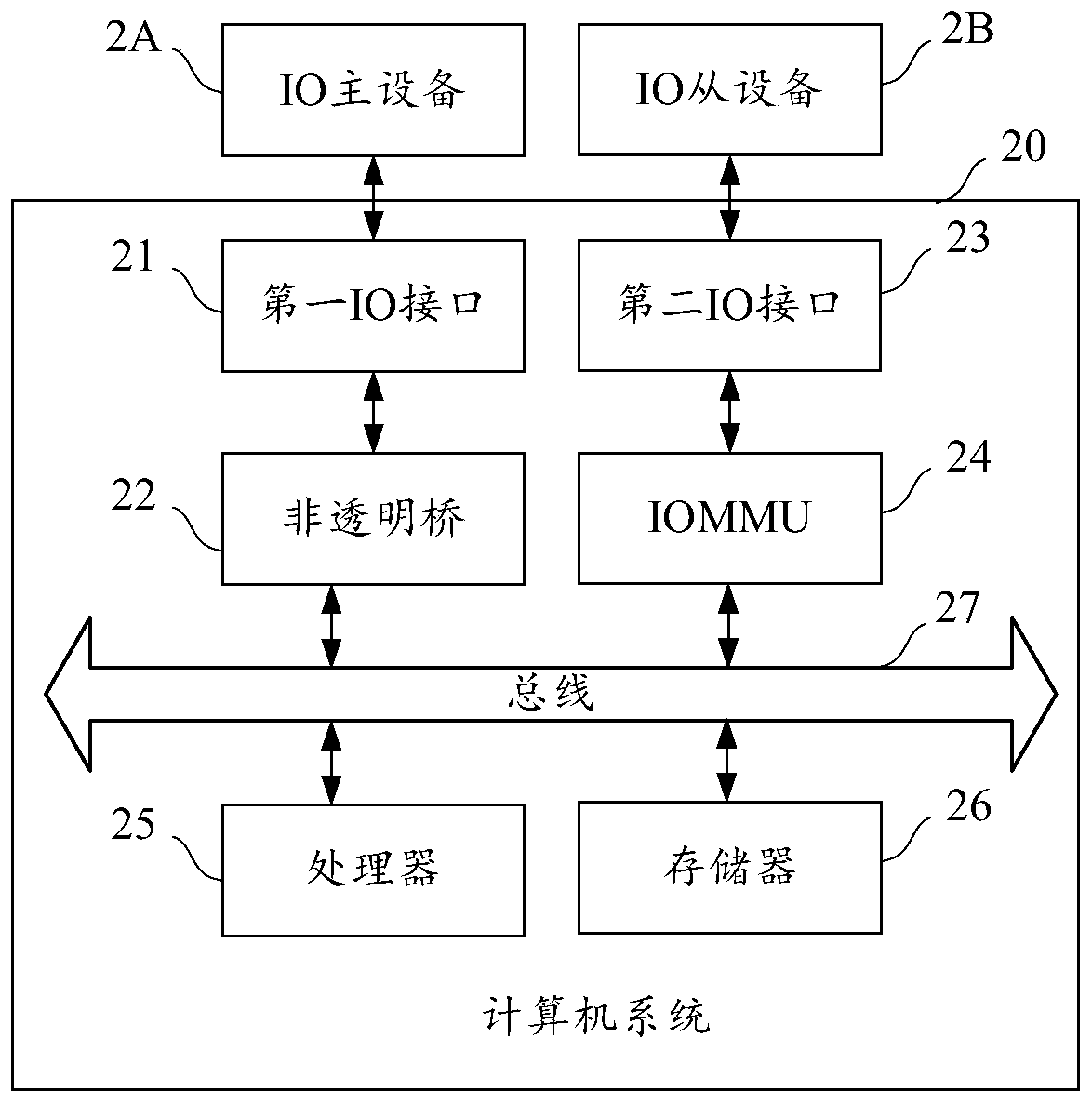
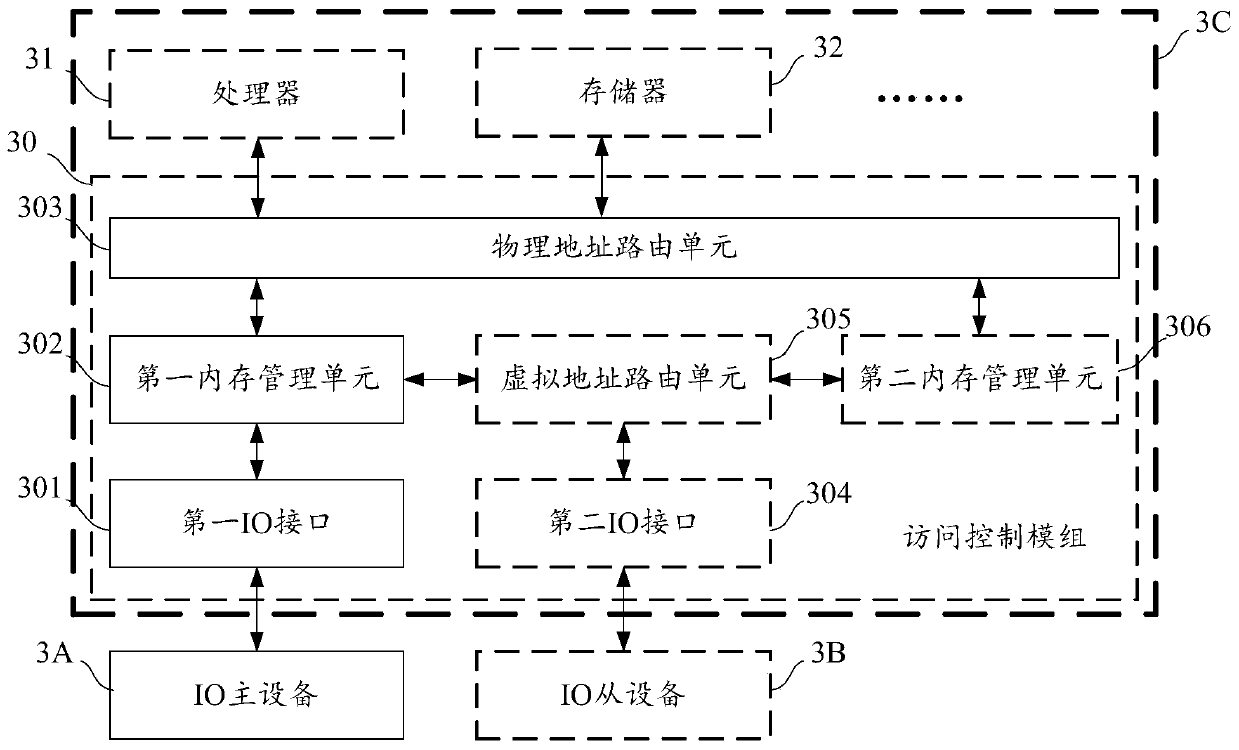
Access control module, virtual machine monitor and access control method
An access control and virtual machine technology, applied in the computer field, can solve problems such as increasing processor load, reducing the data exchange efficiency between IO master devices and computer systems, and limited address translation space for non-transparent bridges
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
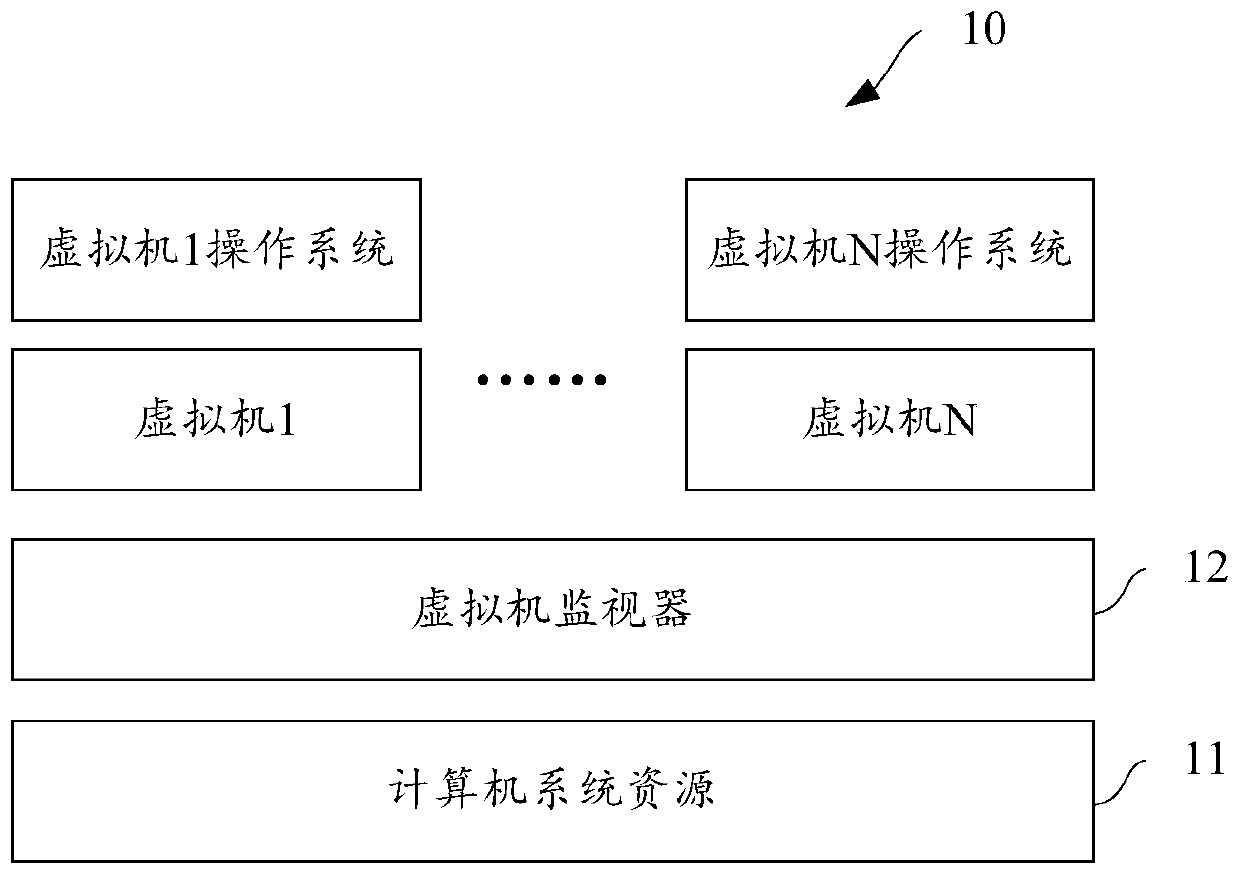
[0060] A virtual machine (Virtual Machine, VM) refers to a complete computer system that is simulated by software and has complete hardware system functions and runs in a completely isolated environment.
[0061] Such as figure 1 As shown, it is a schematic diagram of a hierarchical structure of computer system virtualization in the embodiment of this specification, wherein the computer system 10 includes: computer system resources 11, and virtual machines 1-N running on the computer system. The corresponding virtual machine operating systems can run on ~N respectively, that is, the virtual machine 1 operating system to the virtual machine N operating system. The virtual machines 1-N share the underlying computer system resources 11 through a virtual machine monitor (Virtual Machine Monitor, VMM) 12, and the virtual machine monitor can monitor the behavior of the virtual machines 1-N to realize the resource sharing between the virtual machines 1-N. isolation, so that no confl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com