Method and system for authenticating UE during interoperation from EPS to 5GS
A 5GS and interoperable technology, applied in the field of interoperability between EPS and 5GS, can solve the problems of waste of air interface resources, increase module coupling, etc., achieve the effects of reducing coupling, ensuring network security, and reducing message length
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
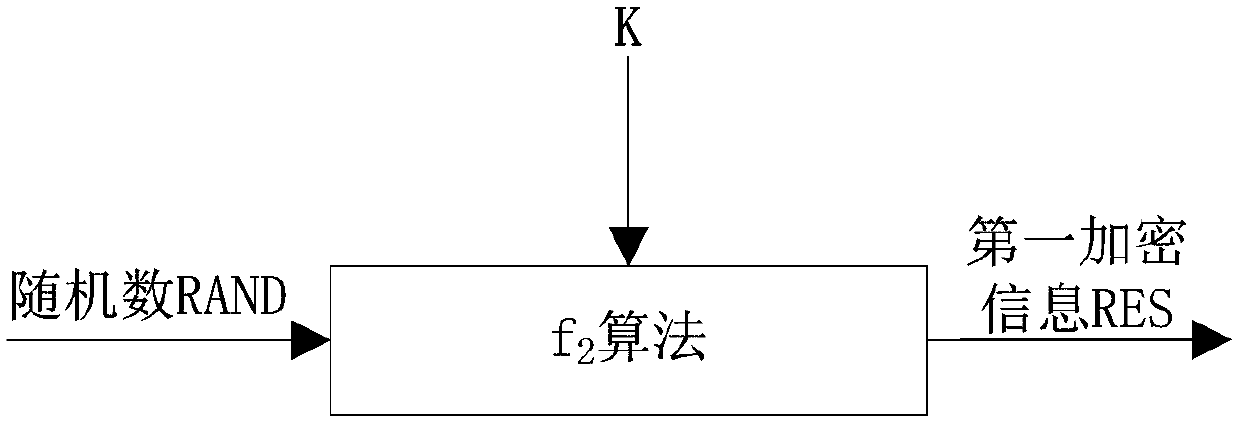
[0058] Optionally, as in figure 2 As shown, in this embodiment, the UE mainly carries the first source information and the encrypted information in the registration request message, or only carries the encrypted information; then the MME decrypts the encrypted information in the same way after receiving it, and performs Compare and verify, if they are consistent, the UE is successfully authenticated.
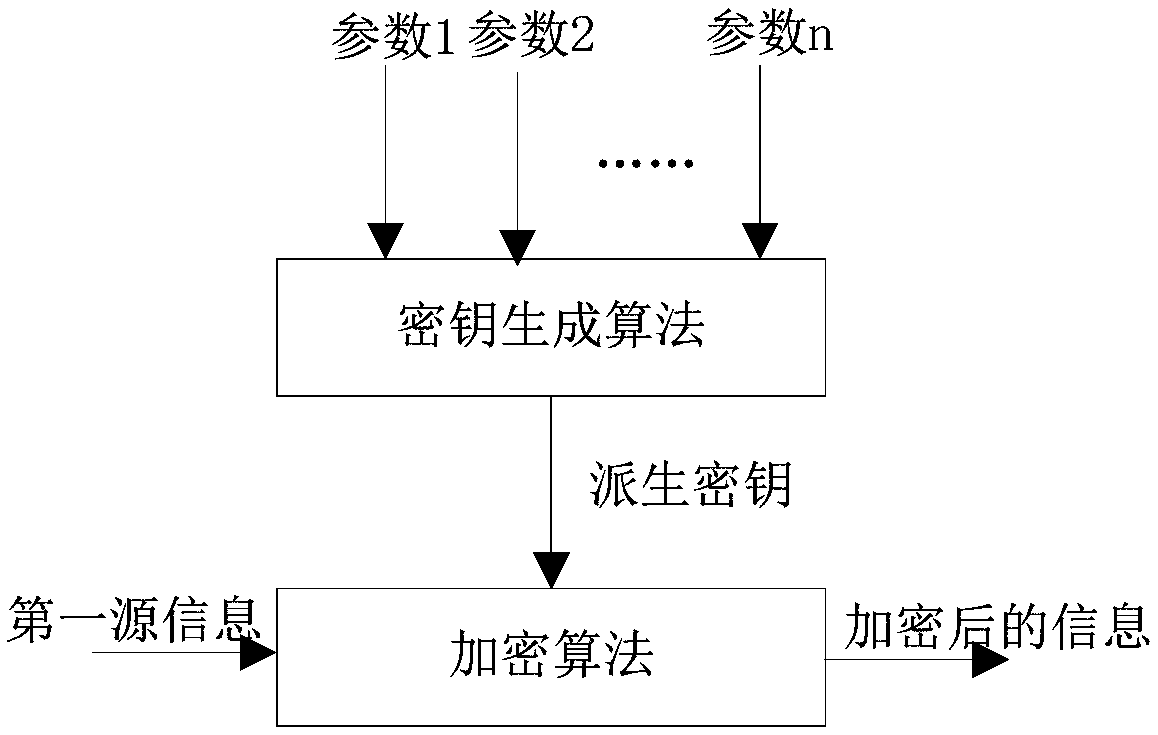
[0059] Wherein, the encrypted information can be derived by presetting the derived key, or using a key generation algorithm to generate a derived key for encryption, and the input is parameter 1 to parameter n, and the number and specific content of the input parameters can be set as required. Then, use the derived key and the encryption algorithm to encrypt the first source information, and output the encrypted information (first encrypted information RES, first encrypted information).
[0060] Optionally, the UE sending the encryption information, or the encryption informati...
Embodiment 2
[0077] Such as Figure 6 As shown, the method described in this embodiment authenticates the UE through the MME performing an integrity check on the second source information, that is, the UE carries the second source information and the MAC (the first integrity of the second source information) in the registration request message. verification result). After receiving it, the MME uses the same method to generate a MAC (second integrity check result) for the second source information, and compares and verifies it with the MAC (first integrity check result) on the UE side, and authenticates if they are consistent UE succeeded.
[0078] Optionally, sending the second source information carried by the UE in the 5GS registration request message and the first integrity check result corresponding to the second source information obtained through a preset algorithm to the MME via the AMF includes:
[0079] The random number RAND generated by the UE is used as the second source info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com