Industrial control system intrusion attack and clue discovery method based on deep learning
A technology of deep learning and industrial control systems, applied in the general control system, control/regulation system, test/monitoring control system, etc., can solve the problems of delaying the time to deal with intrusions, shortening the time required to deal with intrusions, poor security awareness, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
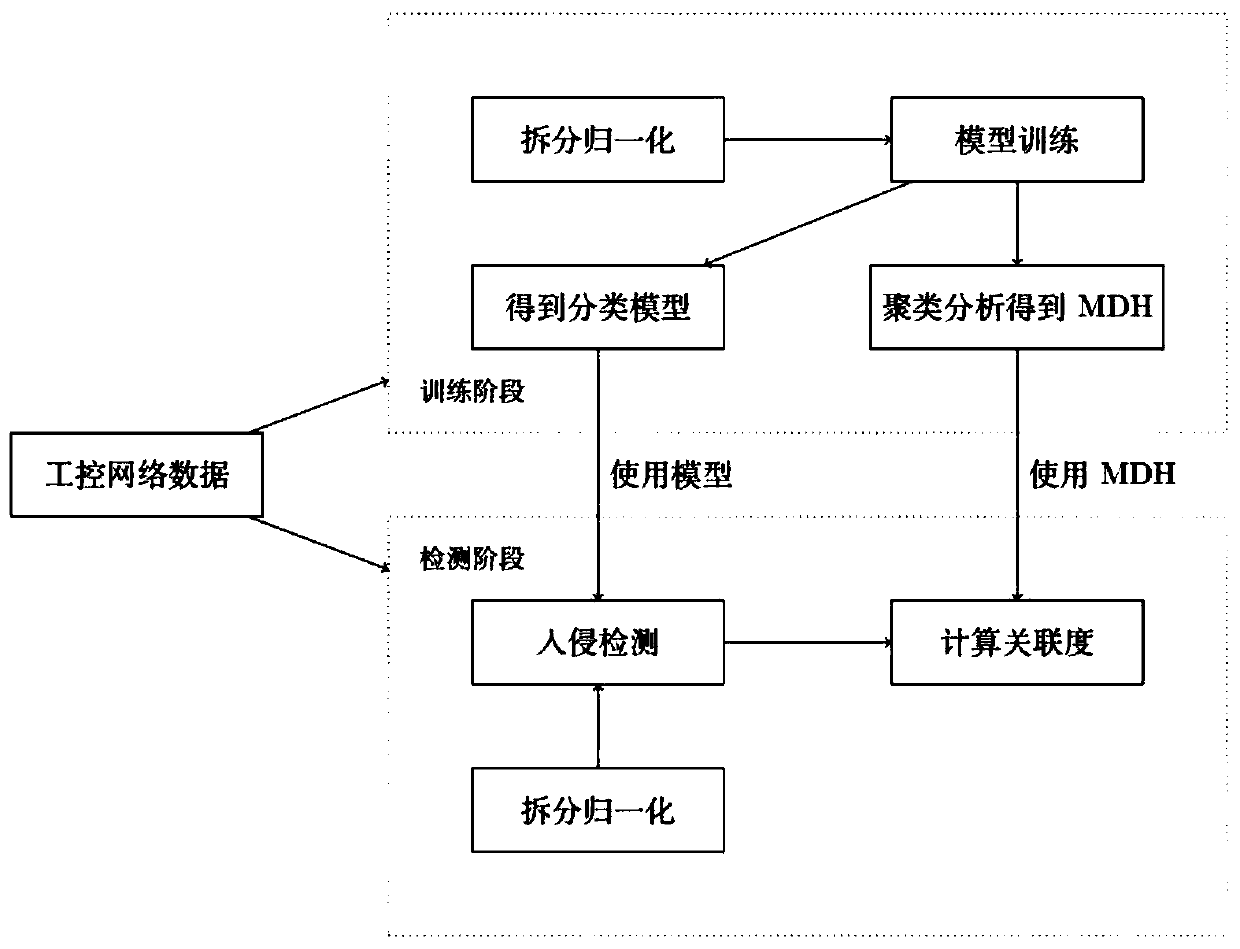
[0021] The overall framework diagram of the industrial control network intrusion attack and clue discovery method based on deep learning in the present invention is as follows figure 1 shown, including:
[0022] In the training phase, the data from the industrial control network of the data set is dedimensionalized by splitting and normalizing the method, and the data is used to train the deep learning classification model as the intrusion detection model. After the model training is completed, the cluster analysis method can be used to obtain each category of MDH.
[0023] The steps of the cluster analysis method are as follows:
[0024] Step 1.1 clusters the output of the hidden layer of the deep learning model to obtain a clustering model;
[0025] Step 1.2 tries to form a new classification model through each hidden layer output +...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com