Underwater wireless sensor network coverage vulnerability repair algorithm based on cluster partitioning
A vulnerability repair and coverage technology, applied in network planning, network topology, wireless communication, etc., can solve the problems of limited node energy, difficult to replace batteries, network paralysis, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] Step 1: Use the topological model of the 3D dense network to divide the entire 3D space into multiple identical virtual components, and ensure that there is a sensor node that can work normally in each segmented unit, and it can be determined that the entire sensor network is highly covered of.
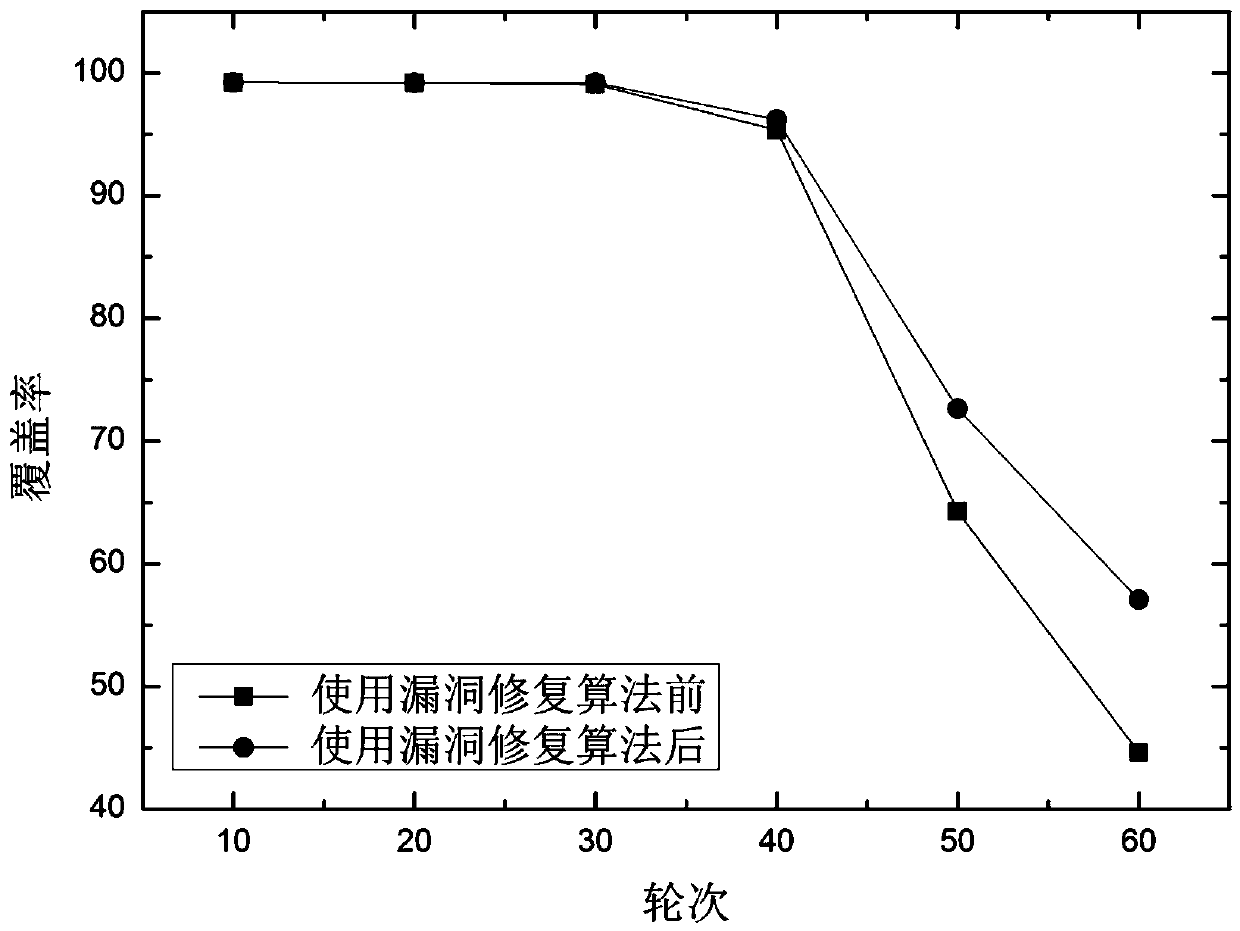
[0075] Step 2: Vulnerability detection. Make relevant definitions and establish a mapping between segmentation units and coverage matrices to find failure nodes in some segmentation units that appear, assuming that coverage holes may appear in the cluster, and then divide the center of the unit according to the relationship between the perceived radius of the vulnerability edge node and the distance The length determines whether there is really a coverage hole;
[0076] Step 2.1: Relevant Definitions
[0077] Definition 1: Coverage C r : The coverage of the sensor network refers to the sensing range V of sensor nodes 1 ,V 2 ,...,V n The intersection of and the monitoring ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com