Video steganography method, system and device based on macro block complexity
A technology of video steganography and complexity, applied in the field of image information hiding, can solve the problems of bit growth, characterization of reconstruction blocks, algorithm security discount, etc., to achieve simple algorithm information extraction, good resistance to steganalysis, and efficient information extraction. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035]The present invention will be described in detail below in conjunction with the accompanying drawings.
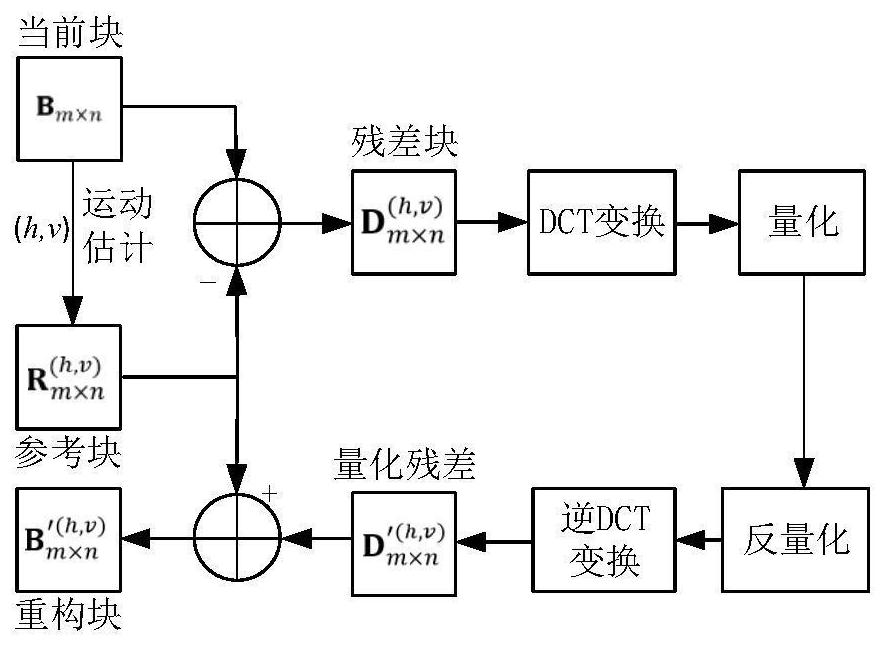
[0036] Such as figure 1 As shown, it is a flow chart of video inter-frame compression. The video is divided into macroblocks of the same size, and then each macroblock is traversed. The encoder will search for the best match of the current block in the reference frame and According to the relative relationship between the position of the current block and the position of the best matching block, the motion vector is obtained, and the corresponding pixels of the current block and the best matching block are subtracted to obtain the residual block, which is changed and quantized by DCT together with the reference frame information and the motion vector Write the compressed video stream, for subsequent frame reference, undergo inverse quantization and inverse DCT changes, and reconstruct with the best matching block to obtain the reconstructed block. Through the above s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com