Encrypted traffic feature extraction method based on feature fusion
A traffic feature and feature fusion technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as the difficulty of providing distinguishing information for encrypted application fingerprints, the discount of classification accuracy performance, and the reduction of encryption application classification accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
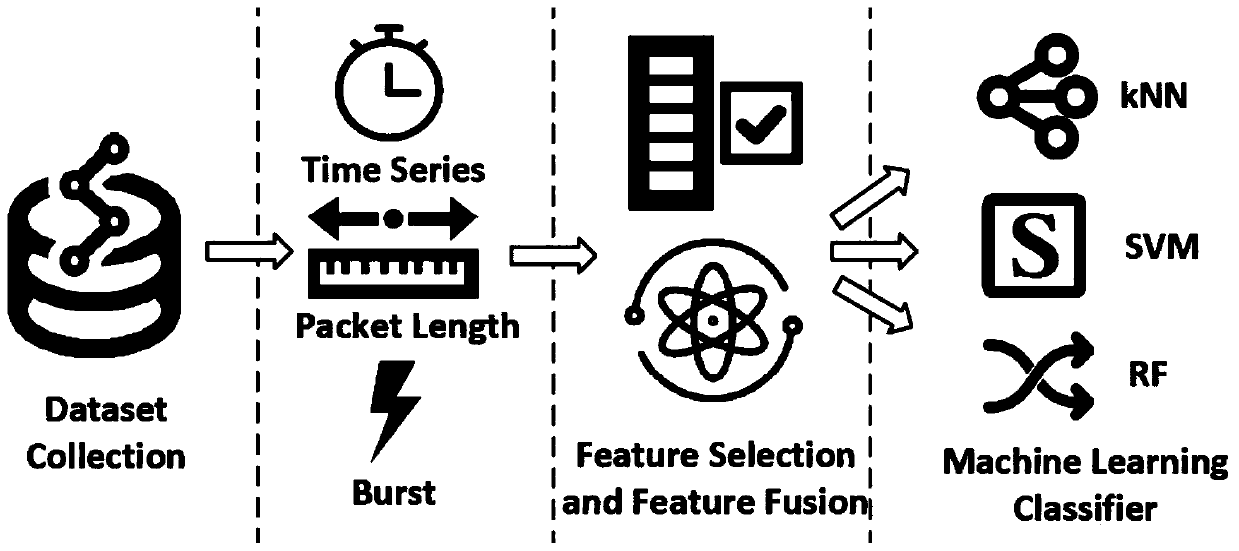
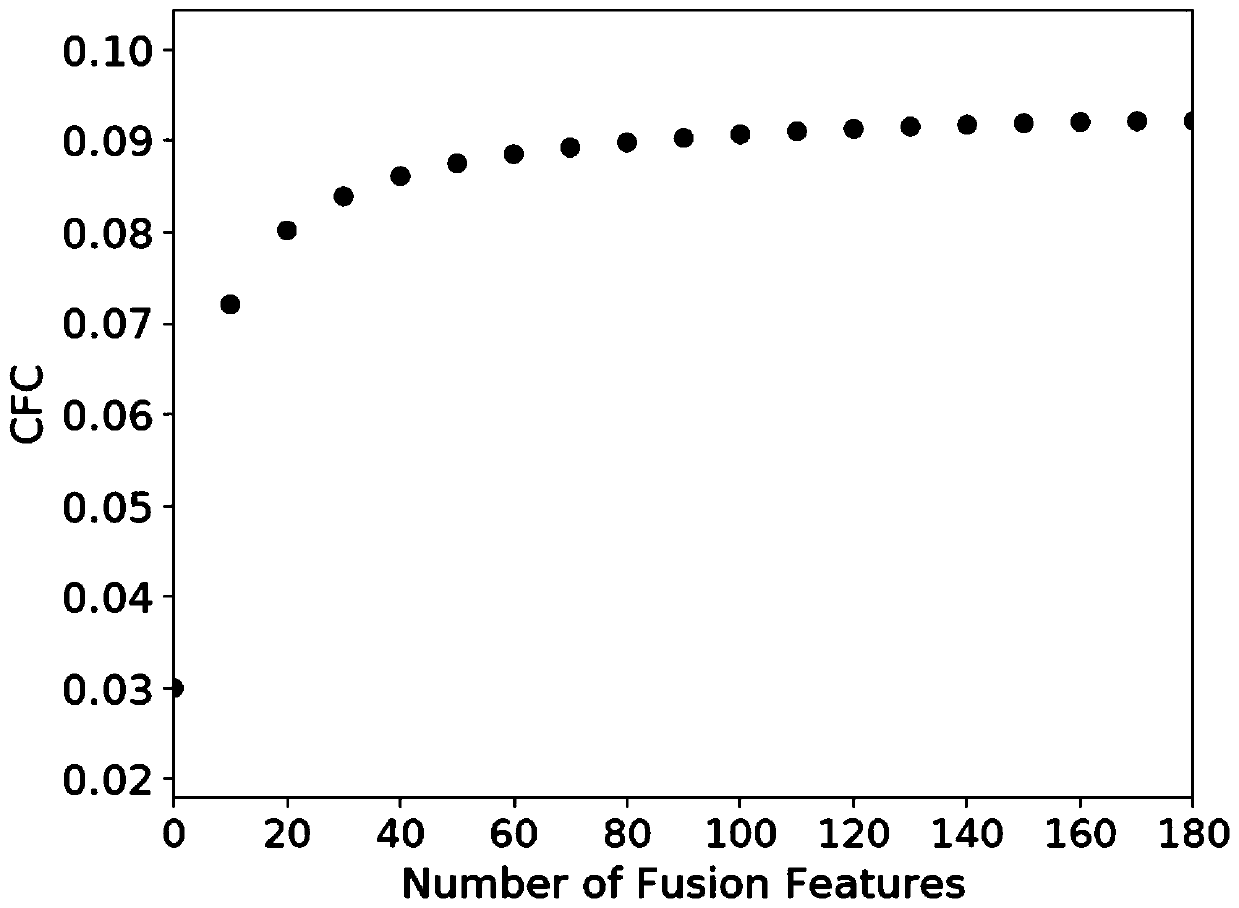
[0063] This embodiment is a complete encrypted traffic feature extraction simulation based on steps 1 to 3 of the present invention. The overall flow chart is as follows figure 1 As shown, Dataset Collection is the data collection stage, which can collect Taobao, JD.com and other website traffic that uses encrypted protocols to transmit data, then perform feature selection and feature fusion, and finally use the fused features for machine learning classification device to classify. By extracting features of different dimensions, the radial basis kernel function is used to increase the feature dimension to obtain the final feature set that participates in classification.
[0064] Collect Taobao, JD.com, Netease Cloud, Amazon, Alipay, WeChat, etc. using encryption protocols to transmit traffic, and divide it in the form of quintuples, specifically:
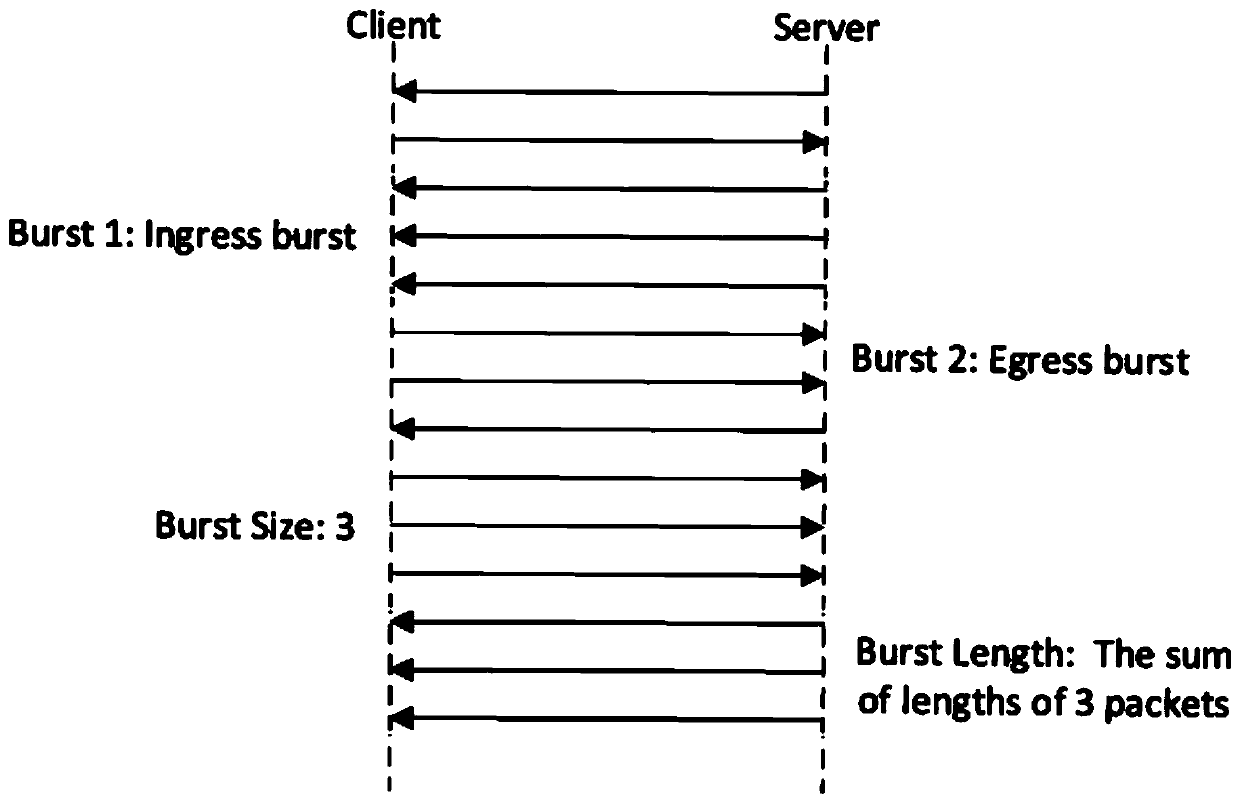
[0065] The first is to extract the statistical feature values of the data packet about the length of the data packet, the time ...
Embodiment 2
[0071] In this embodiment, the traffic features extracted by the method of the present invention are used in a machine learning classifier, and compared with other classifiers that only use single-dimensional features, so as to verify the advantages and effectiveness of the present invention. Combining the encrypted traffic feature extraction method based on feature fusion described in the present invention with the traditional machine learning algorithm random forest is used as the classifier of this method, which is denoted as FFP.
[0072] The methods to be compared include the Markov classifier (MARK) using only the packet flag as a feature and the random forest classifier (APPS) using only the packet length as a feature. The indicators for comparison include the accuracy rate (Accuracy) and F1-score of the classifier. F1-Score comprehensively considers the evaluation criteria of the classifier for the precision rate (Precision) and the recall rate (Recall). The comparison...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com