A safe pair index construction and retrieval method capable of resisting keyword privacy disclosure
A keyword pair and construction method technology, applied in the direction of digital data protection, etc., can solve problems such as security restrictions, inability to prevent attacker keyword information, disclosure of keyword privacy, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
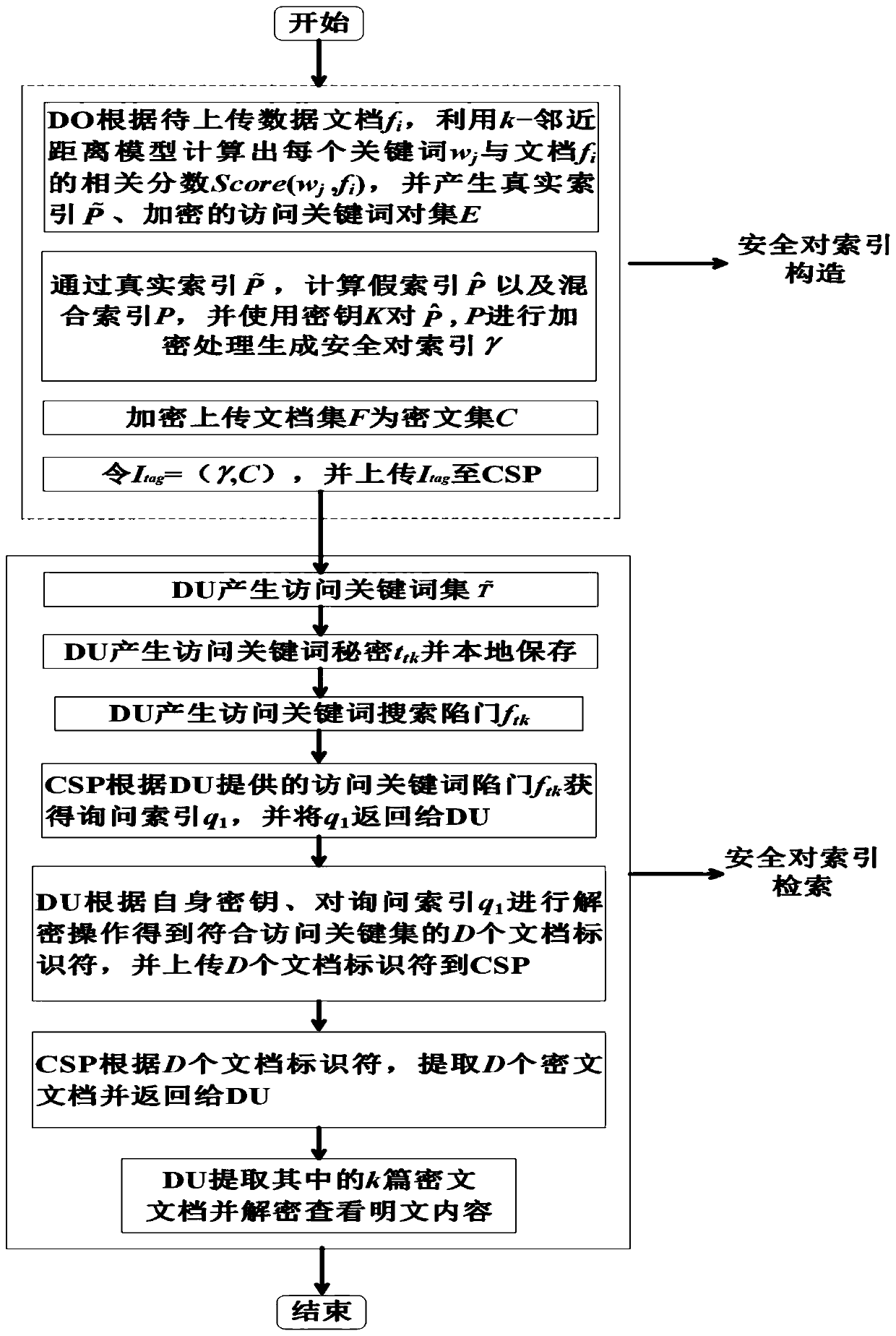
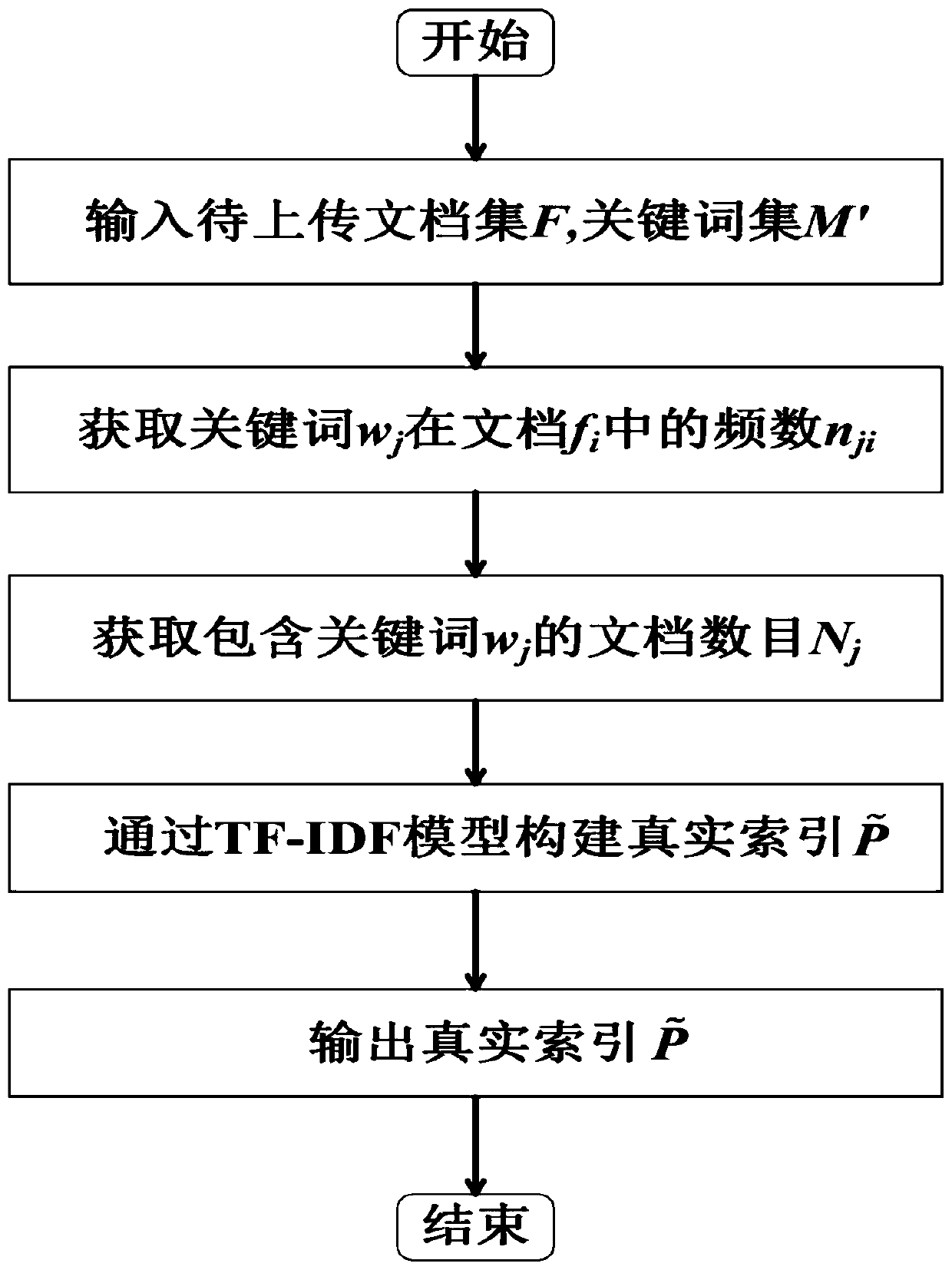
[0097] Before describing the method of present embodiment in detail, earlier the design concept of this method is described as follows:
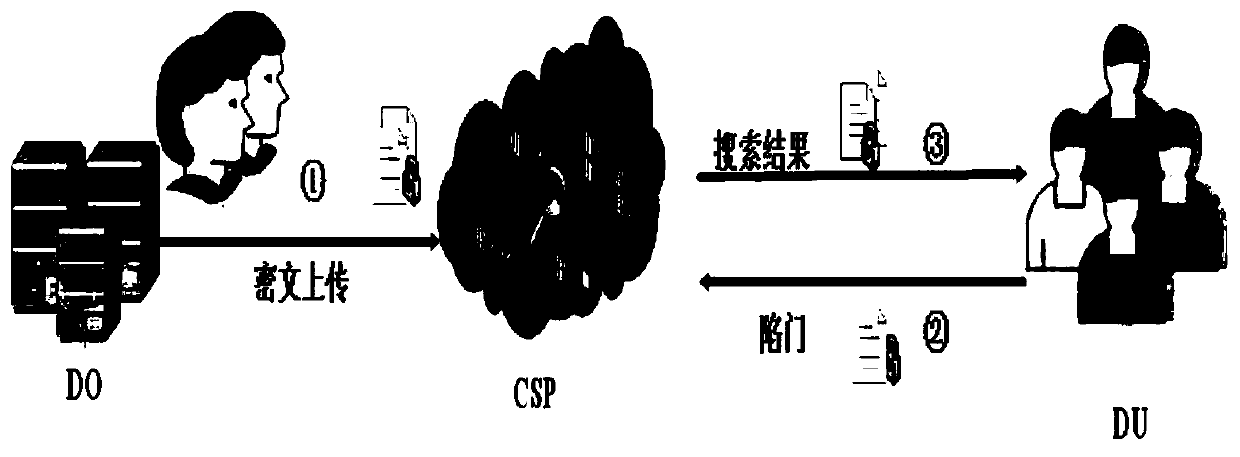
[0098] The system model designed by the present invention includes two types of users and cloud servers, one is the data owner (dataowner, DO) responsible for uploading shared data; the other is the data user (data user, DU), which is mainly reflected in the query The data to be queried, and the information you want to know; the server is a cloud service provider (cloud service provider, CSP), responsible for storing data for the data owner DO and retrieving data for the legitimate user DU. The relationship between the three parties is as figure 2 Shown:
[0099] Both the data owner DO and the legal user DU need to authenticate their identities in a trusted authentication center, and obtain authorization values from the trusted authentication center. For the relevant key K and the document decryption key, DO only needs to share the colu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com