Cloud protection log system and working method thereof
A working method and log technology, applied in the field of information security applications, can solve real-time, reliability and scalability limitations, can not effectively improve system performance, lack of cloud protection log system and other problems, to achieve performance improvement, good real-time , the effect of ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
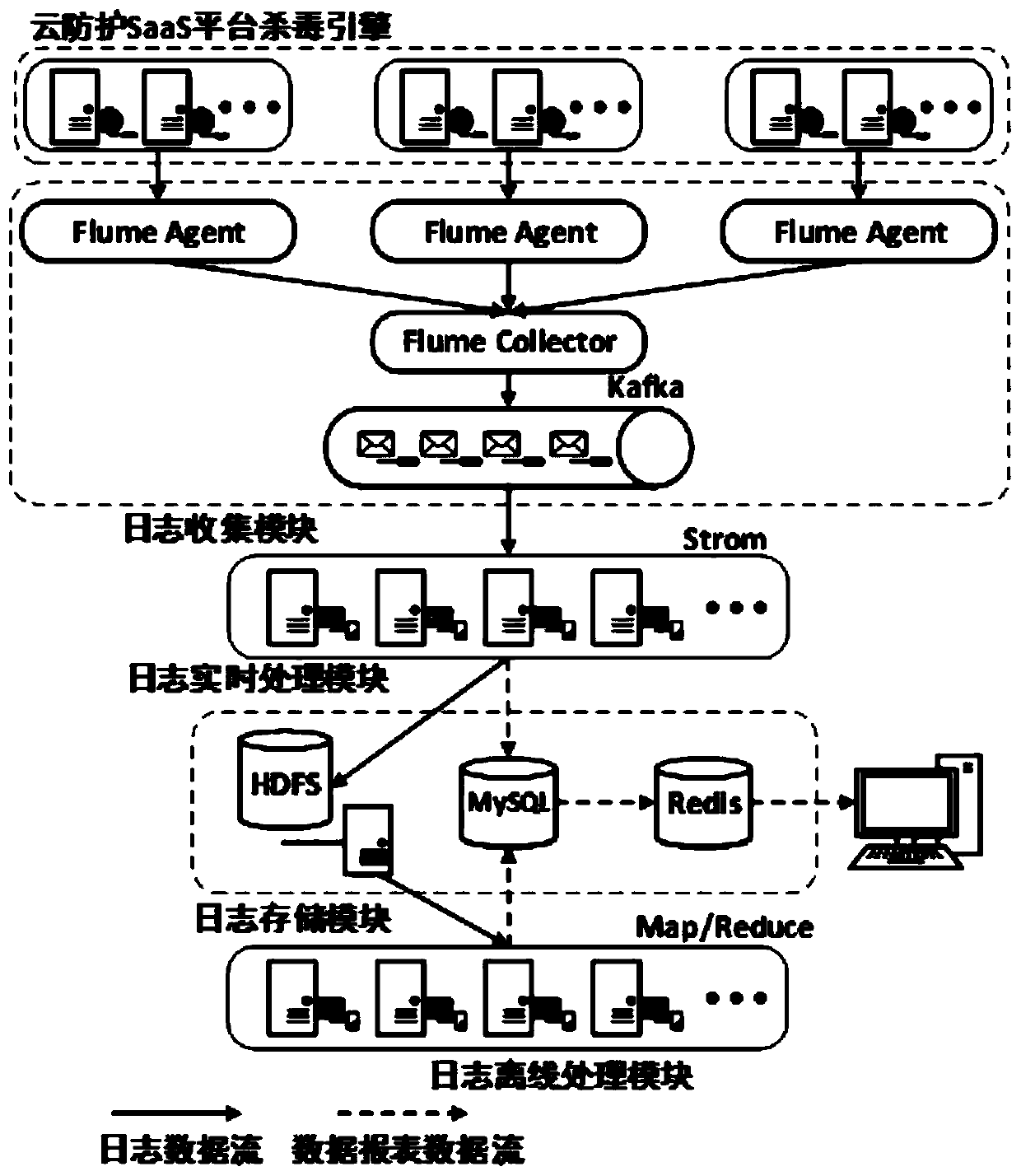
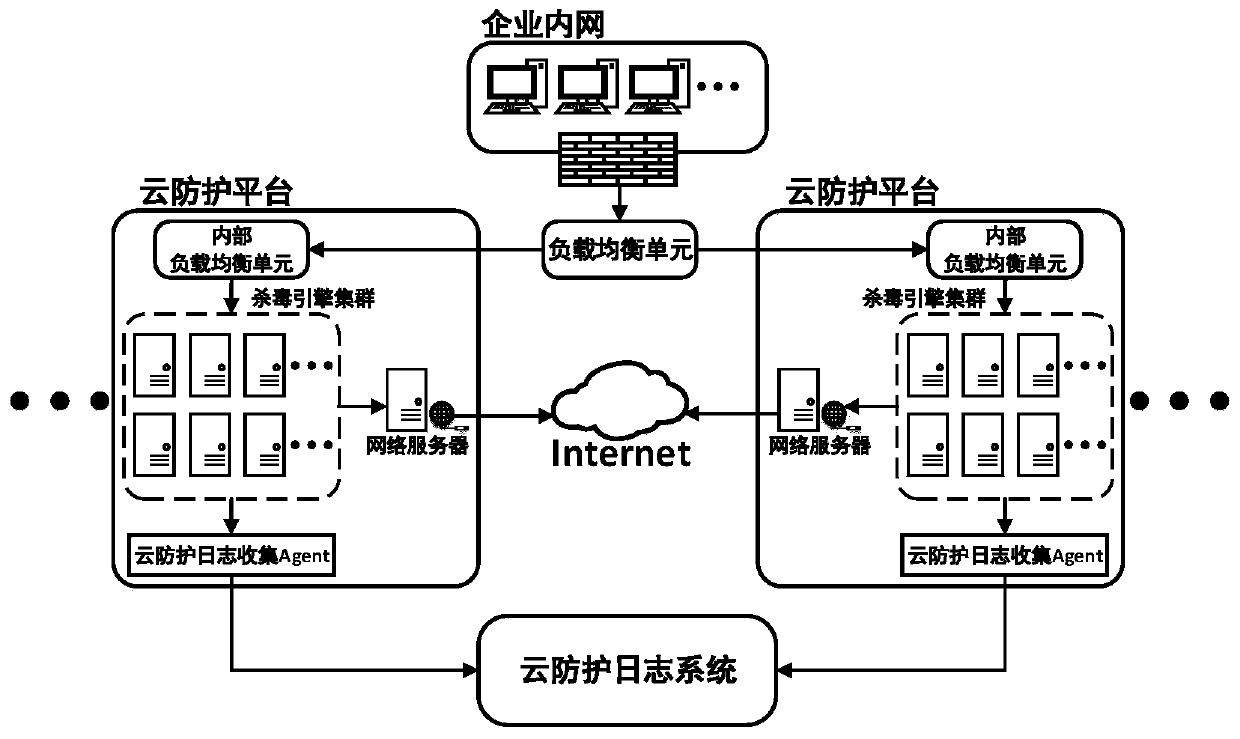
[0031] A cloud protection log system and its working method, such as Figure 1-2 As shown, the system includes a log collection module, a log processing module and a log storage module. The log collection module is responsible for collecting and aggregating the log data generated by the antivirus engine cluster under the cloud protection platform, and then sending the log data to the log processing module for real-time processing; After the real-time processing is completed, the log processing module stores the log data in the log storage module; after that, the log processing module performs offline processing on the log data in the log storage module; the data reports generated by real-time processing and offline processing in the log processing module will be stored into the log storage module; the log collection module includes the log collection system Flume and the message queue Kafka, and Flume includes the Flume Agent responsible for collecting log data and the Flume Co...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap