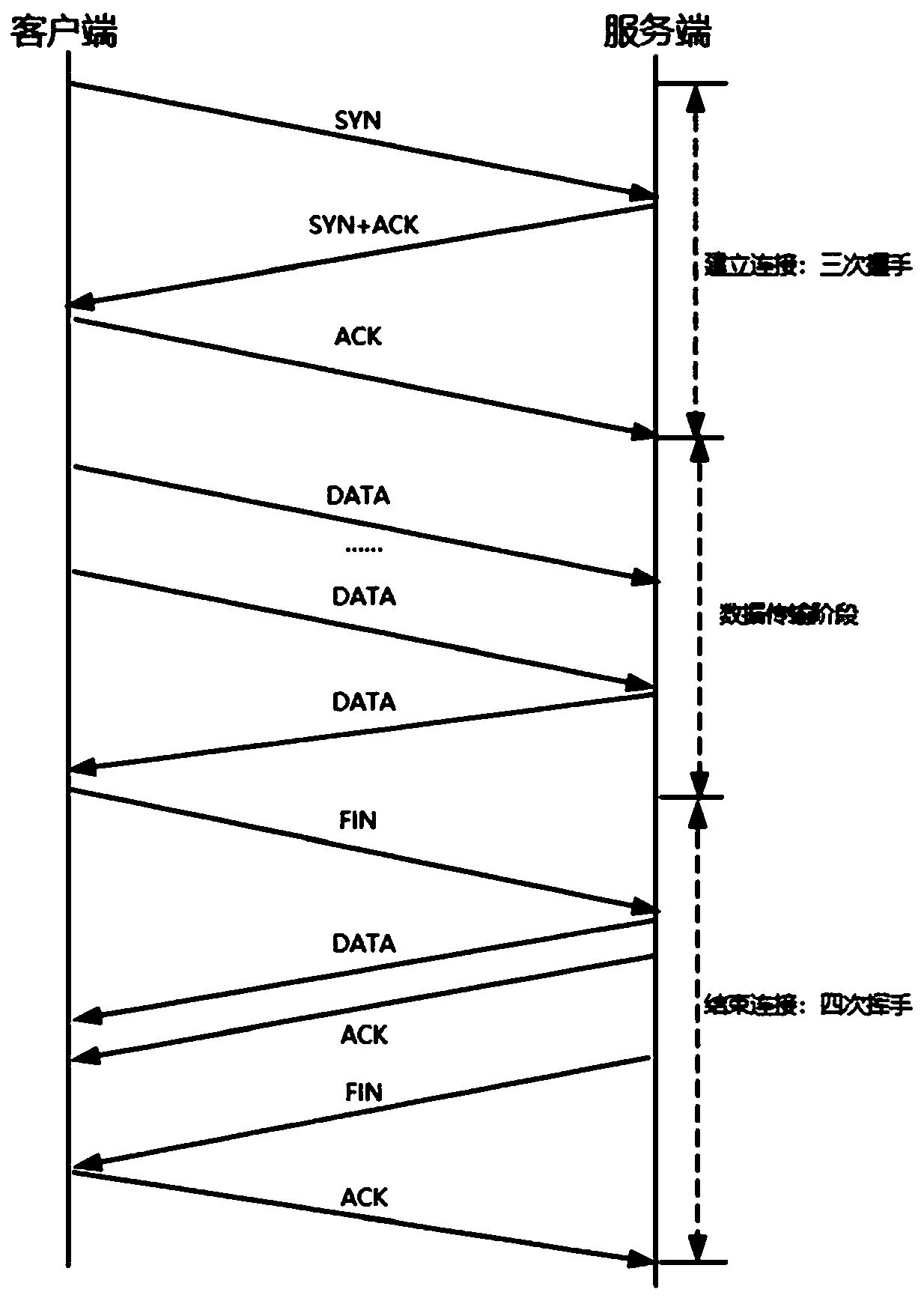
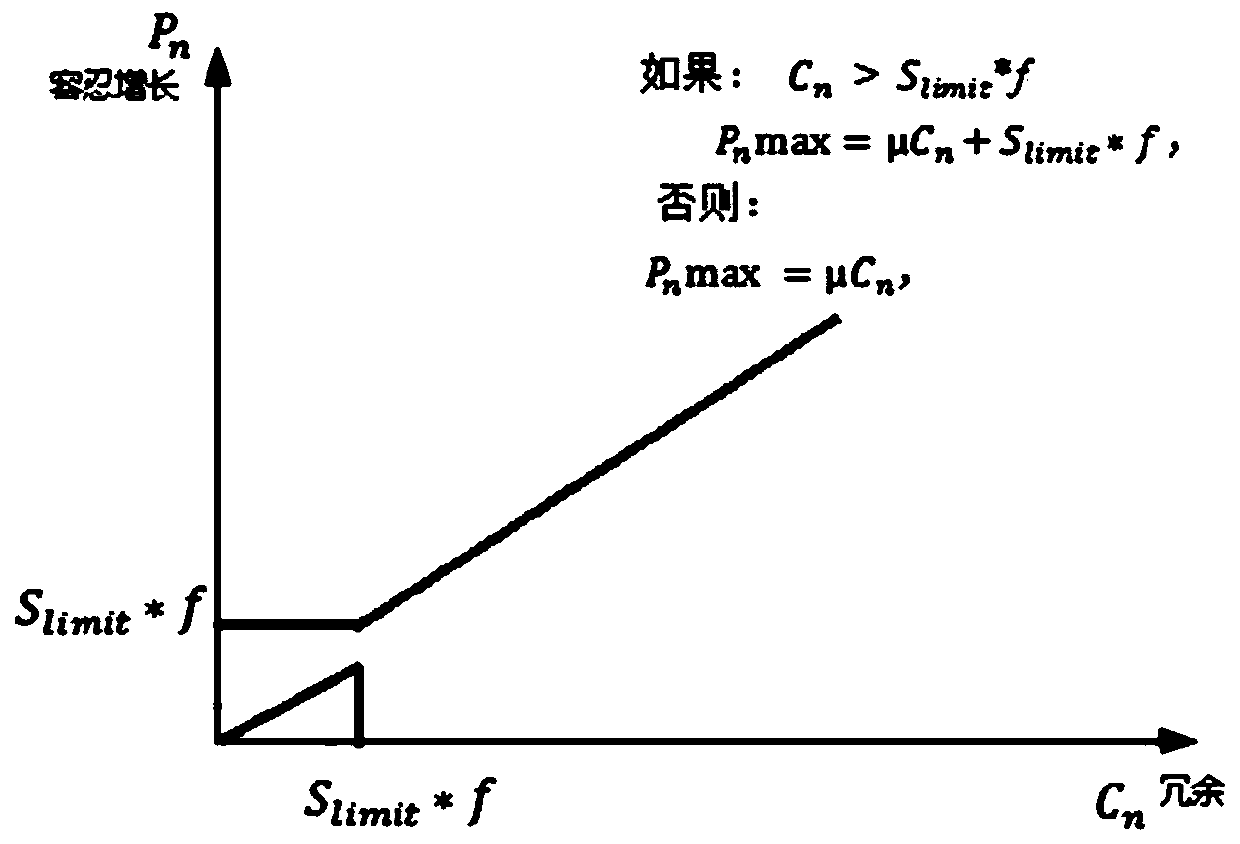
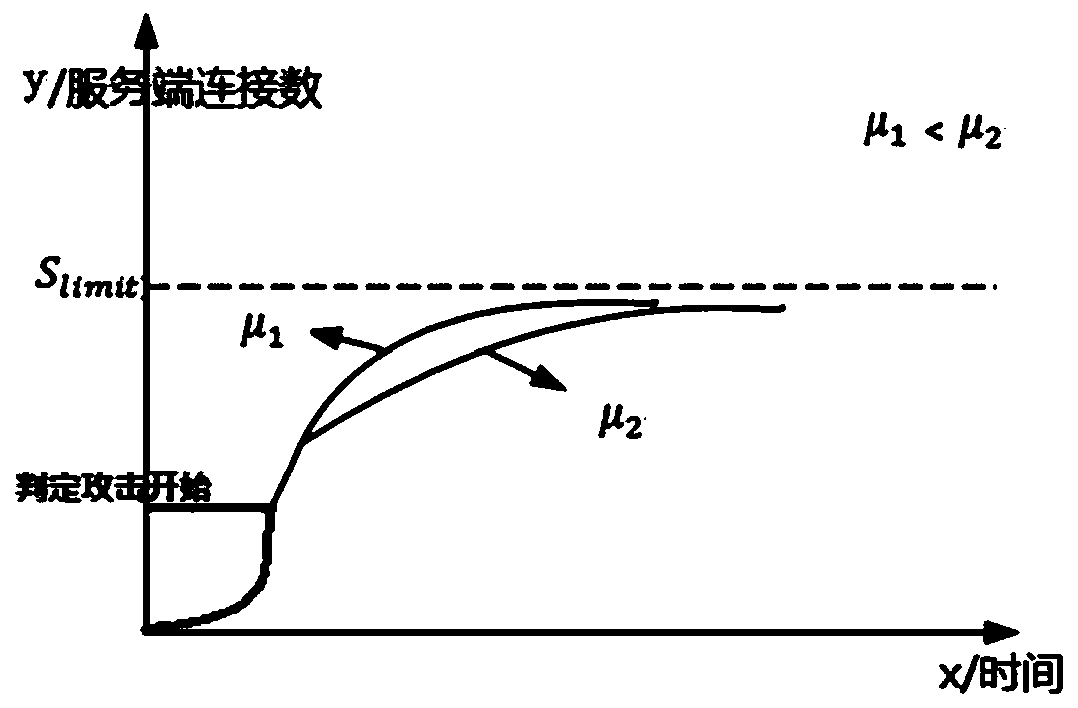
DDoS attack judgment and flow cleaning method and device and electronic equipment
A technology of traffic cleaning and traffic differentiation, applied in the field of network security, it can solve the problems of network service crash, inability to respond to data packets, exhaustion of target resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0162] In this embodiment, the following scenario is set: there is server A, and the maximum load connection number is 5000 (S limit =5000), S v =0.9*S limit = 4500;
[0163] After accessing the protection of the device of the present invention, under normal circumstances (assuming 10 seconds, from 0 to 5000, then the increase per second is 500, then with 500 as the initial judgment of the IP just accessed, no more than 500, Then it is judged as a normal scene. When the value is learned later, the policy is discarded. This policy is only for the IP that has just been connected for 1 hour), study for 1 hour, and get the average number of SYN packets sent by all IPs SYN_Mode= 50, get Smax=2500, Umax=400; Smax is the maximum value of the server connection during the learning period. Umax is the maximum value of the number of new connections during the learning period;
[0164] When attacking the scene:
[0165] The number of session connections in the second second S2=4000, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com