Safe password chip testability design structure in boundary scanning design environment
A technology of boundary scan and design structure, which is applied to secure communication devices and key distribution, can solve the problems of not finding patented inventions of cryptographic chips, etc., and achieve the effect of low area cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in detail below in conjunction with the drawings.
[0027] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the following further describes the present invention in detail with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, but not to limit the present invention.
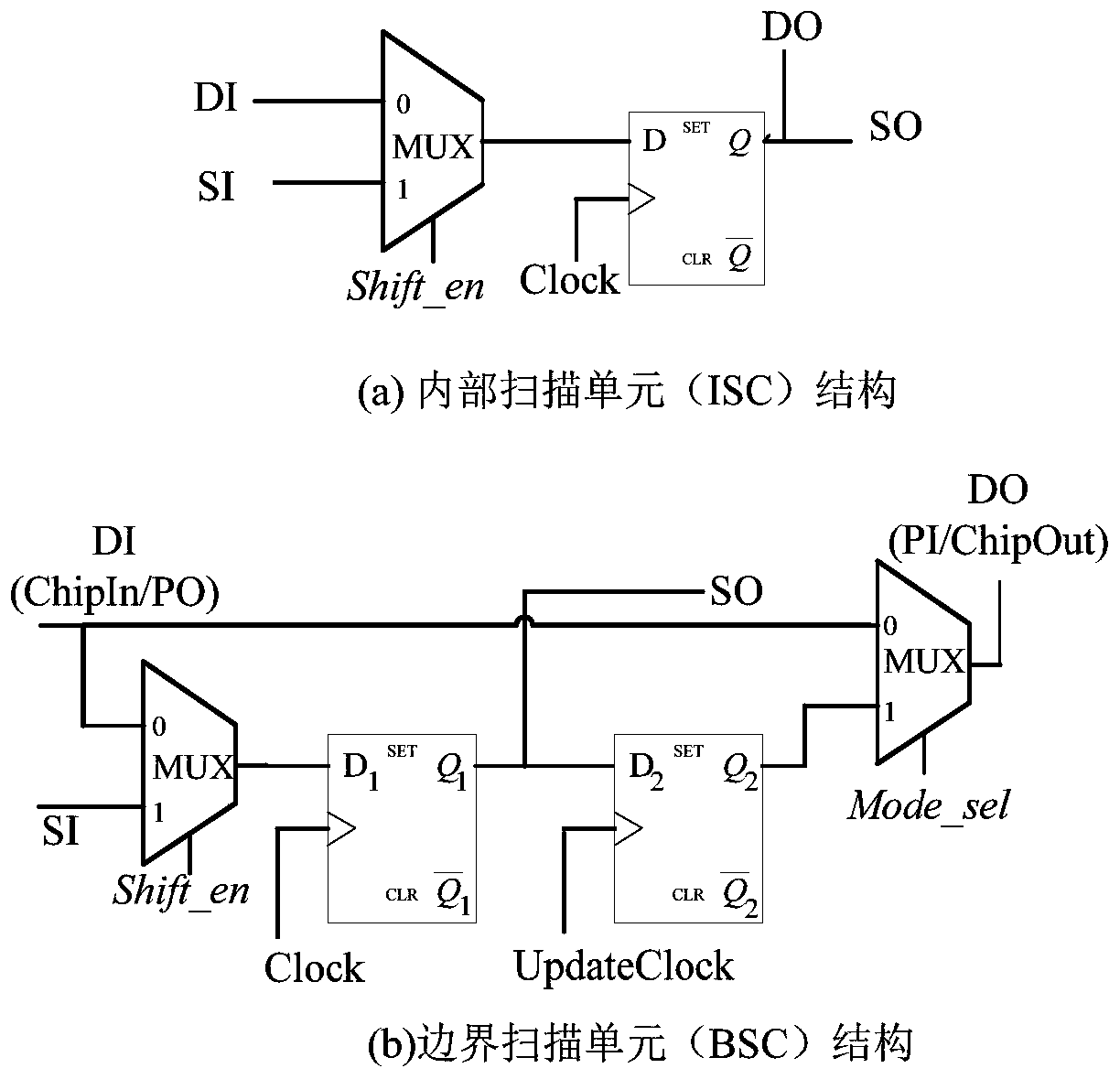
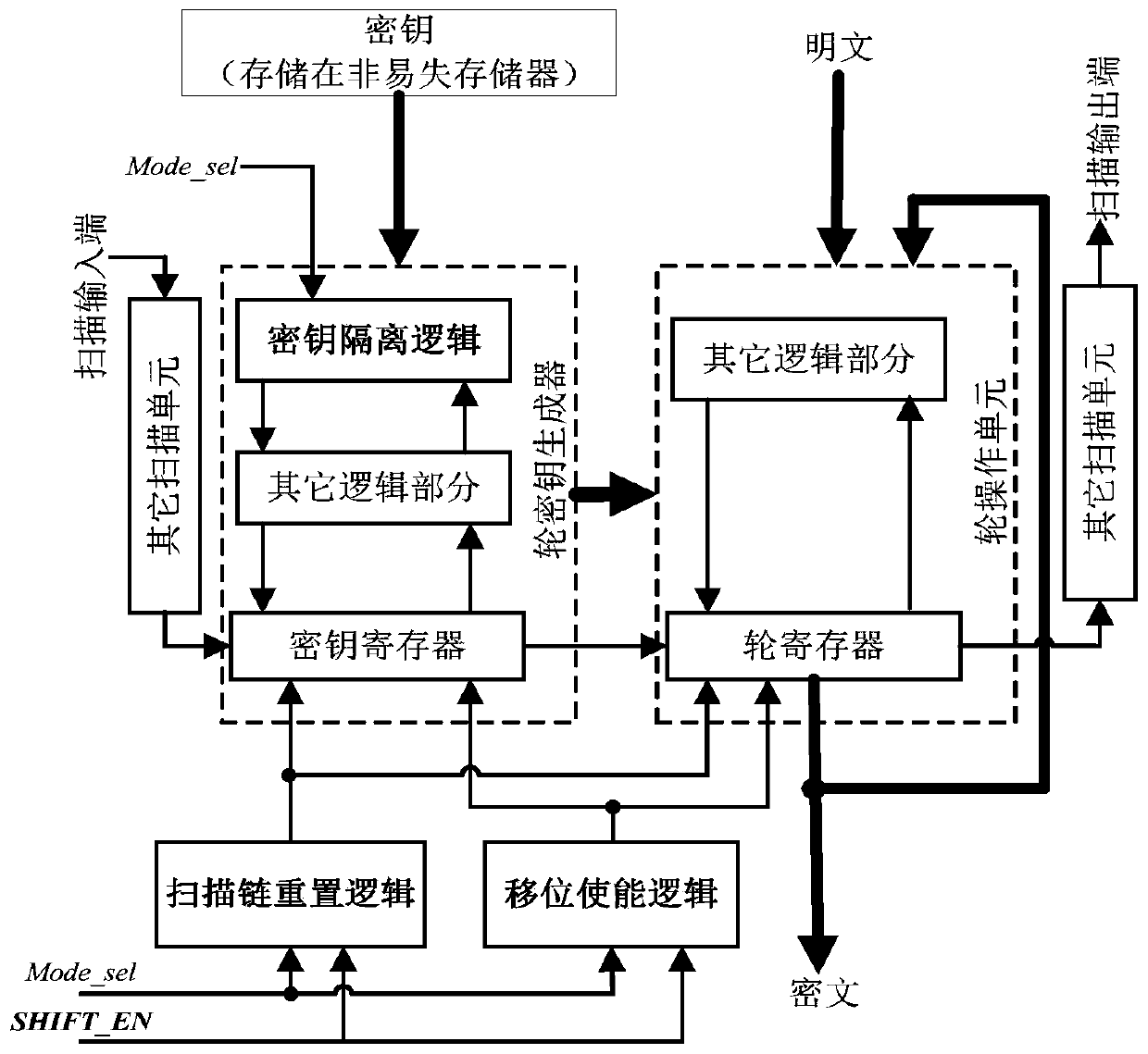
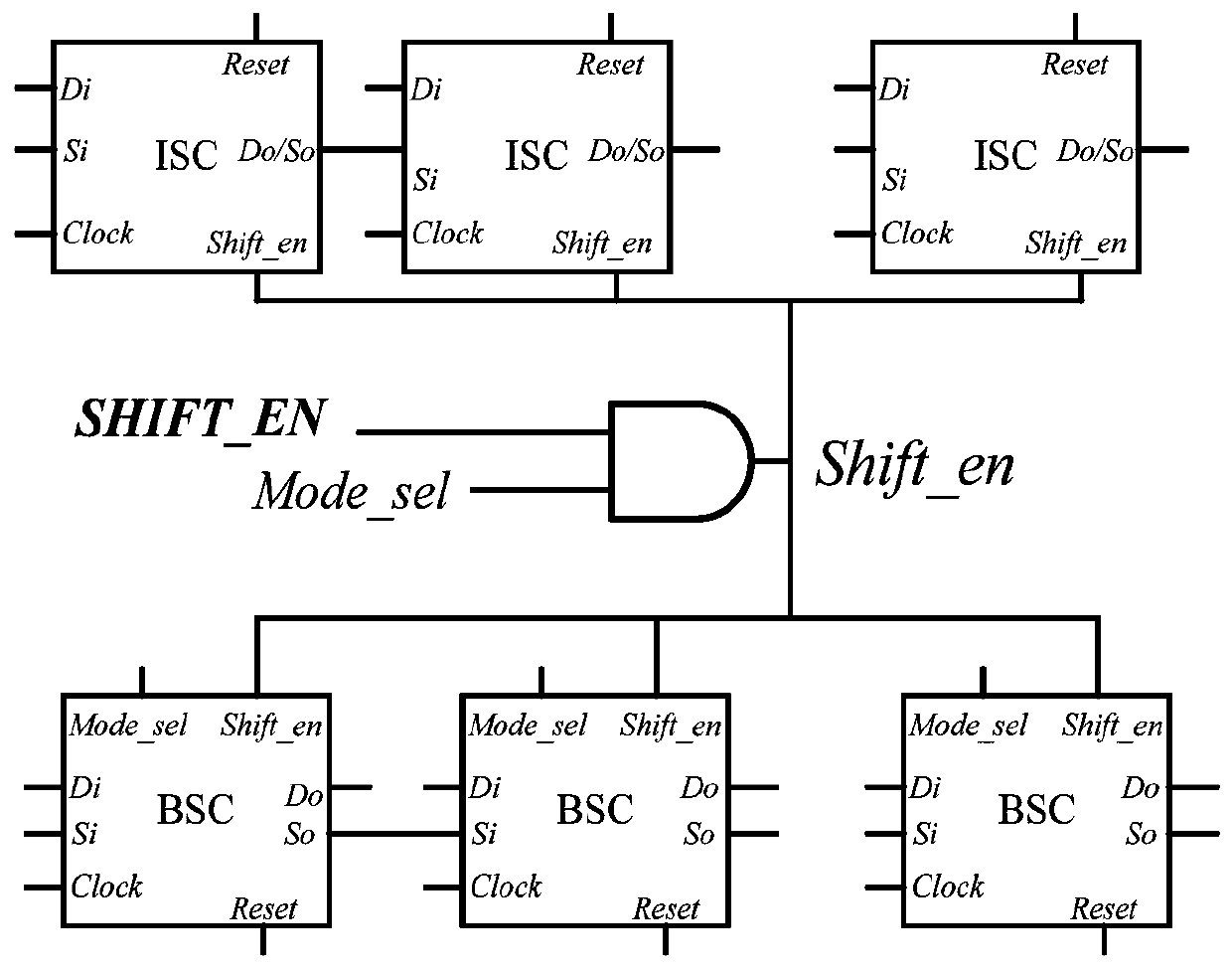
[0028] When using the technology of the present invention to protect the chip, the above-mentioned security control logic needs to be inserted in the chip design stage. After inserting the safety control logic, the working and testing process of the chip is as follows.
[0029] 1. After power-on, if the mode selection signal and shift enable signal {Mode_sel, SHIFT_EN} are both set to 0, the crypto chip runs in functional mode, and the initial key can be loaded into the key register to perform encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com