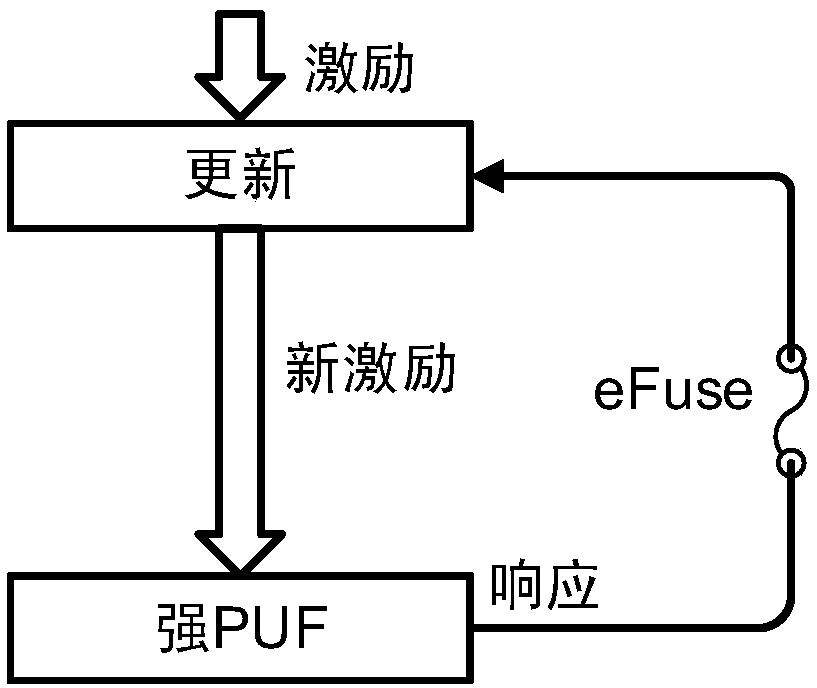
[0071] The lightweight authentication device based on the feedback loop PUF in the embodiment of the present invention has a circuit structure as figure 1 As shown, N takes 64, M takes 2, and K takes 4, which includes a 64-bit linear feedback shift register module (64-bit LFSR), a 64-bit arbiter PUF module (64-bit Arbiter PUF), and a 2-bit counter module (2-bit Counter), eFuse-based feedback network module and output D flip-flop module, in which the 64-bit linear feedback shift register module (64-bit LFSR) contains 4 XOR gates.
[0072] 64-bit linear feedback shift register module, including a 2-to-1 data selector MUX, 64 D flip-flops (the 0th, 1st...63rd D flip-flops from right to left) and 4 XOR gates (Denoted as xor_1, xor_2, xor_3, xor_4). The two input terminals of the 2-to-1 data selector are respectively connected to the input signal (Serial_in) and the output terminal of the XOR gate xor_1, the selection control terminal is connected to the control signal Mode, and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com