Recommendation method based on label and differential privacy protection
A differential privacy and recommendation method technology, applied in digital data protection, special data processing applications, instruments, etc., can solve the problems of privacy definition, large encryption algorithm size, user privacy leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
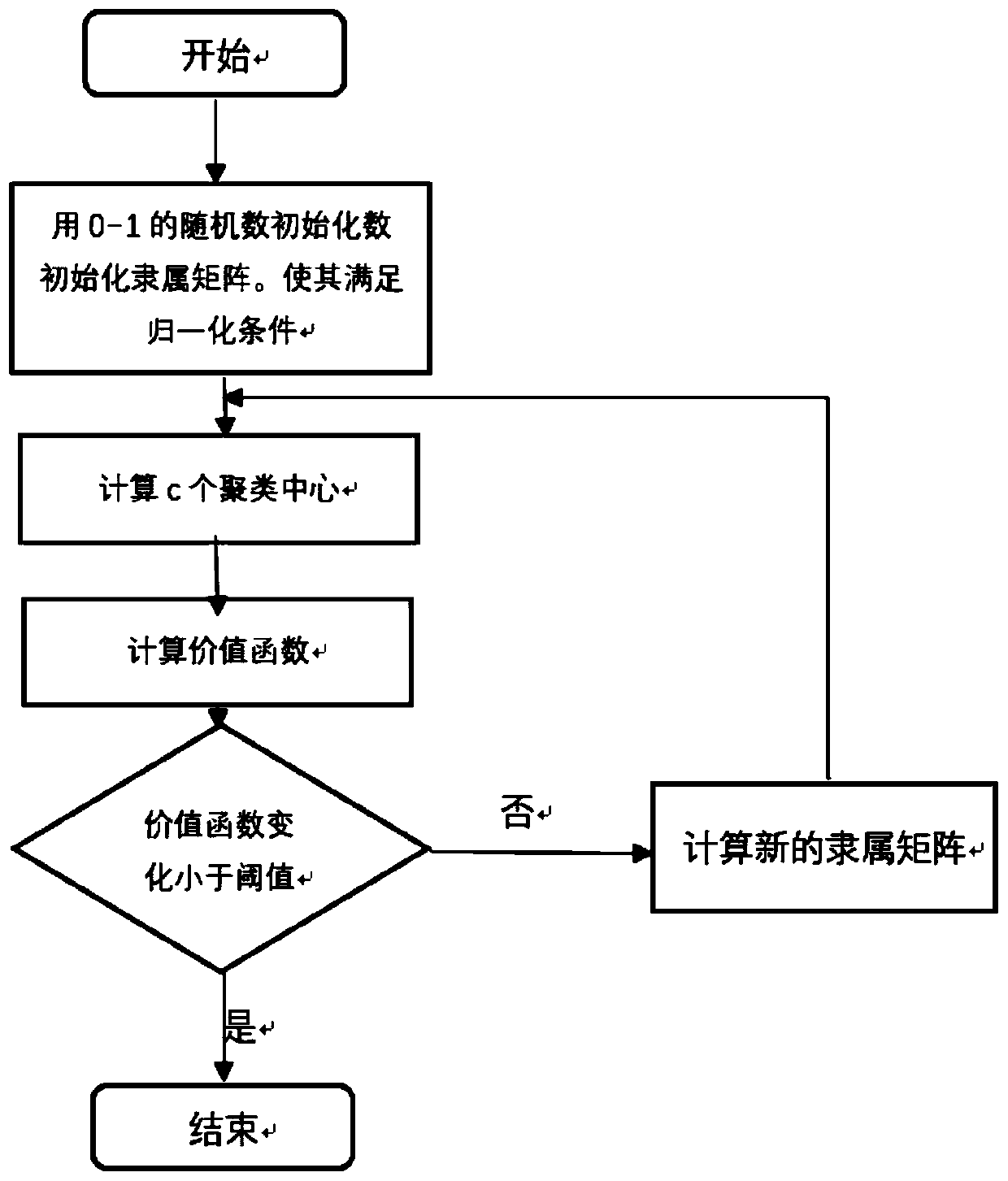
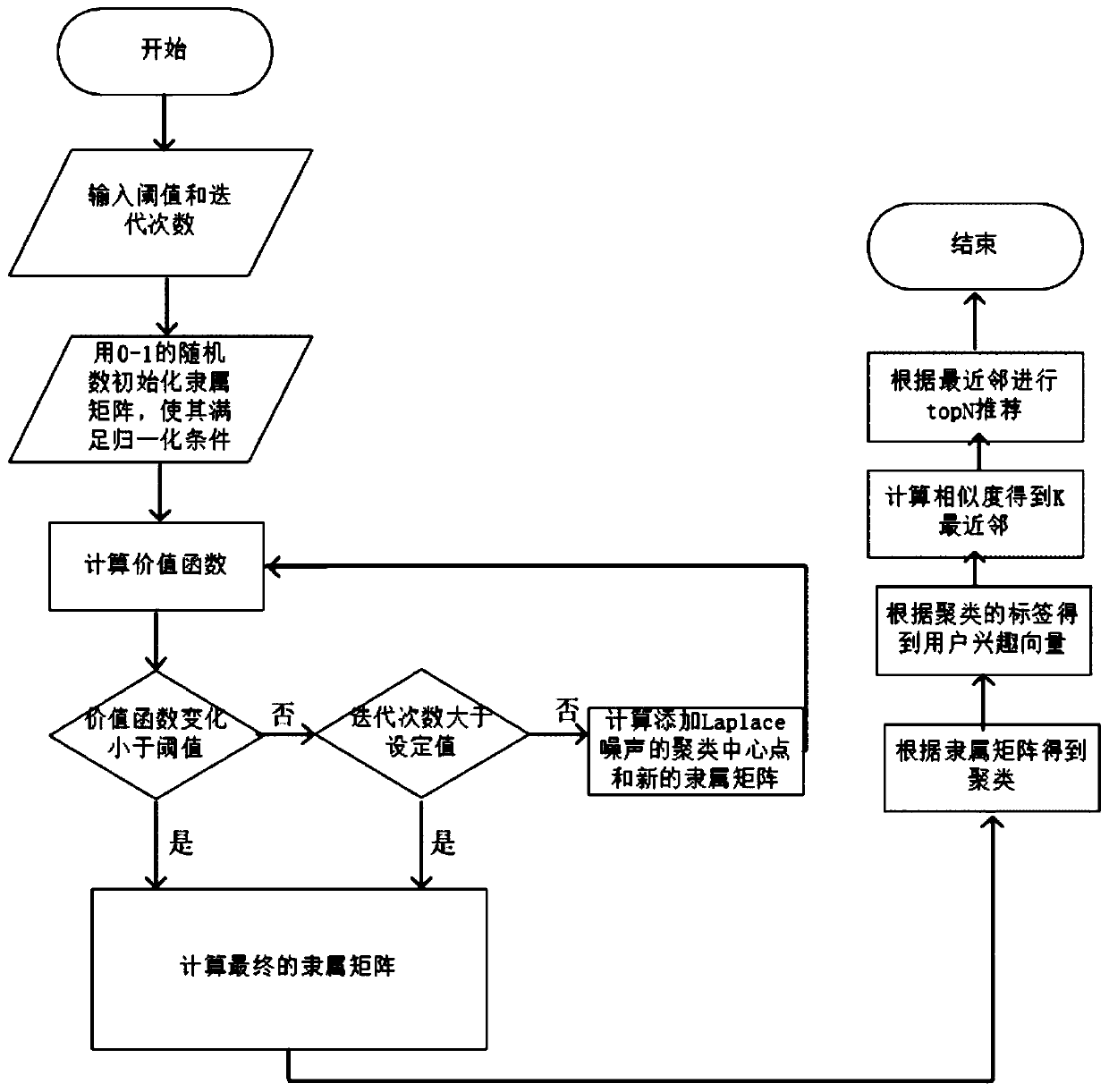
[0025] The present invention mainly proposes a recommendation method based on tags and differential privacy protection, and the concepts used in the present invention are as follows.
[0026] 1. Collaborative labeling system
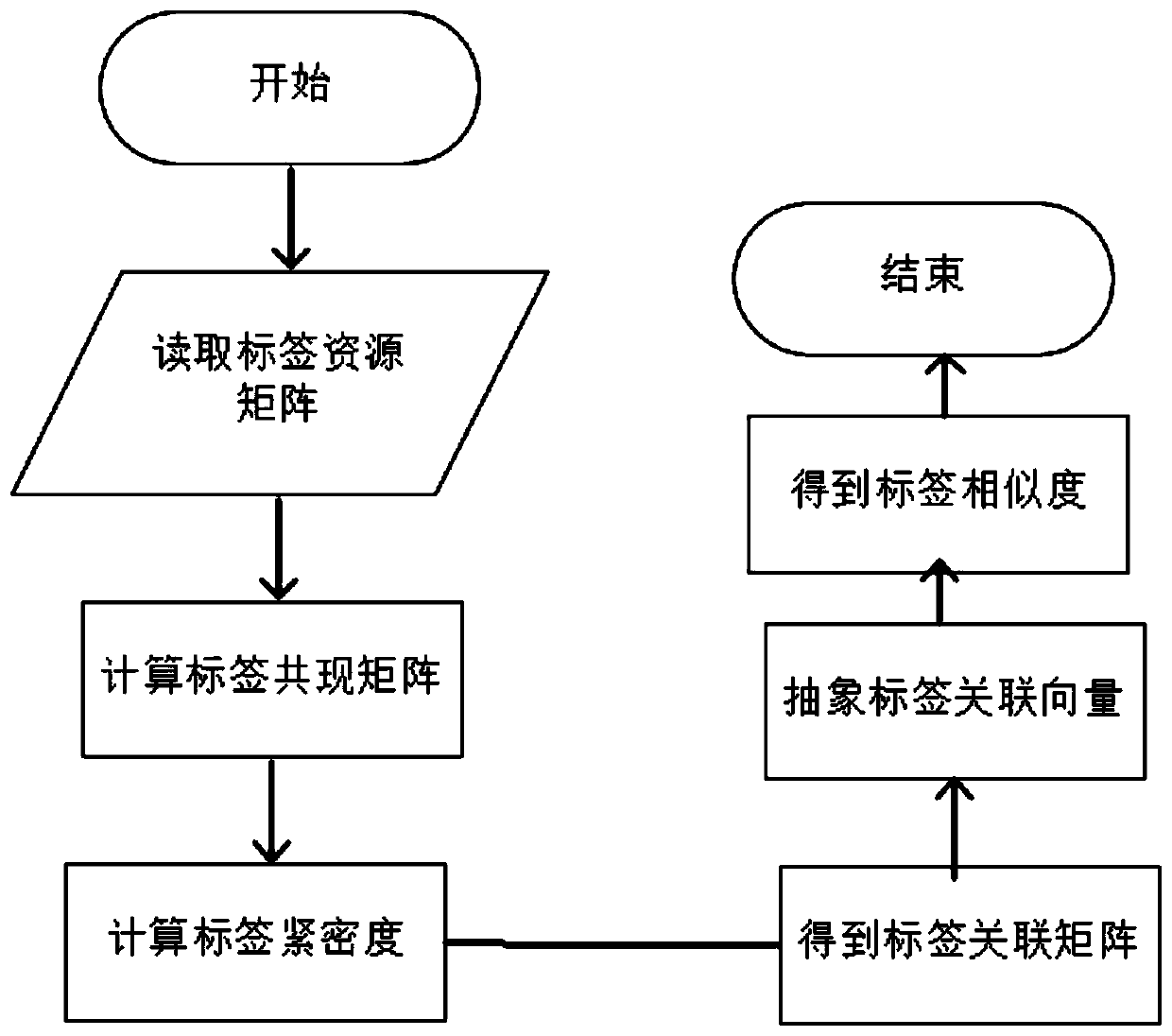
[0027] Conceptually, the collaborative labeling system can be abstractly expressed as a triplet model, which is mainly composed of three entities: user, tag, and resource; here, the three entities of user, tag, and resource can be regarded as three independent sets , the elements in each set can be regarded as a point, and these points are connected respectively. A user's marking action can be regarded as a path connecting the elements in the user collection, label collection and resource collection with two edges. It can be seen that the label is a bridge connecting users and resources.
[0028] Tags are marked for resources by users, and with the help of the semantic characteristics of the tag itself, it can provide us with more information for analys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com