Big data test field safety initialization method based on trusted third party
An initialization and big data technology, applied in the direction of electrical components, transmission systems, platform integrity maintenance, etc., can solve cloud platform security disputes, cloud provider difficult to detect, user data loss and other issues, to improve security and fairness reliability, data protection, and high-confidence effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
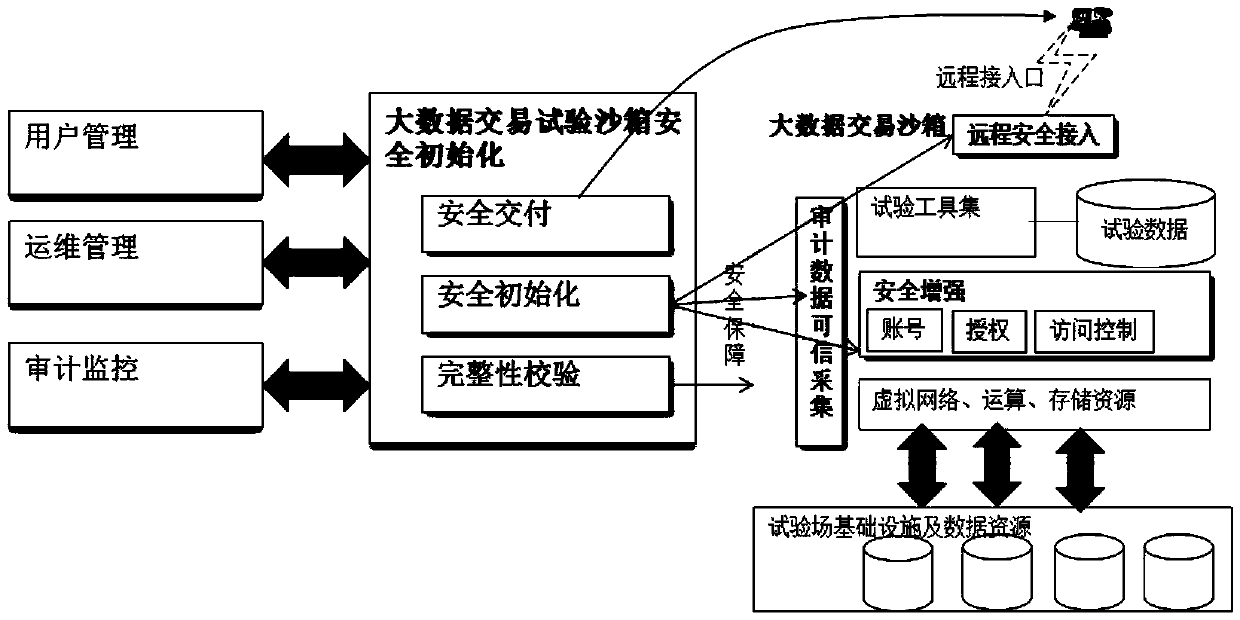
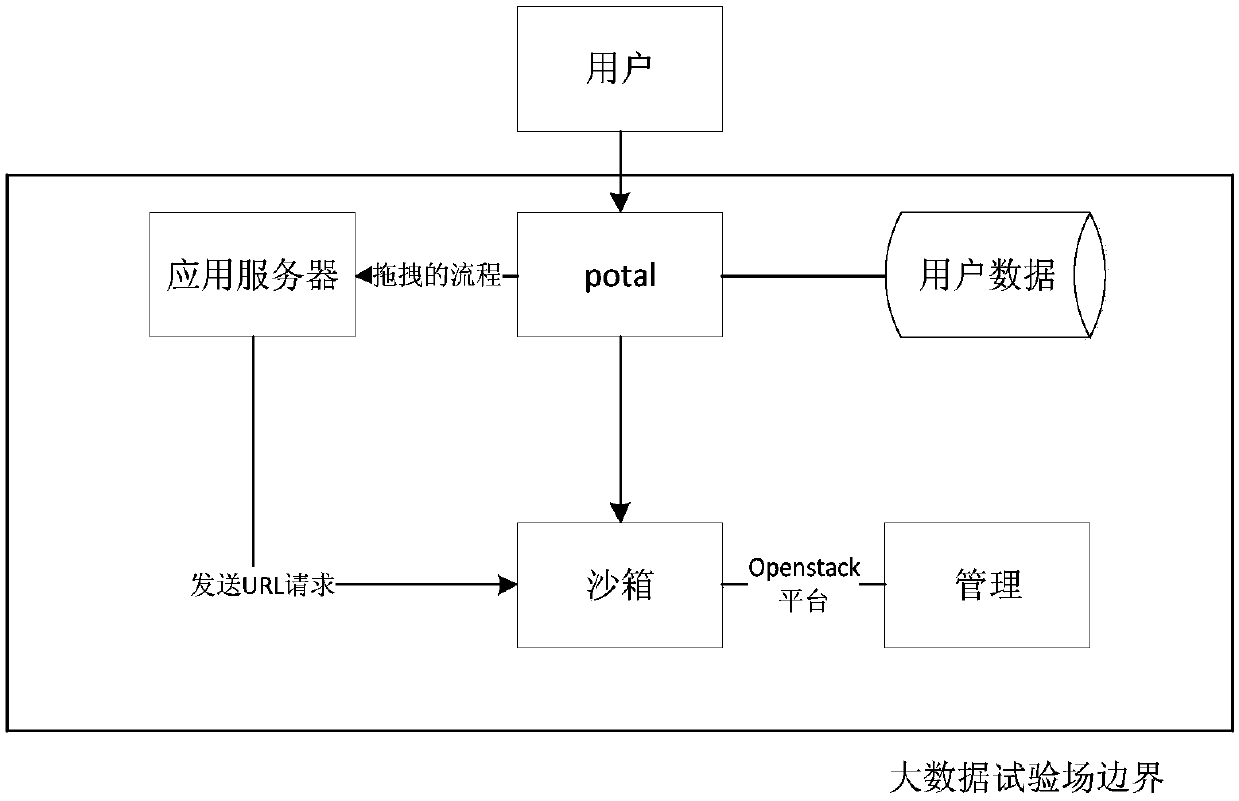
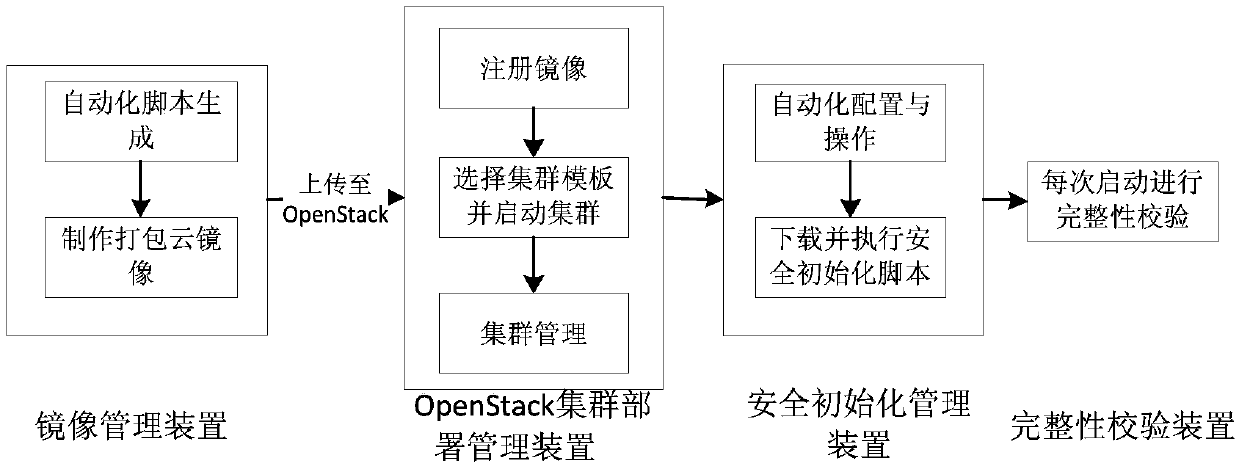
[0057] Such as image 3 The described invention is composed of a mirror image management device, an OpenStack cluster deployment management device, a security initialization management device, and a system integrity verification device. On the server, the OpenStack cluster deployment management device is installed on the cloud platform management server of the cloud service provider, and the security initialization management device and the system integrity verification device are installed on each virtual machine in the cloud environment.
[0058] As a software running on a trusted third-party server, the image management device can run in the background service mode, continuously receive the requirements collected from the cloud service provider for the big data operating environment in the sandbox, and use the official OpenStack project as required Diskimage-builder makes and packages the cloud image, and inserts scripts related to security initialization during the process;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com