Data security implementation method and related equipment
A technology of data security and implementation methods, which is applied to secure communication devices, data exchange networks, data exchange through path configuration, etc., and can solve problems such as IPSec static deployment not applicable to 5G networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] Figure 6 A schematic flow diagram of the method for implementing data security provided by Embodiment 1 of the present invention, as shown in Figure 6 As shown, the method includes:
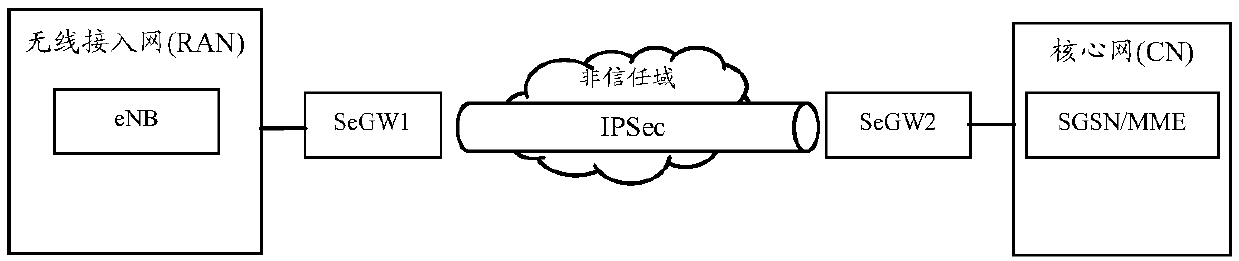
[0056] Step 601, the first security gateway function on the access network side obtains first information, and the first information includes at least one of the following: the IP address of the network element on the access network side, the network topology on the access network side information;
[0057] Step 602: According to the first information, the first security gateway function negotiates with the second security gateway function on the core network side to establish an IP security tunnel IPSec.
[0058] Wherein, the first information obtained by the first security gateway function includes:
[0059] The first topology management function TMF on the access network side acquires and saves the first information;
[0060] The first TMF acquires address information of the first...
Embodiment 2
[0092] Figure 7 A schematic flow diagram of the method for implementing data security provided by Embodiment 2 of the present invention, as shown in Figure 7 As shown, the method includes:
[0093] Step 701, the second security gateway function on the core network side obtains second information, the second information includes at least one of the following: the IP address of the core network side network element, the network topology of the core network public network element domain Information, network topology information of network slicing;
[0094] Step 702: According to the second information, the second security gateway function negotiates with the first security gateway function on the access network side to establish an IP security tunnel IPSec.
[0095] Wherein, the second security gateway function acquires second information, including:
[0096] The second topology management function TMF on the core network side obtains and saves the second information;
[00...
Embodiment 3
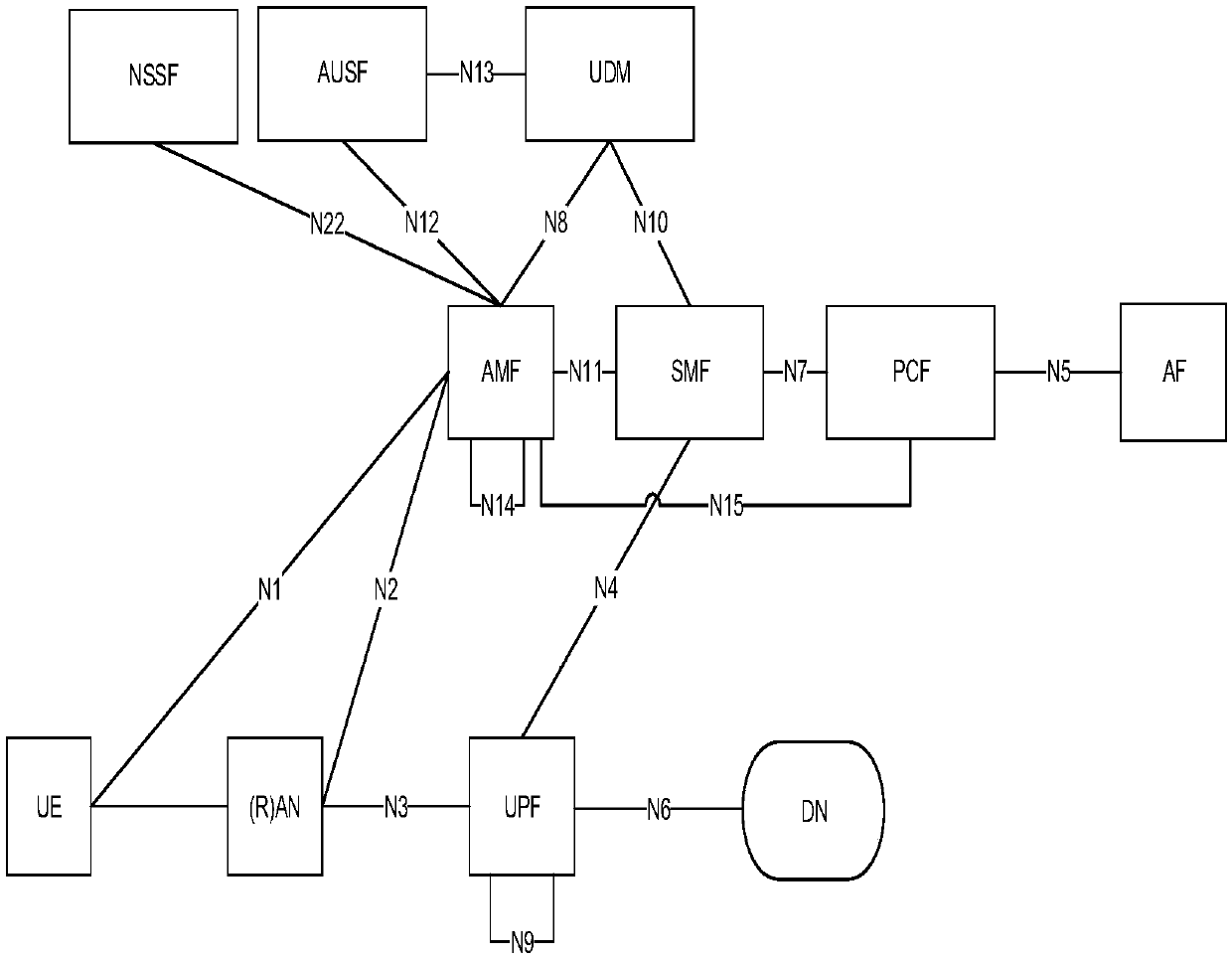
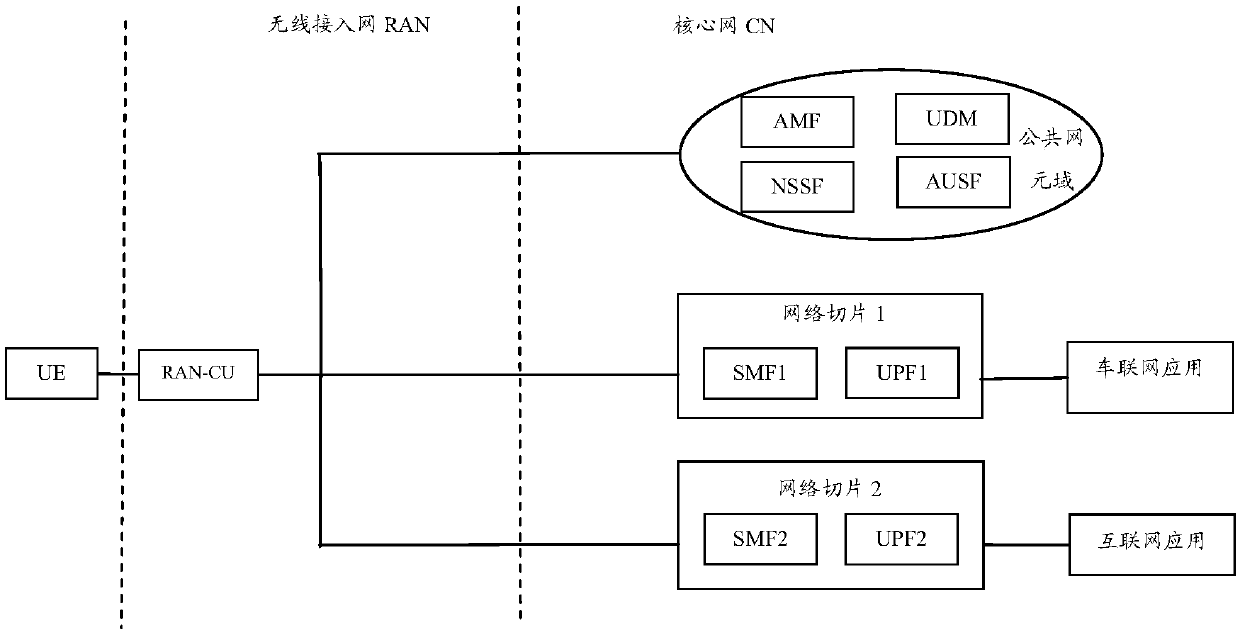
[0129] Embodiment 3 is applied to a communication system including functions such as communication function, security gateway function and topology management function (Topology Management Function, TMF). Among them, the communication function is the wireless access network and functional network elements in the 5GCN network, such as CU, AMF, etc.; the security gateway function is the IPSec tunnel endpoint, which is used to perform IPSec protection on the interactive data between communication functions; the topology management function It is used to manage the network topology, such as the networking structure between network elements and the IP address segment used by the network or the IP address of each communication function in the network. In the communication system, the first network includes at least a first communication function, a first security gateway function, and a first topology management function; the second network includes at least a second communication fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com