Sovereign network architecture of rear IP
A technology of architecture and sovereignty, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as the inability to guarantee the controllability of the network, and the inability to provide good support for mobile services, so as to improve user experience, The effect of improving security and improving data transmission efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
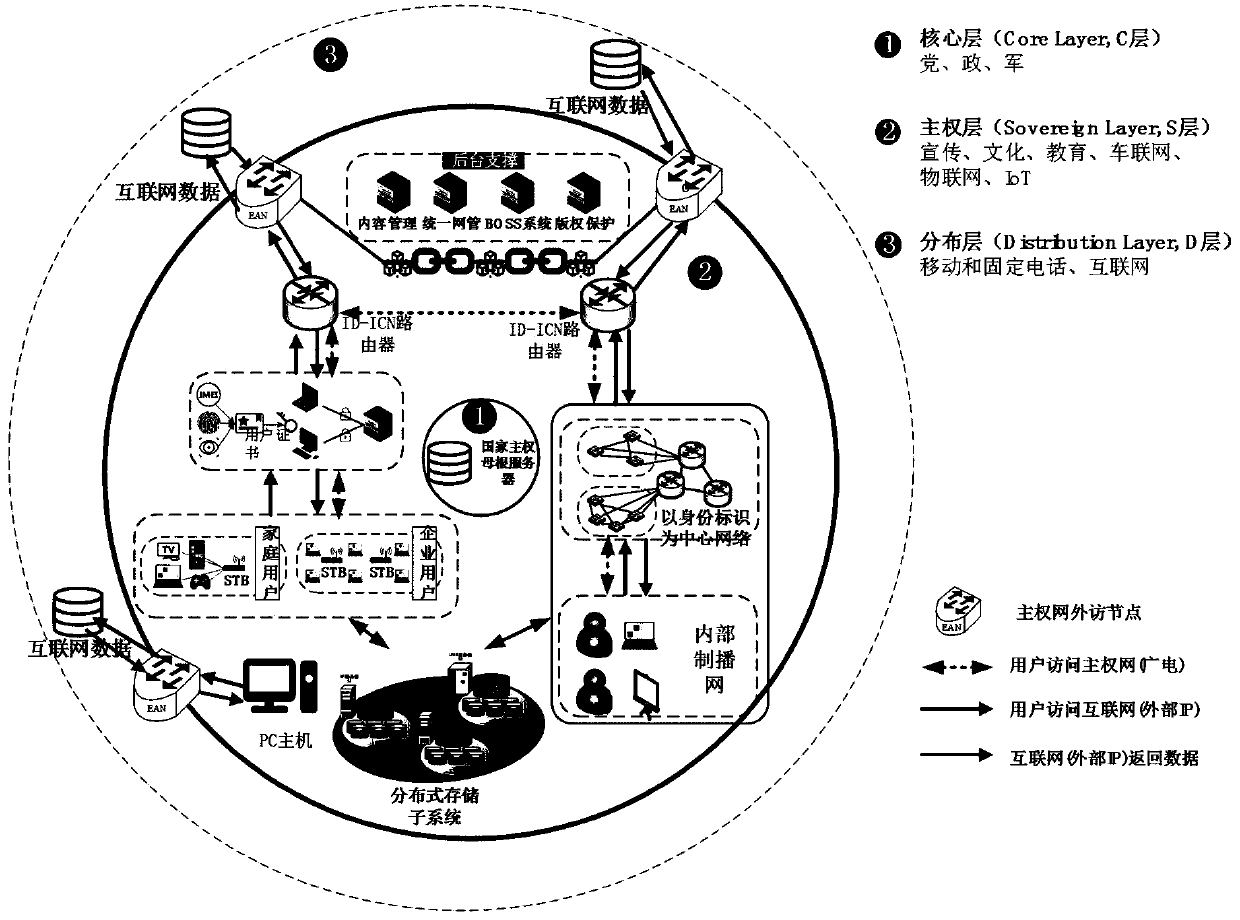
[0089] A network hierarchical management scheme bound with identity marks is proposed, which solves the problem of current network content management confusion. The hierarchical management scheme not only promotes the dissemination of information, but also eliminates the influence of traditional media on inappropriate information for minors to a certain extent.
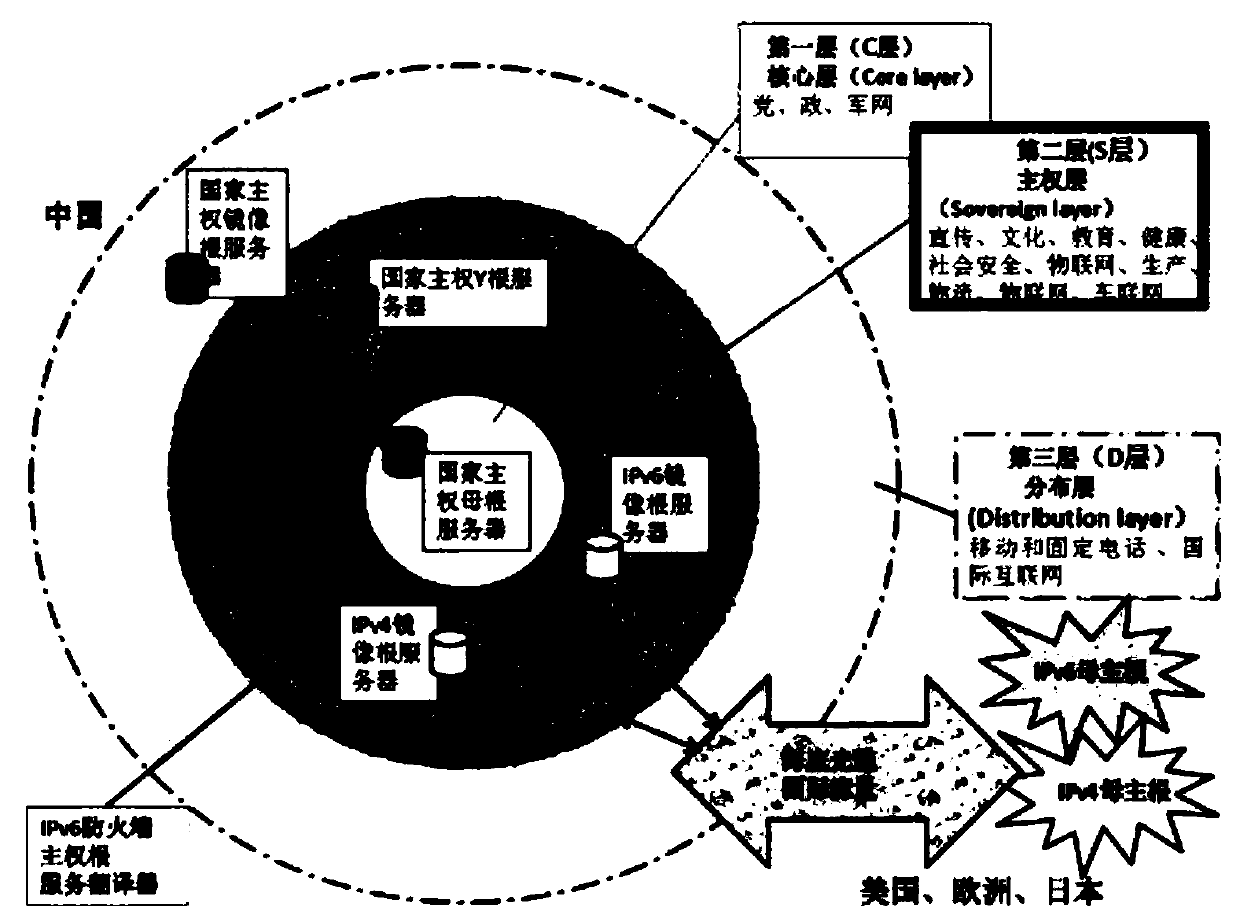
[0090] The sovereign network internally uses identity identifiers for routing, and its name space has no upper limit in principle, avoiding the problem of exhaustion of IPv4 addresses. The network pays more attention to the storage of network resources or users rather than traditional network resources, avoiding the performance problems of traditional IP networks.
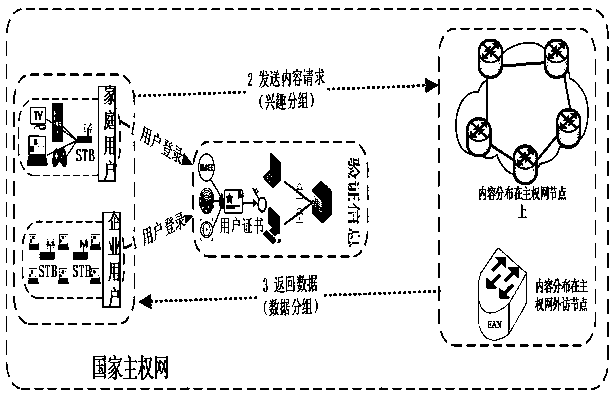
[0091] Such as figure 1 As shown, the post-IP sovereign network system framework provided by the present invention is sufficient, and the equipment in the post-IP sovereign network system framework adopts a novel network centered on identity identificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com