Video signature verification and evaluation tool and method based on GB35114 standard
A GB35114, video technology, applied in the field of video signature verification and evaluation tools, can solve problems such as video security chaos
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
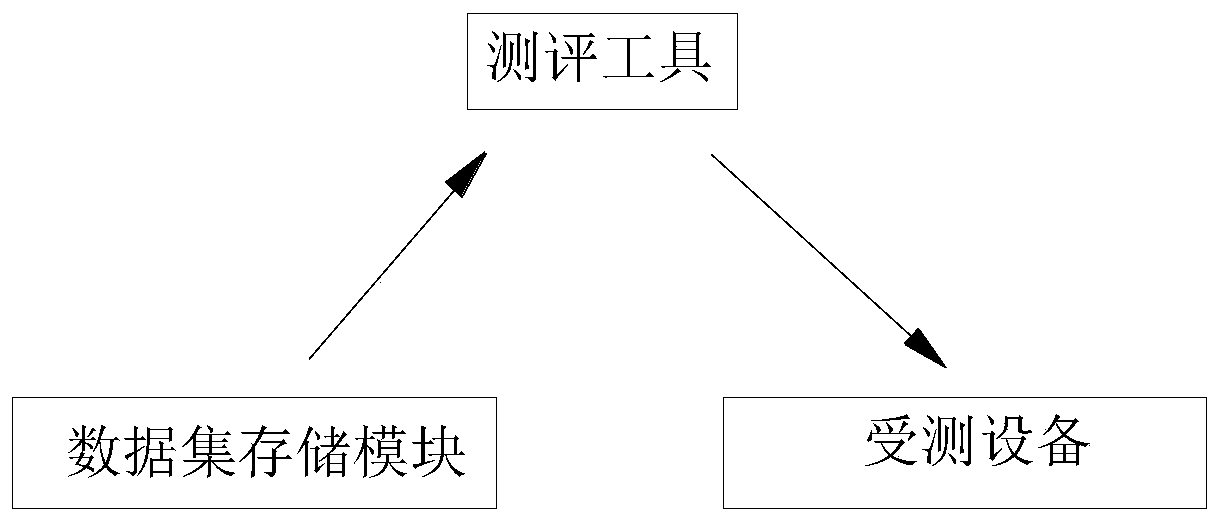
[0043] A video signature verification and evaluation tool based on the GB35114 standard, such as figure 1 shown, including:
[0044]Data set storage module: used to store the test data support data set, the test data support data set includes a key set and a data set, and the data set includes a cryptographic hash algorithm salt value data set, a video signature forward test data set and A video signature reverse test data set; the key set includes an asymmetric encryption private key key set and an asymmetric decryption public key key set;
[0045] Video signature and signature verification evaluation tool: communicate with the data set storage module and the device under test, used to retrieve the corresponding key set and / or data set from the data set storage module and send it to the device under test, and test the device under test Whether the function and performance of the signature and / or signature verification of the device comply with the GB35114 standard.
[0046]...
Embodiment 2
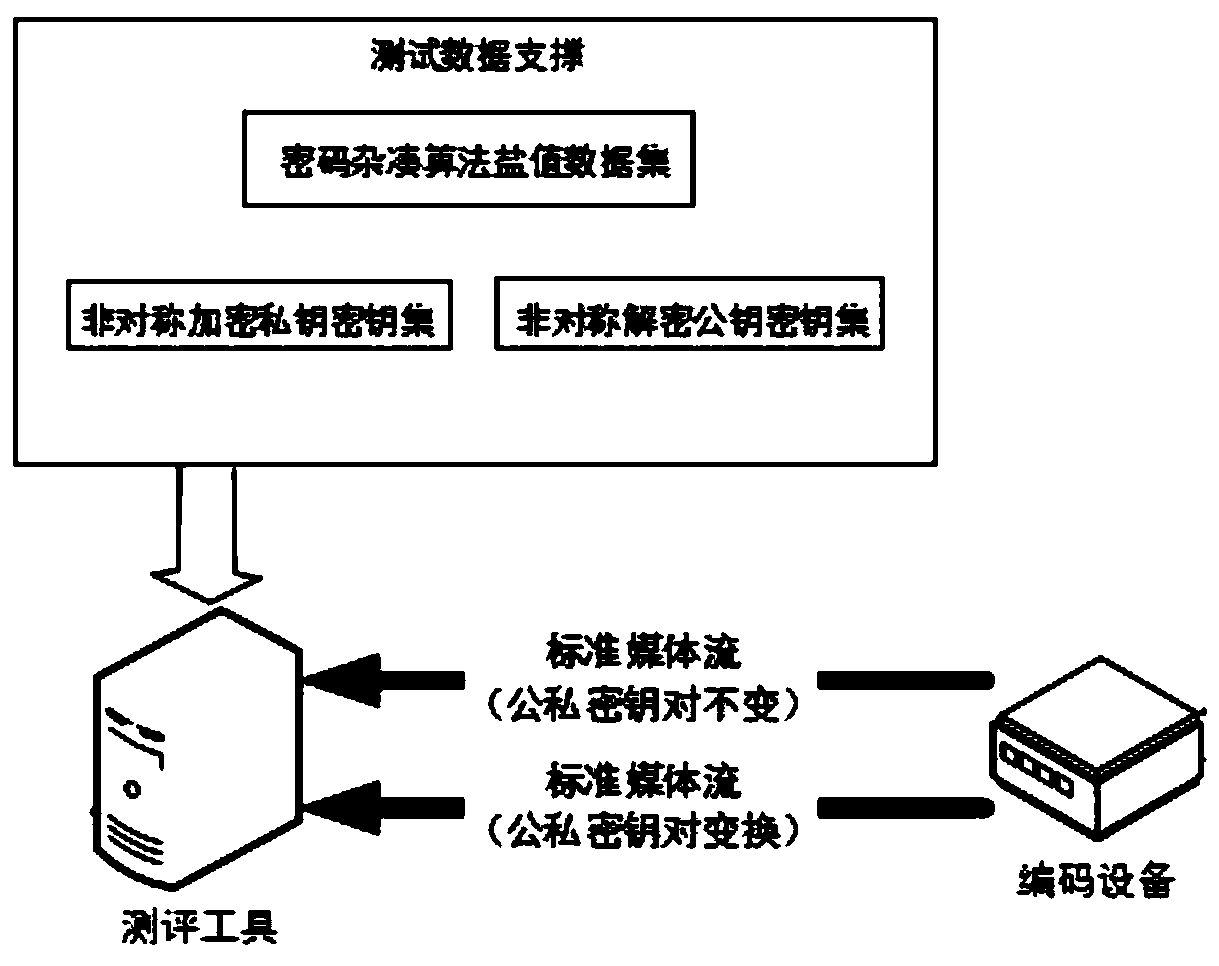
[0048] The following provides a specific application example of the evaluation tool as described in Embodiment 1 when detecting an encoding device with a digital signature function. Deployment such as figure 2 Shown:
[0049] 1. The video signature and signature verification evaluation tool selects the asymmetric encryption private key key, asymmetric decryption public key key and cryptographic hash algorithm salt value data from the test data supporting data set;
[0050] 2. Send the key and data information selected in step 1 to the encoding device under test, and synchronize to the database; the database is used to store the asymmetric key VKEK information and password hash algorithm salt value used in each test As well as test data and test status information, these contents are used for test process recording and analysis and test result judgment, etc.
[0051] 3. The encoding device under test uses a given key to perform video stream signature operations;
[0052] 4. ...
Embodiment 3
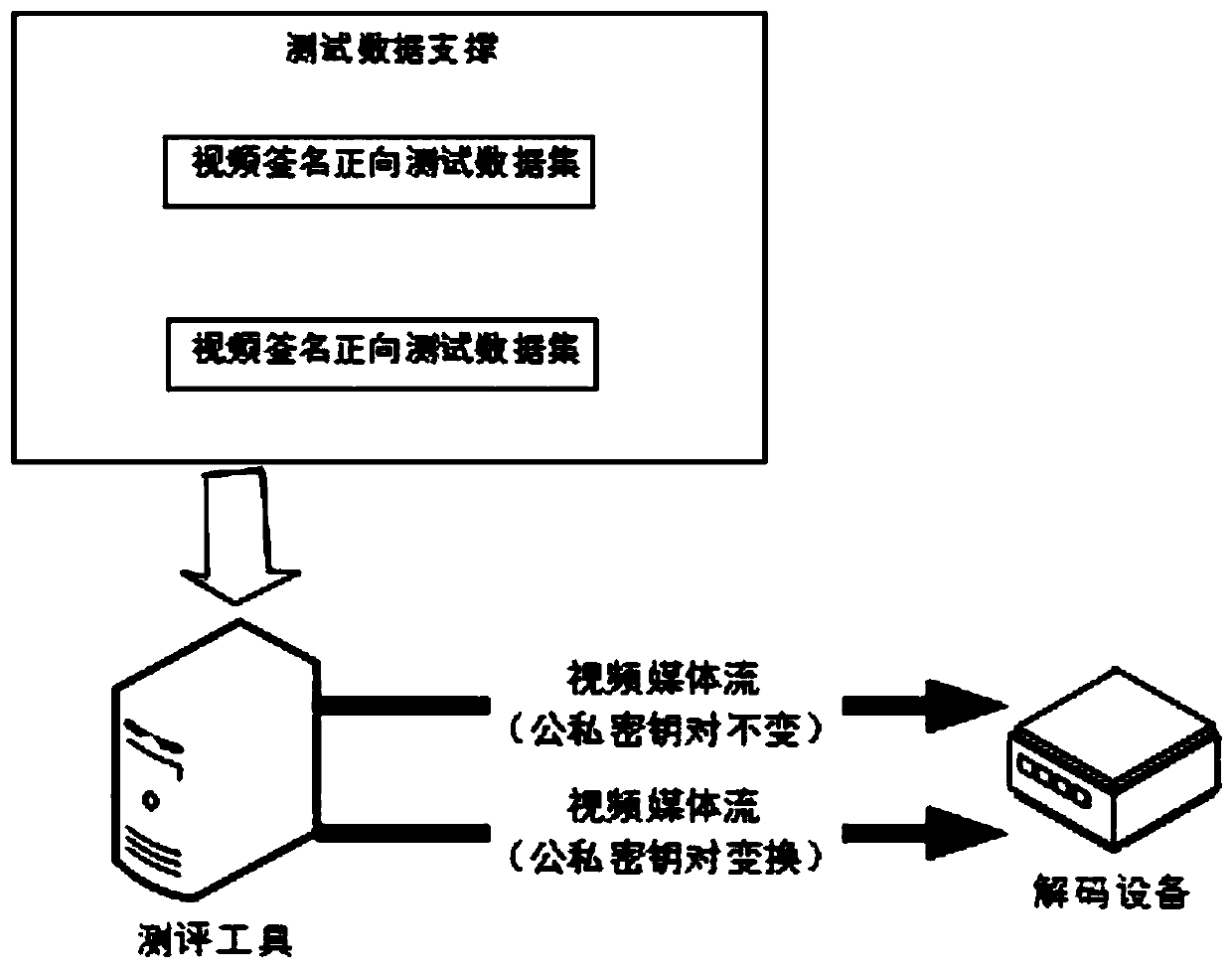
[0060] The following provides a specific application example of the evaluation tool as described in Embodiment 1 when detecting a decoding device with a video signature verification function. The deployment is as follows image 3 Shown:
[0061] 1. When the video signature and signature verification evaluation tool detects the decoding device, first, the evaluation tool selects the video signature forward test data or the video signature verification reverse test data from the test data supporting data set;
[0062] 2. Use video signature and signature verification evaluation tools to perform on-demand and playback operations on the tested decoding equipment;
[0063] 3. Test and judge the signature verification performance of the tested decoding equipment. If all pass, it is considered that the video signature verification function and performance of the decoding equipment meet the requirements of the national standard.
[0064] In video signature verification commissioning,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com