Mimicry safety system and method based on sampling detection
A sampling detection and security system technology, applied in the field of network communication, can solve problems such as increasing the difficulty and cost of loopholes and backdoor attacks, difficulty for attackers to observe and predict, complex computing functions, etc., to improve the efficiency of mimicry ruling, reduce storage space and Computing resources and ensuring timeliness effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
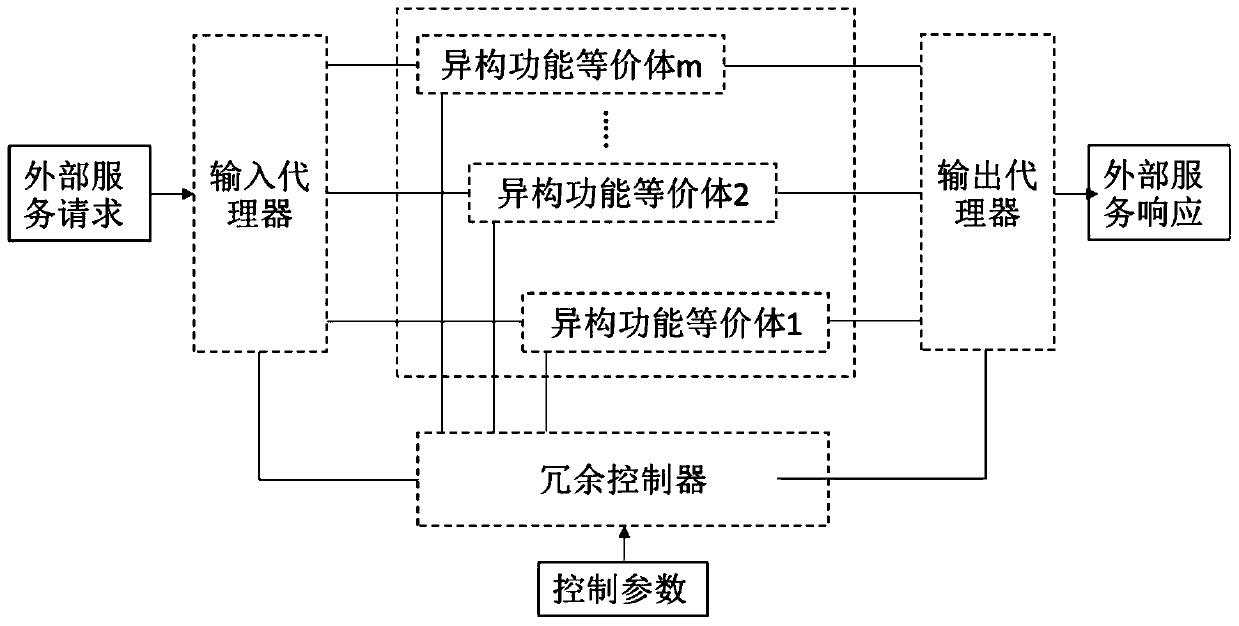
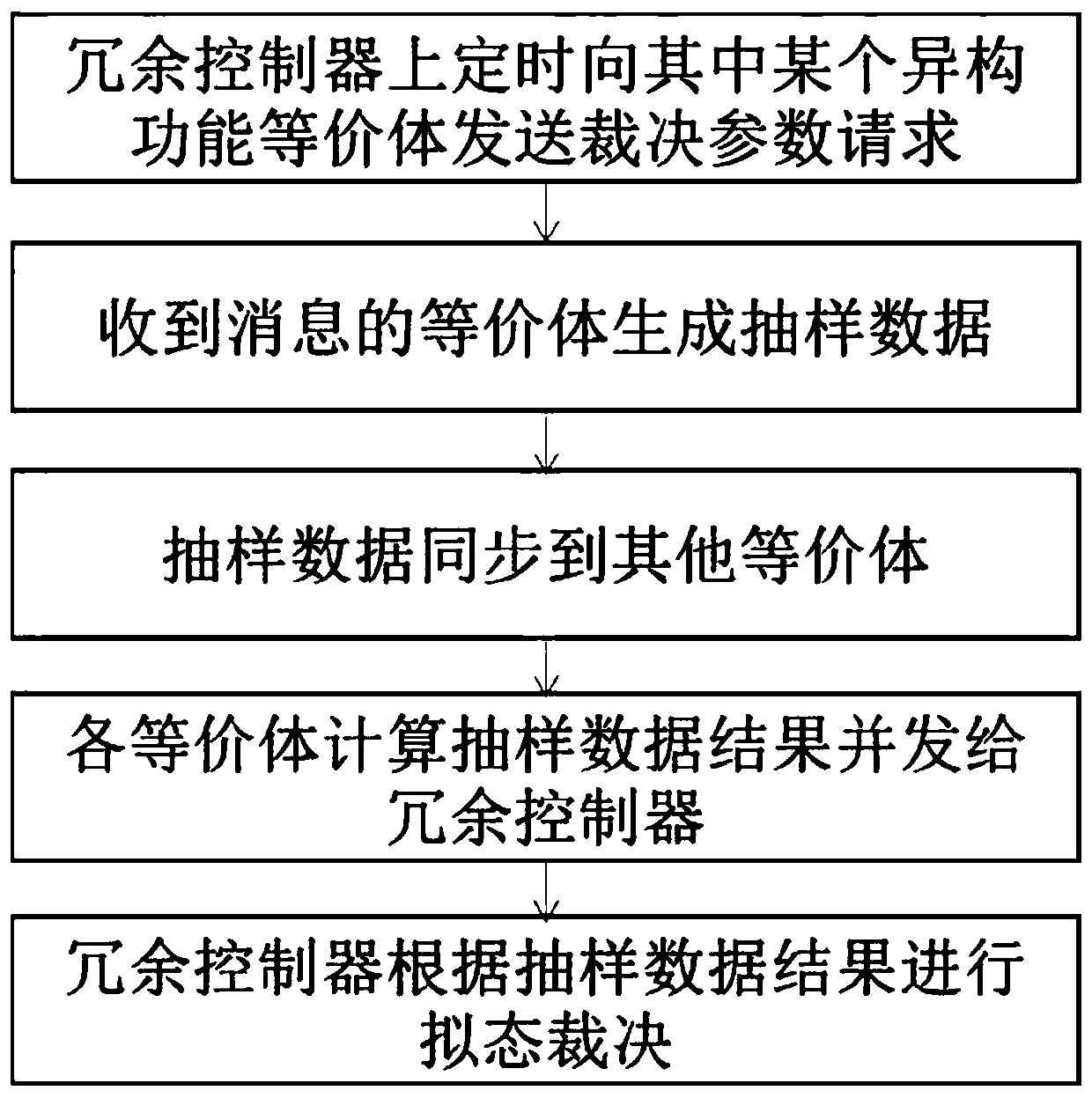
[0025] A mimic security system based on sampling detection, including an input agent, a redundant controller, at least two heterogeneous functional equivalents, and an output agent; the input agent is used to receive an external service request according to the redundant controller Agent strategy, sending external service requests to one or more selected heterogeneous functional equivalents; redundant controller, used to compare the parameters of the judgment results of heterogeneous functional equivalents, and notify the output of the ruling result Agent; the heterogeneous functional equivalent is used for sampling data selection and synchronization, making feature judgment on the sampled data, and sending the judgment result to the redundant controller; the output agent is used to transfer the corresponding The output of the equivalent body is sent as an external service response;
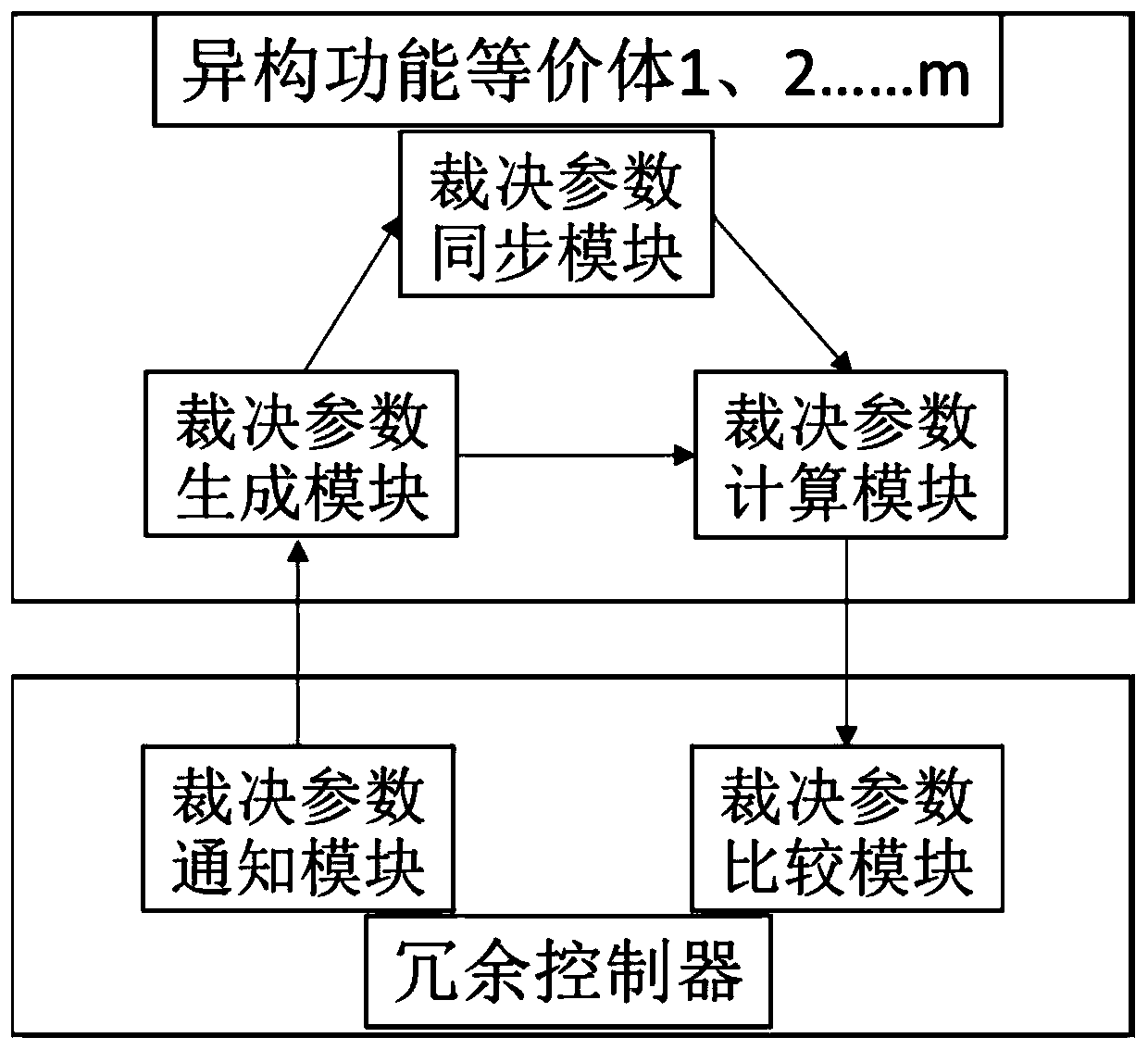
[0026] Further, as figure 2 As shown, the redundant controller includes:
[0027] Adjudica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com