Method and device for realizing A2 Trojan horse detection through compatible fault scanning test
A technology of scan test and fault test, which is applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of failure to monitor, frequent interruption, large area overhead, etc., to reduce detection time, reduce detection cost, and High diagnostic effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
[0062] Such as Image 6 As shown, the steps of the method for realizing the A2 Trojan horse detection by the compatible fault scanning test of the present embodiment include:
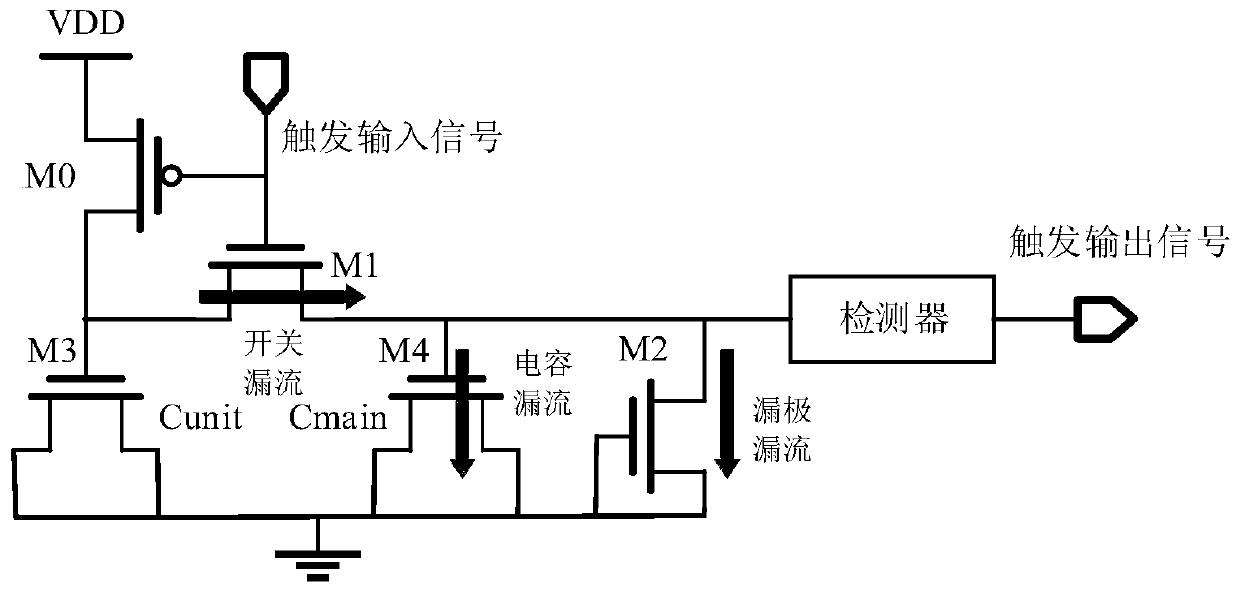
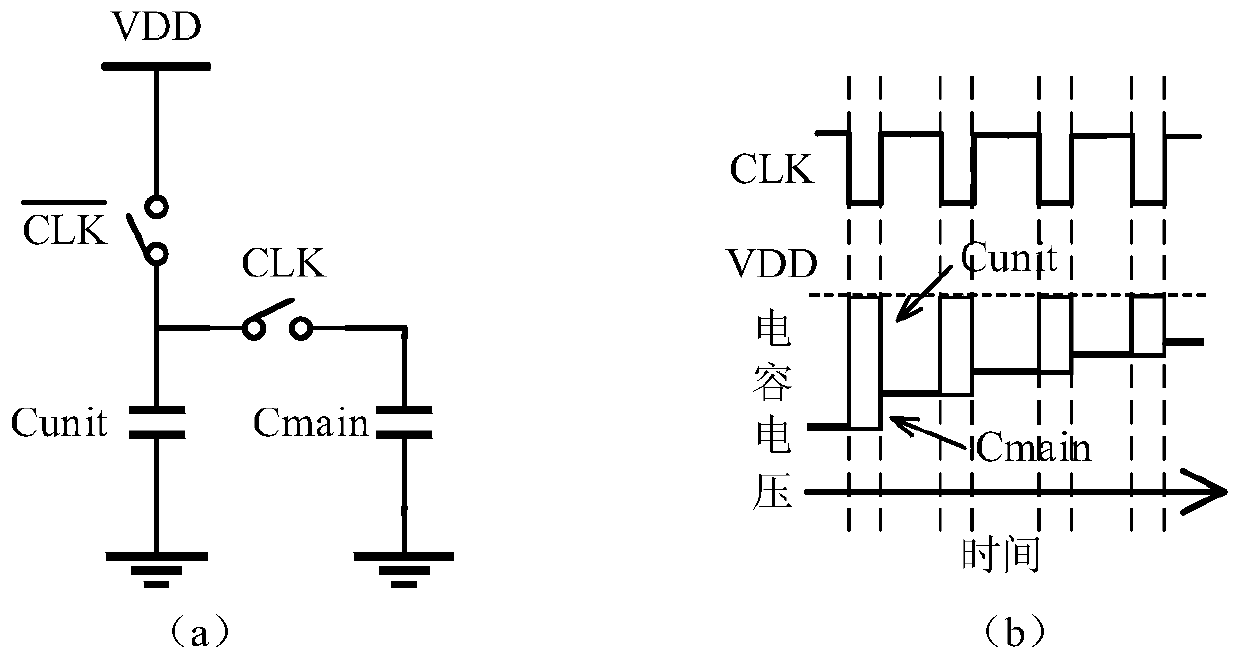
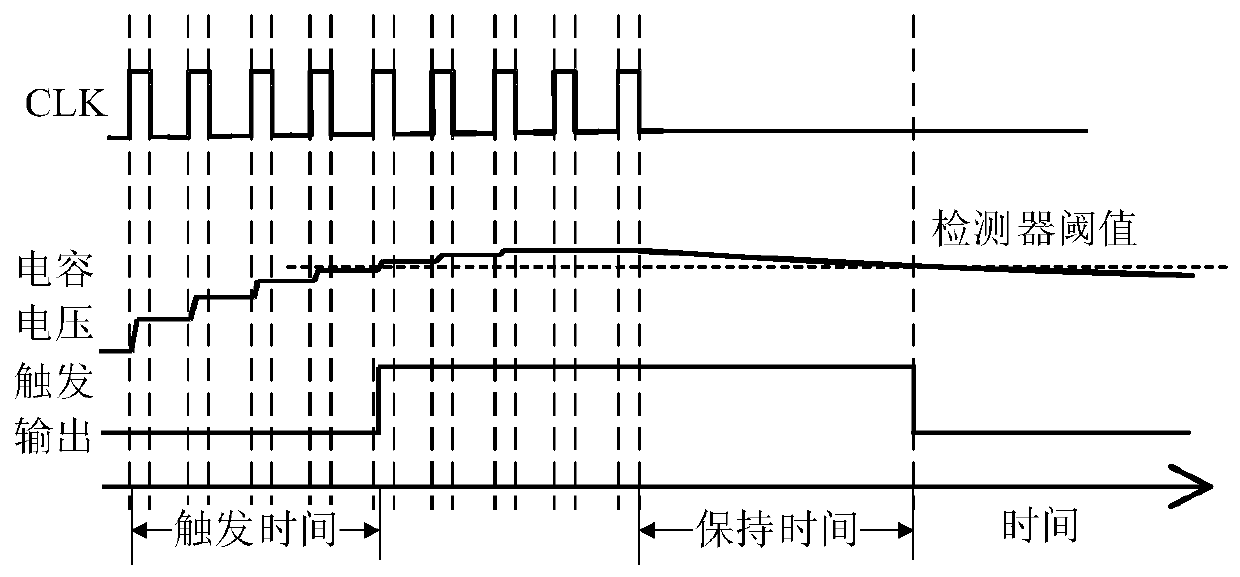
[0063] S1. Insert a multi-function controller and more than one composite ring oscillator in the gate-level netlist generation stage of the chip to be tested. The chemical units are sequentially connected into an end-to-end ring chain structure, and the working mode of the compound ring oscillator is controlled by a multi-function controller;
[0064] S2 When performing a fault test on the chip to be tested, configure a multi-function controller to make the working modes of each compound ring oscillator change alternately during the scanning shift stage to enhance the jump of suspicious ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com