An internal attack detection method based on a weighting rule and consistency in a CPS system
An internal attack and detection method technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as rough methods, not practical enough, and insufficient consideration of the closed-loop structure of the CPS system control system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
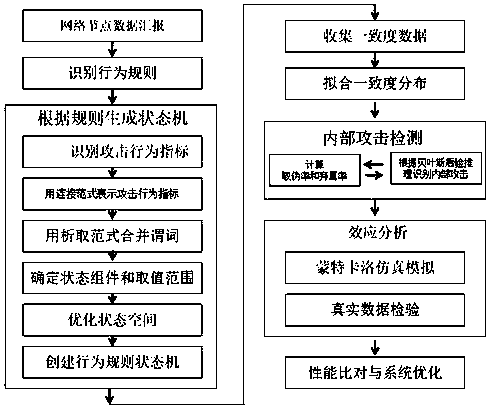
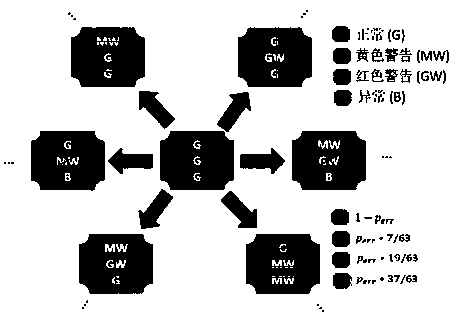
[0086] The present invention will be further described in detail below in conjunction with the accompanying drawings, and specific implementation methods will be given.
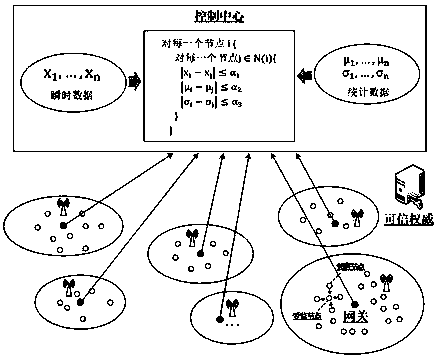
[0087] The present invention is based on a typical CPS system application scenario, and the overall structure of the system is as follows figure 1 As shown, it includes the following four participants: (1) Trusted authority: responsible for managing the entire system, and no longer participates in subsequent specific operations after system initialization; (2) Control center: responsible for collecting and integrating the global data of the system, and Centralized monitoring, analysis and decision-making of system operation status; (3) Gateway: responsible for aggregating the data of each autonomous area network node of the CPS system, and forwarding the report data of each node to the control center; (4) Network node: CPS system There are a total of n nodes at the sensing end N={N 1 ,N 2 ,...,N n} (or use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com