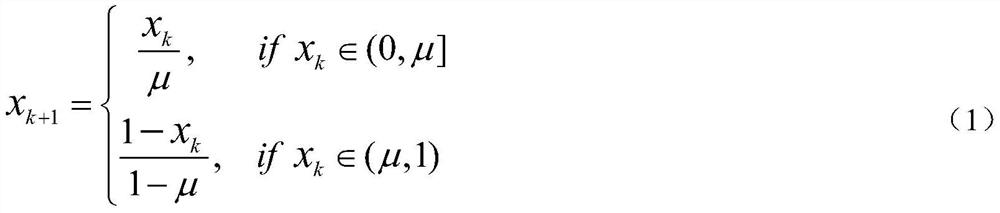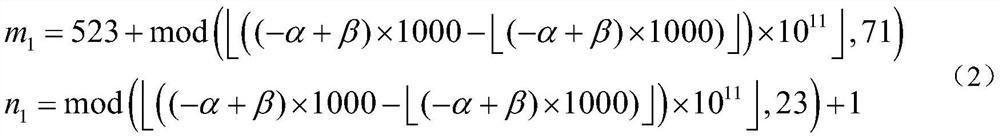A String Encryption and Decryption Method
An encryption method and string technology, applied in the field of information security, can solve problems such as complex encryption operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
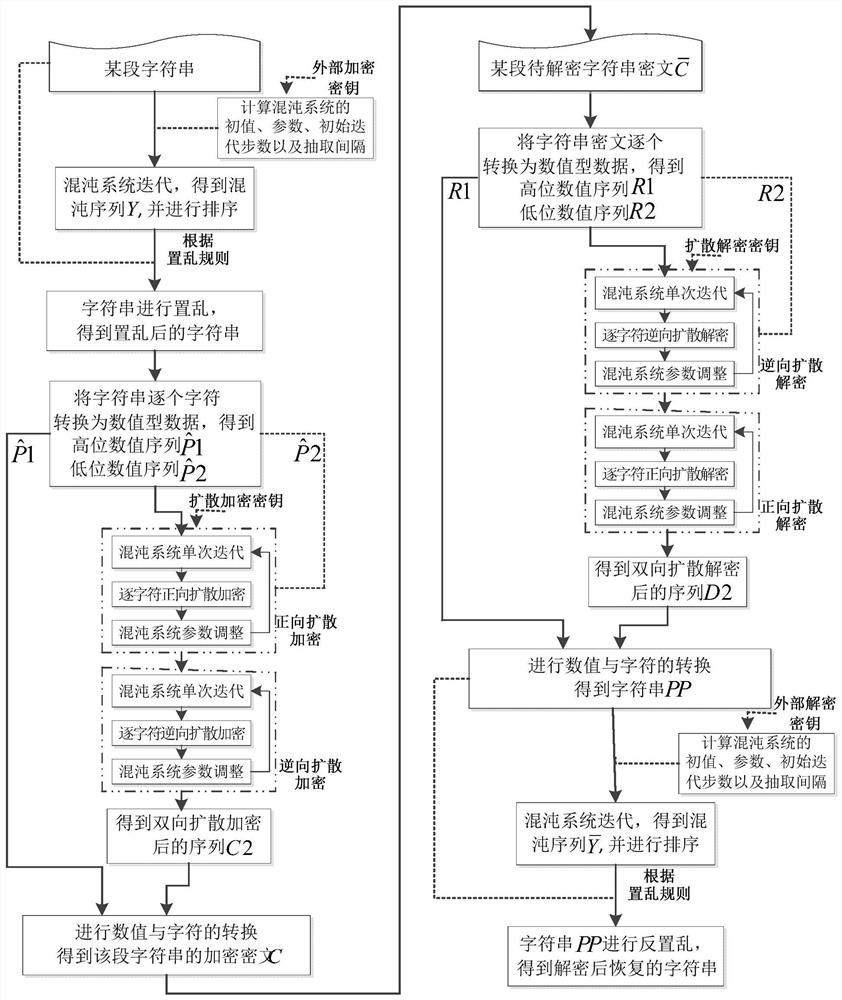
[0191] According to the encryption method of a kind of character string in the above-mentioned specific embodiment, the steps are as follows:
[0192] (1) First utilize the external encryption key (α=0.12345, β=0.65) to iterate the tilted tent chaotic system shown in the formula in step (1) of a kind of character string encryption method in the above-mentioned specific embodiment, obtain chaos Sequence X, calculate according to the formula in the encryption method step (1) of a kind of character string in the above-mentioned specific embodiment simultaneously, obtain the initial iterative steps of chaotic system (m 1 ) and sampling interval (n 1 ),
[0193] m 1 =523+23=546
[0194] no 1 =19+1=20
[0195] 从混沌序列X中第546个元素开始每隔20个元素取1个,从而形成长度为L=18的混沌序列Y={0.361896018751758,0.707665360260700,0.416287938280632,0.569011637774278,0.276890527259342,0.467623413399187,0.989176495851167,0.169240171895533,0.675028025531495, 0.458815246880602,0.612489131368256,0.174072241734472,0.580925...
Embodiment 2
[0228] According to the above-mentioned method for encrypting a character string, a certain character string to be encrypted is "encryption and decryption of a character string 111111aaaaaa", the encryption steps of a character string are similar to those in Embodiment 1, and only the encryption key changes slightly: α=0.12345000000001 ; or β=0.65000000000001; or Y1 0 =45; or C1 0 =27; or Y2 0 =55; or C2 0 =37, the string encryption result is shown in Table 1. It can be seen from Table 1 that a slight change in the encryption key will cause a large change in the encrypted ciphertext of the string, so it can be seen that a string encryption method proposed in this patent is sensitive to the encryption key.
[0229] Table 1 When the external encryption key changes slightly, the result of string encryption
[0230]
[0231]
Embodiment 3
[0233] According to the above-mentioned encryption method of a character string, its encryption steps are similar to the specific embodiment 1, and only a certain section of the character string to be encrypted ("encryption and decryption of character strings 111111aaaaaa") has a slight change: "encryption and decryption of subcharacter strings 111111aaaaaa"; or "String encryption and decryption 111111aaaaaa"; or "string encryption and decryption 211111aaaaaa"; or "string encryption and decryption 111112aaaaaa"; or "string encryption and decryption 111111baaaaa"; or "string encryption and decryption 111111aaaaaab", the string encryption result is as follows Table 2 shows. It can be seen from Table 2 that slight changes in the plaintext information of the string to be encrypted will cause the encrypted ciphertext to be "unrecognizable". It can be seen that the string encryption method proposed in this patent is sensitive to the plaintext information of the encrypted string.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com