Interface authentication method suitable for multiple frameworks and multiple platforms
An authentication method and multi-platform technology, which is applied in the field of digital information transmission, can solve the problems of encryption algorithm development language and system limitations and emergencies that cannot be handled, and achieve the effect of preventing brute force cracking and reliable interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
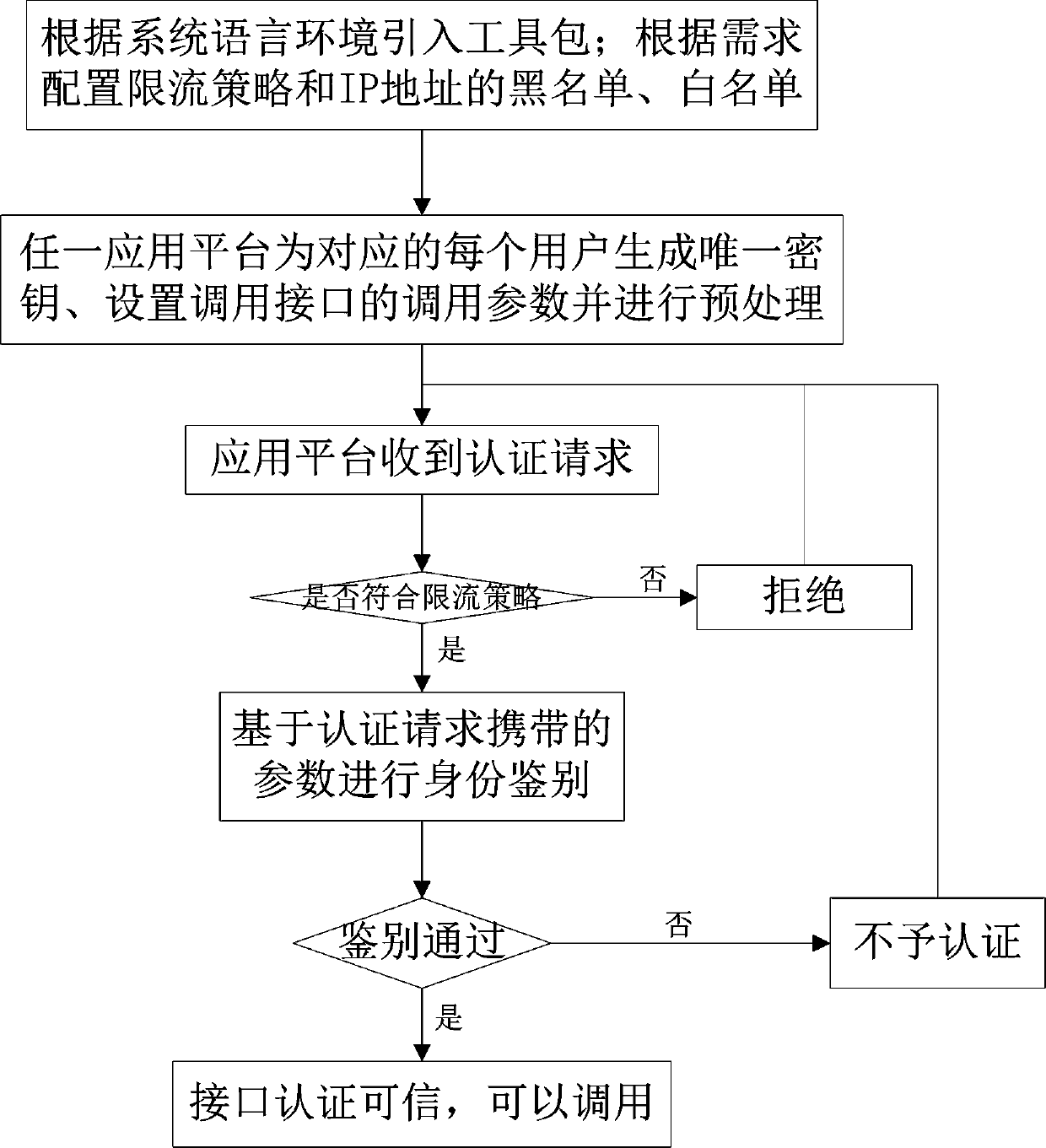
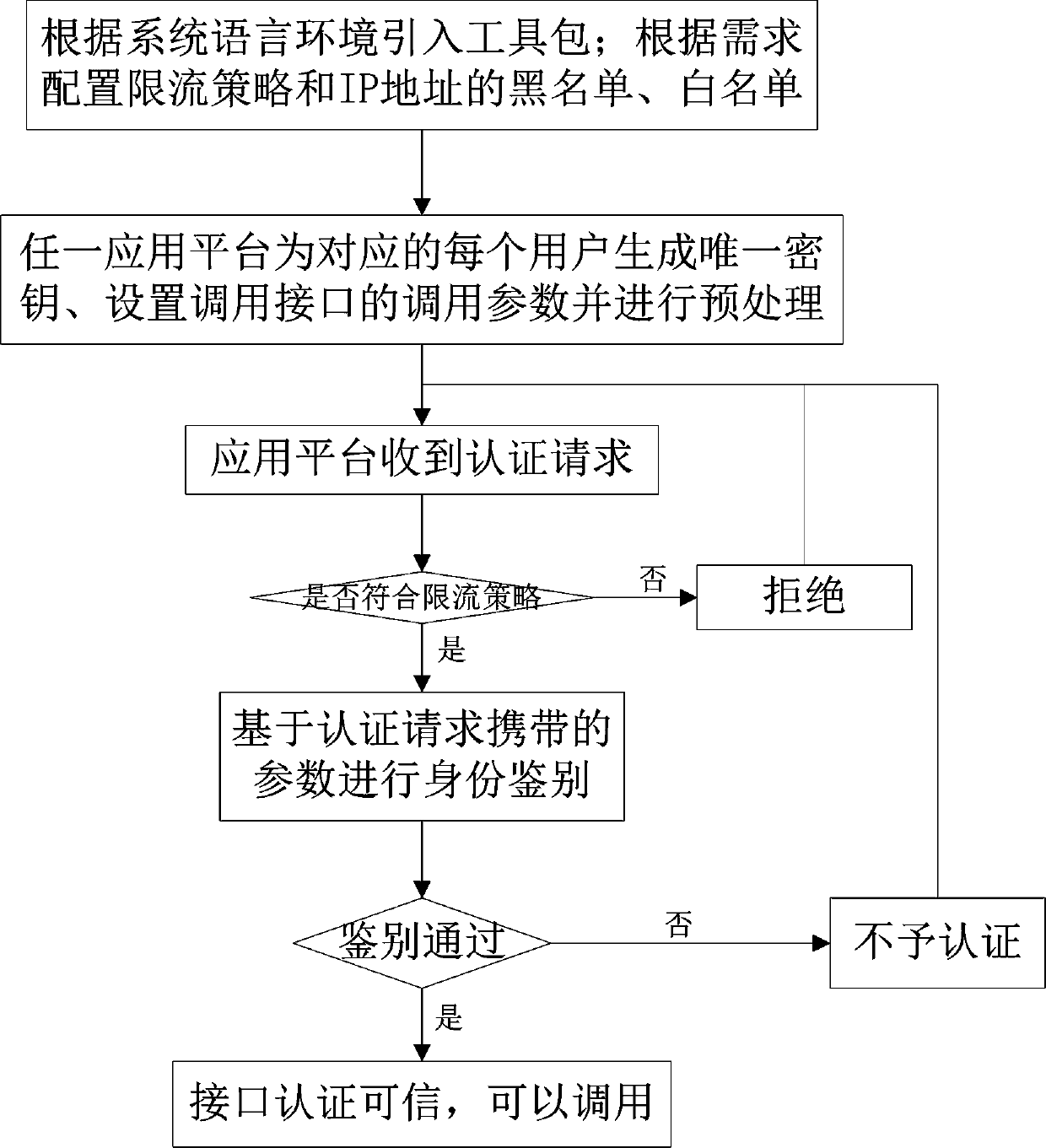
[0041] The invention relates to an interface authentication method applicable to multiple frames and multiple platforms, and provides an identity authentication using a toolkit whose encryption algorithm is a national secret commercial encryption algorithm and whose secret level is commercial secret level as an interface for each platform or frame.
[0042] In the present invention, the encryption and decryption algorithm includes services such as asymmetric encryption algorithm key pair generation, symmetric data encryption algorithm key generation, true random number generation, signature verification, etc. Equipped with an encryption algorithm, the efficiency is guaranteed under the premise of authentication security.
[0043] In the present invention, the RSA asymmetric encryption algorithm is u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com