A block chain consensus method based on credibility evaluation
A blockchain and trustworthy technology, applied in encryption devices with shift registers/memory, user identity/authority verification, payment systems, etc., and can solve problems such as weak asymmetric encryption algorithms, ByzCoin consensus attacks, attacks, etc. , to achieve the effect of improving transaction throughput, ensuring randomness, and ensuring fairness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0015] Concept introduction:
[0016] System round time: the time from one leader to the next.
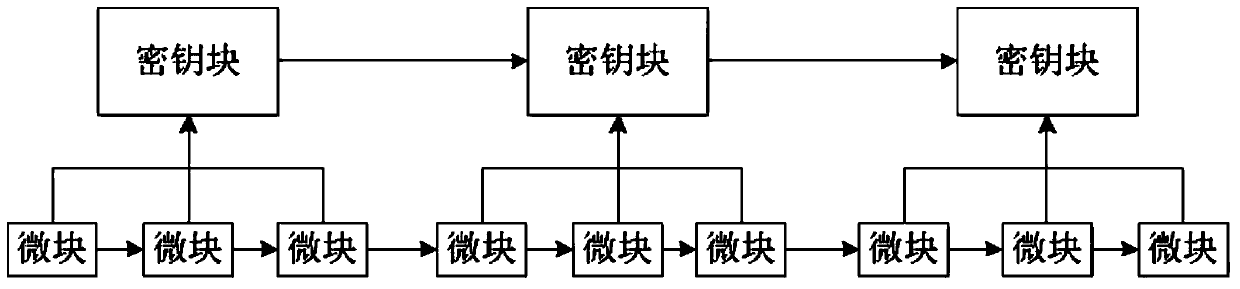
[0017] Key block: The key block is used to determine the leader and mine using the POW consensus mechanism. In a secret key block, Prev keyblock hash is the hash value of the previous key block, Nonce is a random number, PK is the public key of the miner, R is the trust value, K sig is Prev keyblock hash, Nonce, PK, R The hash value of , Sig keyblock agreement is the consensus-verified signature of this key block. Consensus group members verify the key block by checking the validity of K sig.
[0018] Microblock: A microblock is a simple block that is verified every few seconds. Microblocks include verified historical transactions. To prevent double spending, each microblock is proposed to the consensus group before being accepted, and if the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com