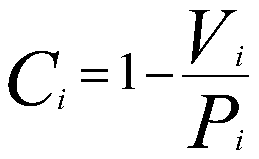Quantitative characterization method for potential threat degree of mimicry controller executor
A technology of threat level and executive body, applied in the field of quantitative characterization of potential threat level, it can solve the problems of unguaranteed detection cycle, labor-intensive, difficult to accurately judge potential threat level, etc., so as to enhance security and reliability, and improve reliability. , the effect of improving the robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
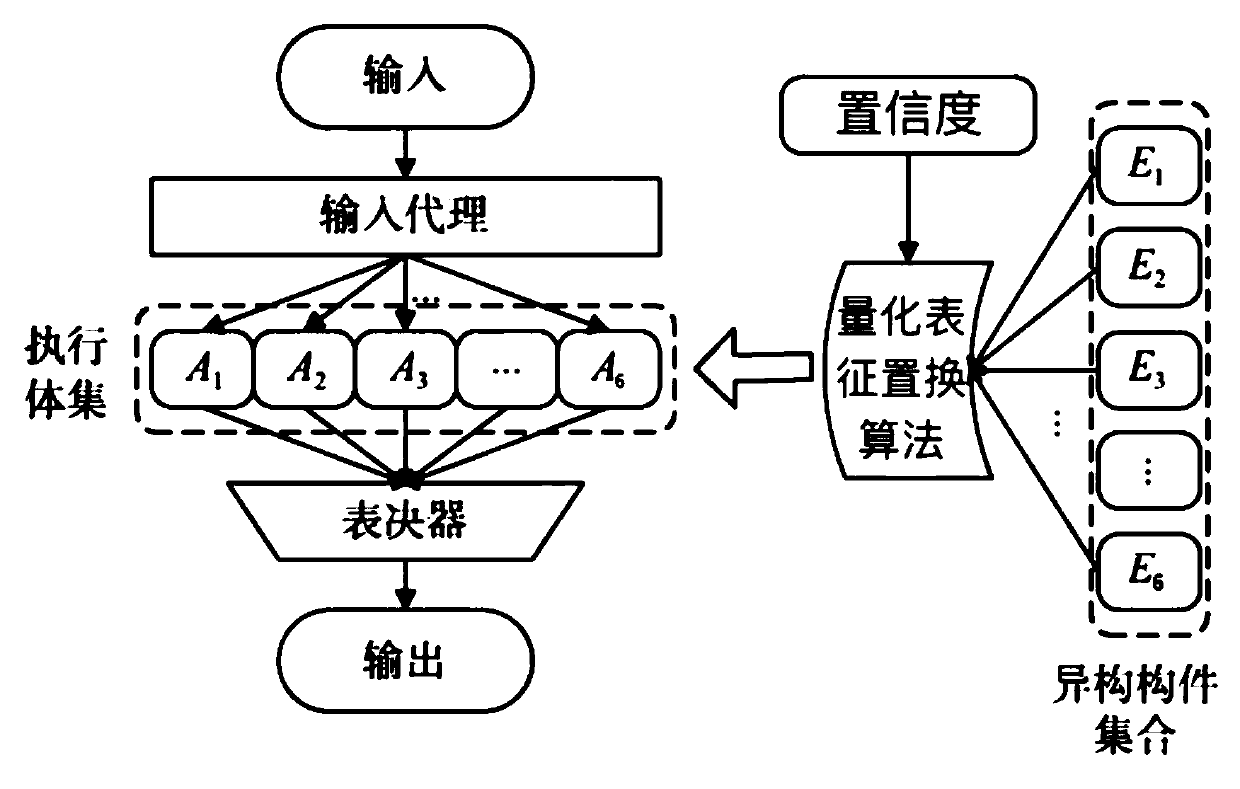
[0032] This example works on the mimic controller in the mimic defense server, such as figure 1 As shown, running A in the mimic controller 1 ~A 6 A total of 6 executive bodies, and E 1 ~E 6 A total of 6 offline executives are input into the controller and delivered to 6 online executives; the method of the present invention replaces the online and offline executives at the same time period t according to the following specific steps to ensure the final voter According to the algorithm, the final result is true and reliable, and the processing of the access request is completed.
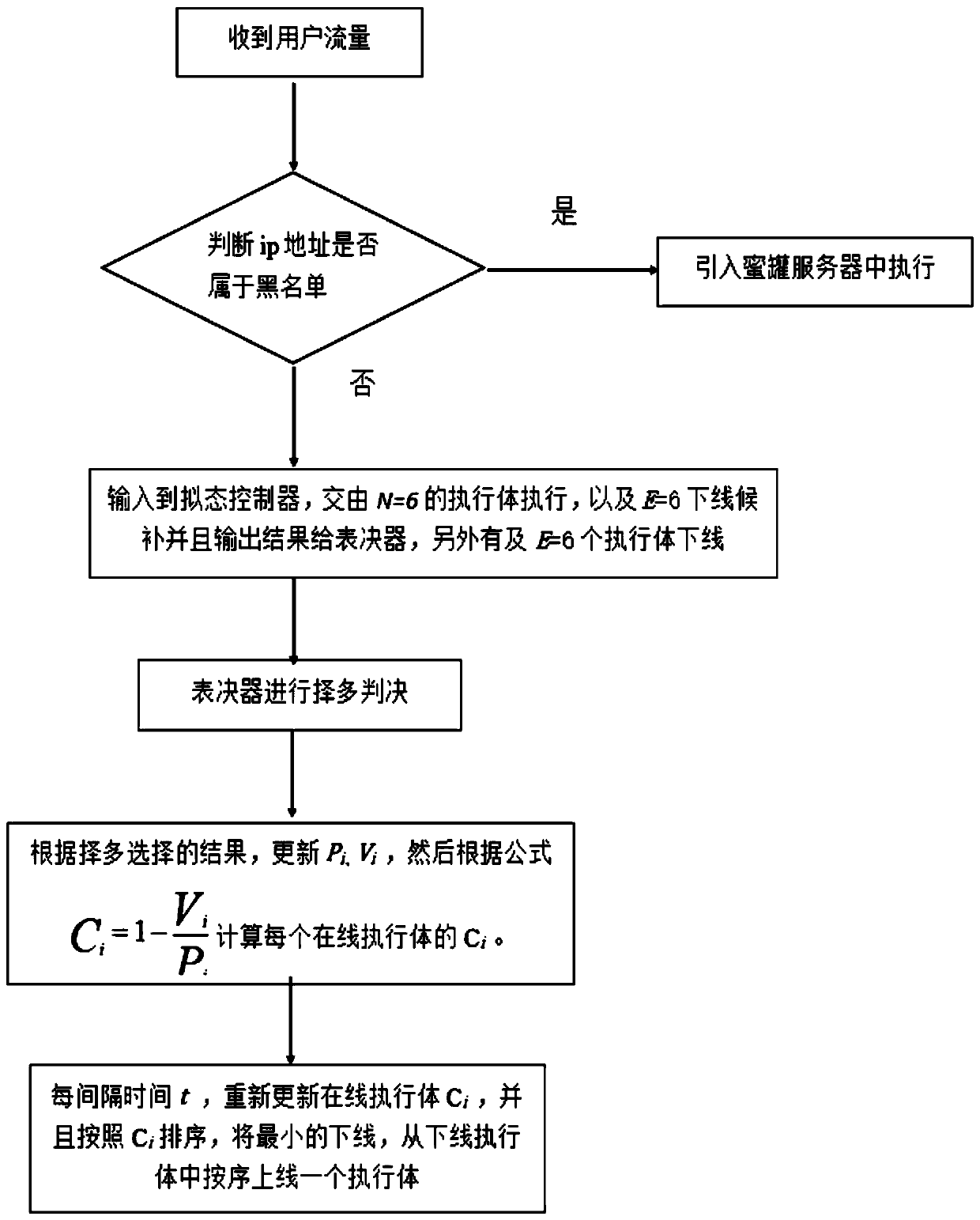
[0033] Such as figure 2 As shown, this example is implemented through the following steps:
[0034] Step 1. Receive a user access request, input the agent to determine whether the user IP is in the blacklist of the honeypot server, if yes, then import the request into the honeypot server for execution; if not, then enter step 2;
[0035] Step 2: Input to the mimic controller, deliver to the on...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap