Video analysis device, server, system and method for protecting identity privacy
A video analysis and server technology, applied in the field of privacy protection, can solve the problems of not considering the privacy leakage risk of encoded data, ignoring context information, and high complexity, so as to ensure stability, reduce storage and computing resources, and improve training efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
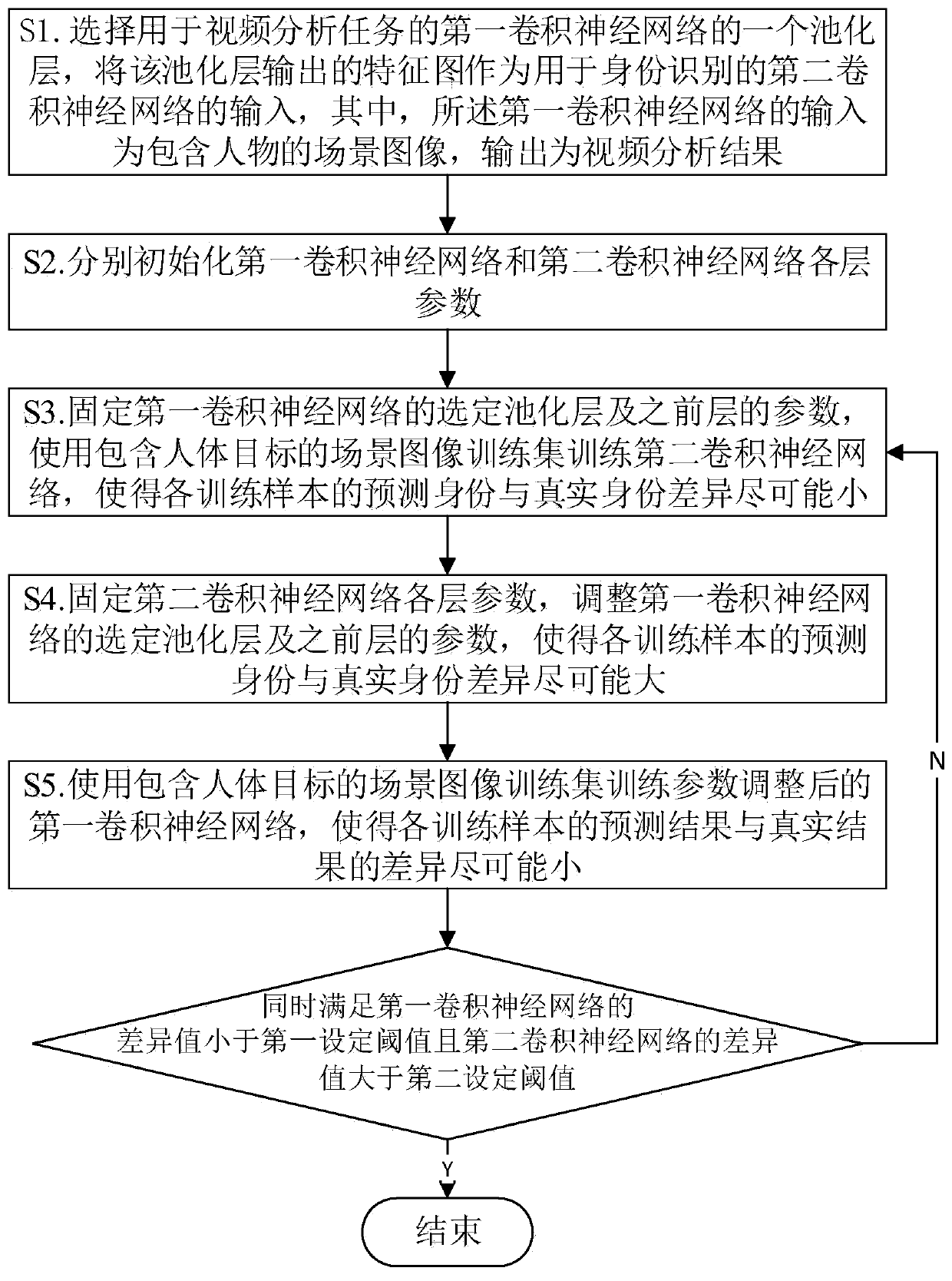
[0069] In this embodiment, for the first convolutional neural network and the second convolutional neural network constructed based on AlexNet, ImageNet image data can be used to pre-train parameters. The specific implementation method is:
[0070] Build an AlexNet network for image classification, and use the AlexNet network to complete image classification tasks on a large-scale ImageNet dataset. In order to make the pre-training parameters have good versatility, the most common 1000 category images are selected from ImageNet as the training set to train AlexNet. When the AlexNet training on the ImageNet dataset is completed, the parameters of some layers are assigned to the first convolutional neural network and the second convolutional neural network to complete the goal of initializing with pre-trained parameters. Specifically, the first convolutional neural network conv1 to mpool3 layers are initialized using the parameters of the corresponding layer of AlexNet pre-trai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com