Host operation instruction exception identification method and system
An operation instruction and host operation technology, which is applied in the field of abnormal identification of host operation instructions, can solve the problems of large time complexity, difficulty in obtaining the distribution function of data in advance, low efficiency, etc., and achieves high computing efficiency and improves object recognition accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
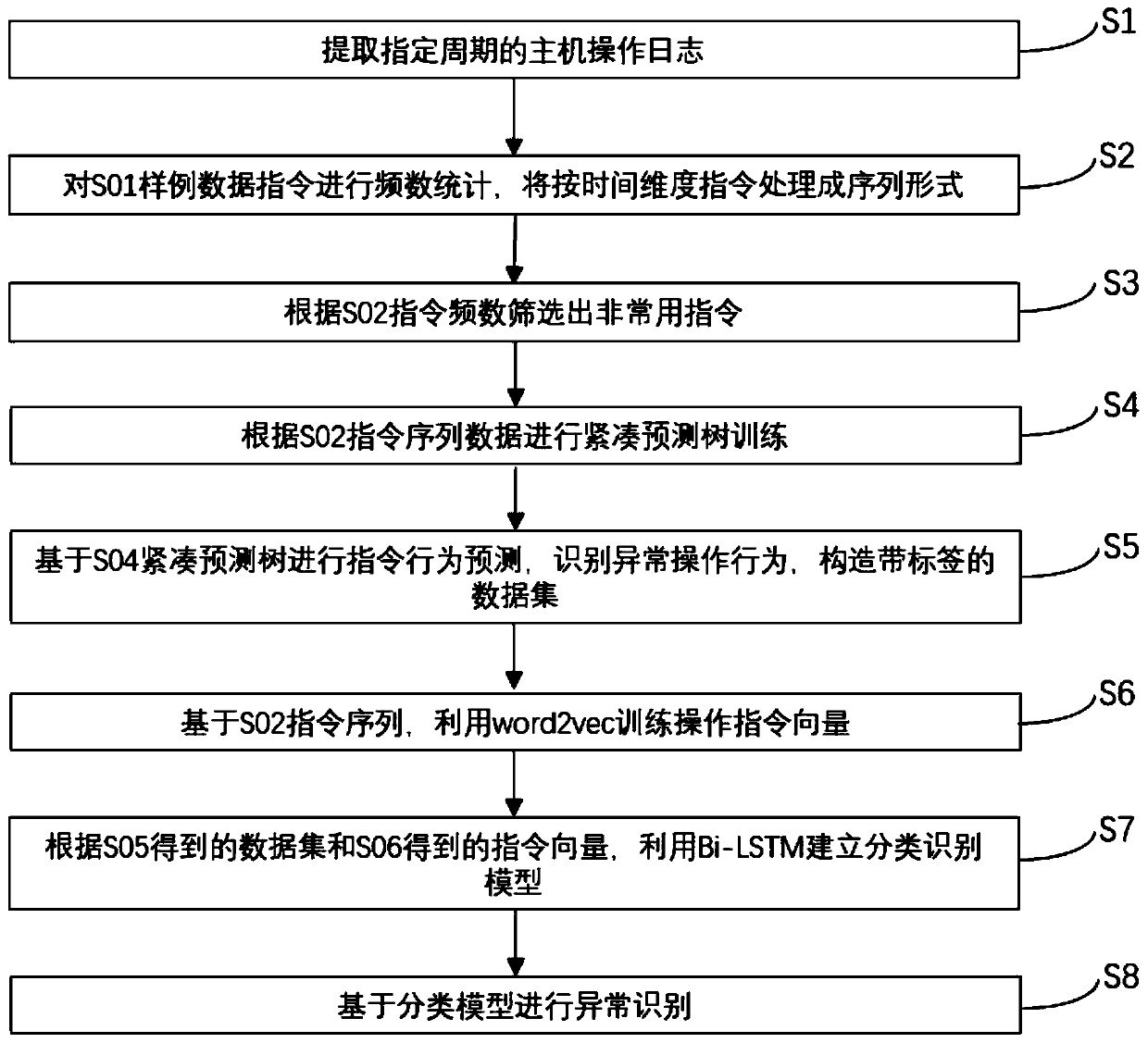
[0067] Such as figure 1 As shown, this embodiment provides a method for identifying abnormality of a host operation instruction, including the following steps:
[0068] S1: Sample data extraction
[0069] Extract a certain quarter (or a specified time period (month, year, etc.)) system operation instruction log data as the original sample data.
[0070] S2: Data processing
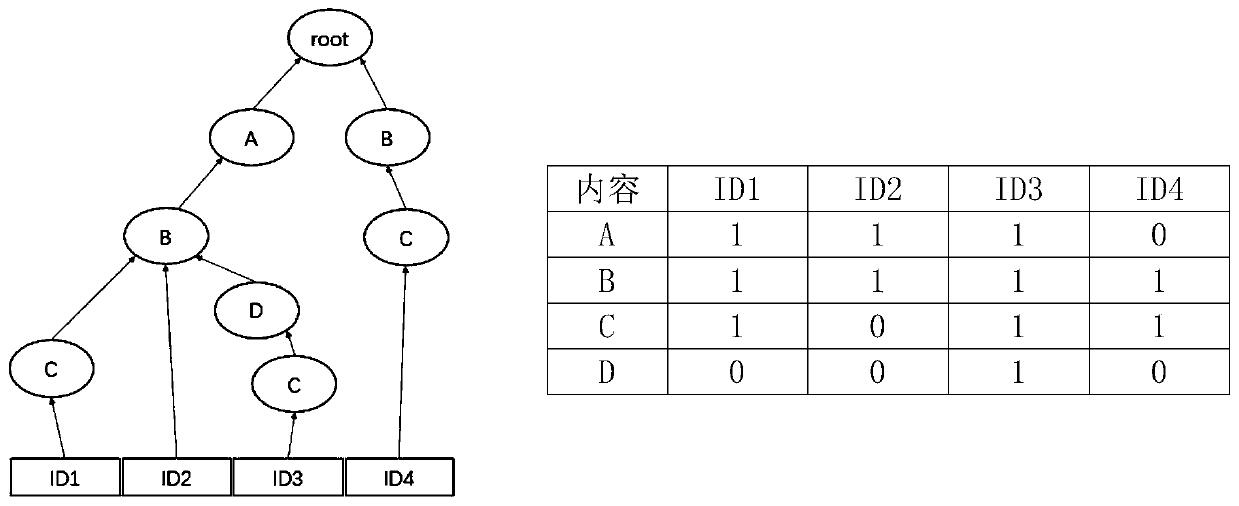
[0071] Based on the sample data extracted by S1, it is distinguished by month, and processed into a user host account as the ID, and the monthly and ID form a unique index, and the commands are arranged in chronological order, and the combined command behavior forms a behavior sequence record, such as 6m; root ;cd,mv,cp,ls,ls,rm,...,reboot;
[0072] According to the data obtained by S1, count the usage frequency of each host operation command.
[0073] S3: Screening of uncommon commands
[0074] According to the frequency of operation instructions obtained by S1, arrange them in ascending order, and u...
Embodiment 2
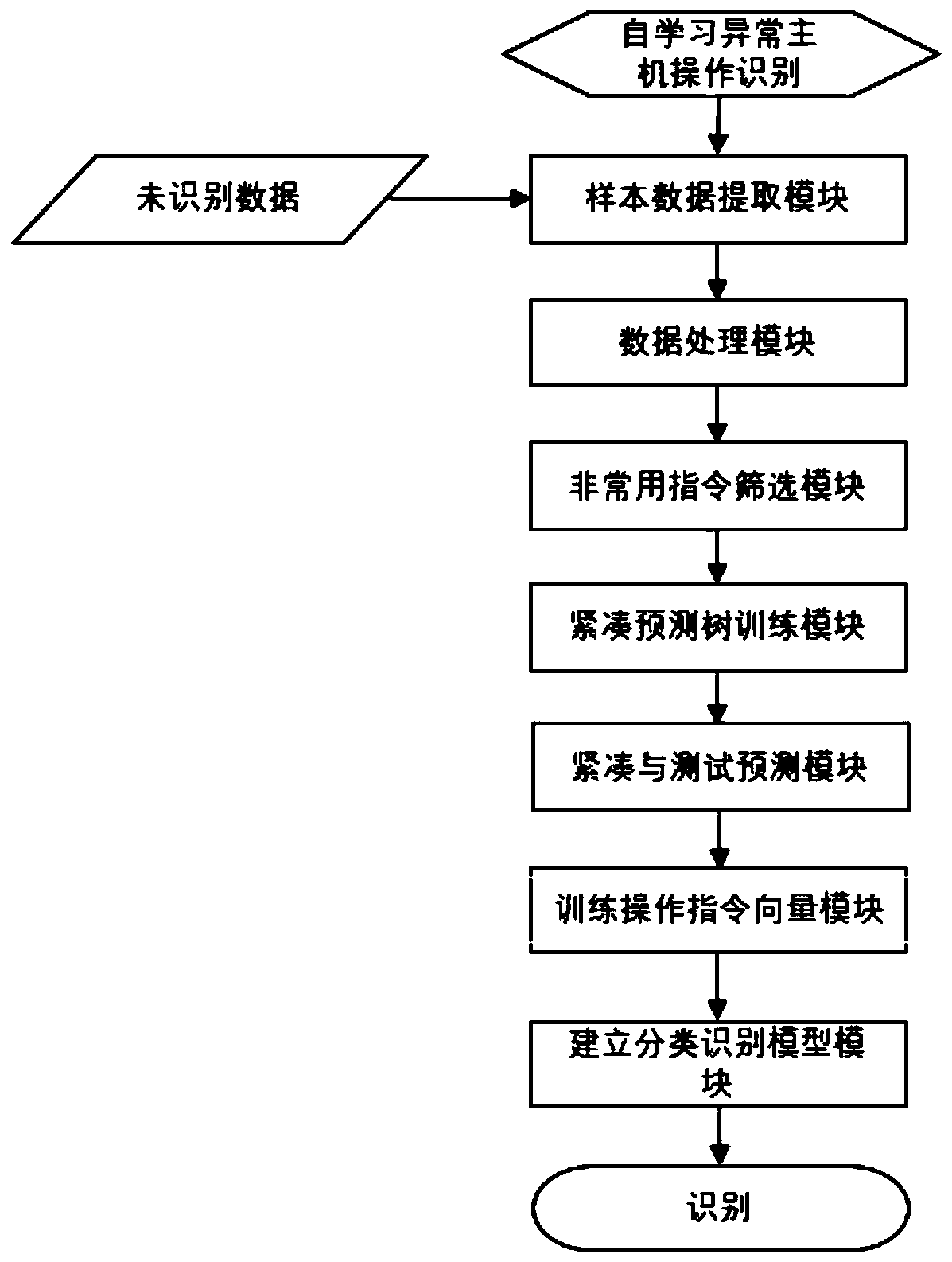
[0112] Such as image 3 As shown, corresponding to Embodiment 1, this embodiment also provides a system for identifying abnormalities in host operation instructions, including
[0113] The sample data extraction module extracts the system operation instruction log data of a specified time period as the original sample data;
[0114] The data processing module, based on the sample data, is distinguished by the set period, and processed into the user host account as the ID, the set period and the ID form a unique index, the instructions are arranged in chronological order, and the combined instruction behavior forms a behavior sequence record.
[0115] According to the sample data, count the usage frequency of each host operation command;
[0116] The non-common instruction screening module arranges the frequency of operation instructions in ascending order, and uses the quantile feature to filter out the operation instructions that are less than the set threshold from the sort...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com