Security service chain dynamic arrangement device
A security service and dynamic technology, applied in the field of network security, can solve the problems of non-uniform management and control interfaces of security protection equipment, lack of continuous upgrade, dynamic maintenance of security policies, dynamic deployment and adjustment of security functions on demand, and lack of technology, etc., and achieve wide application. Prospects, improve the effectiveness of security management and control, and improve the effect of flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings.
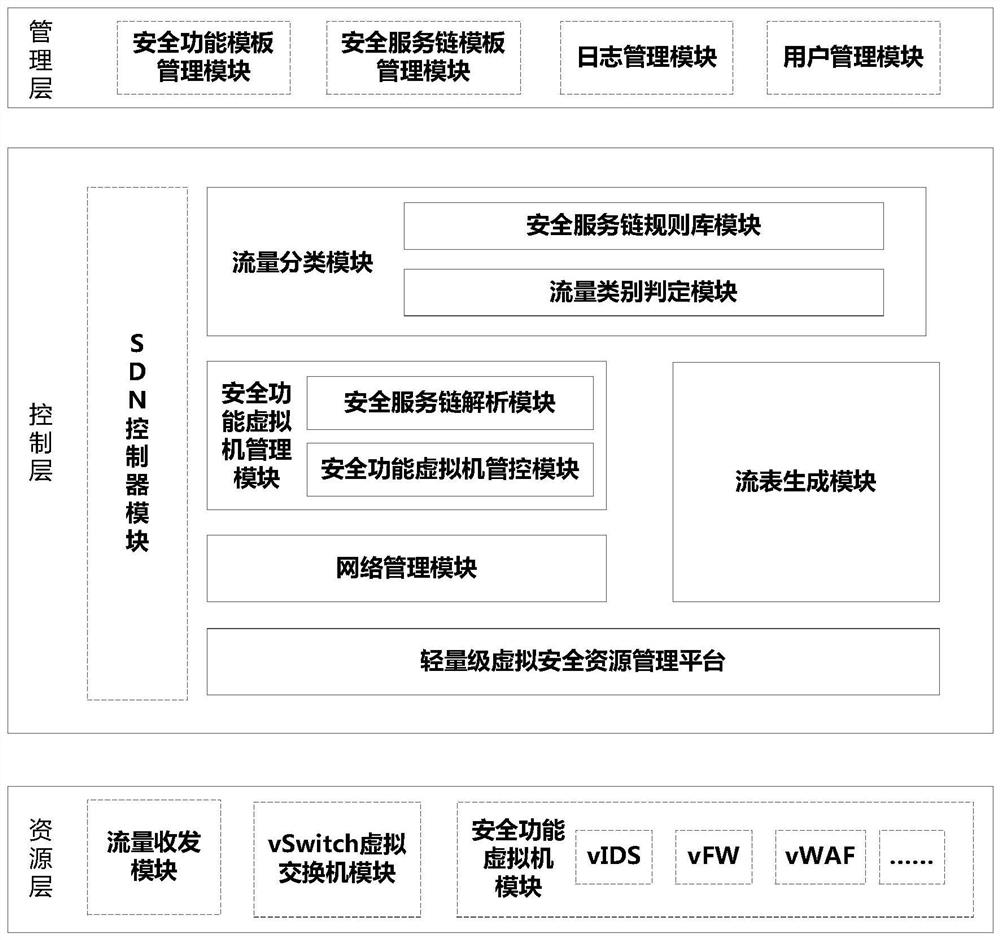
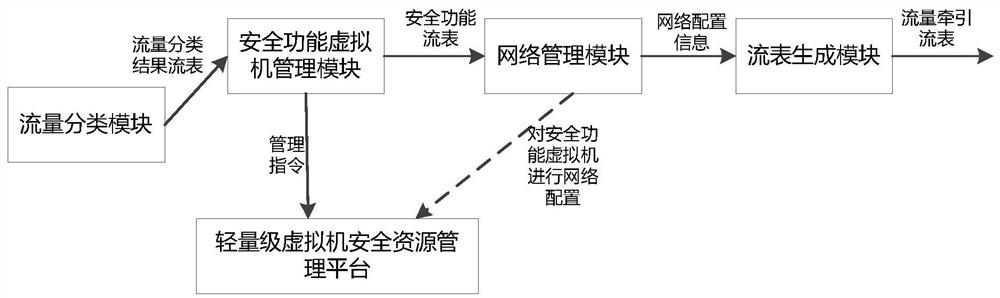
[0036] Such as figure 1 As shown, a security service chain dynamic orchestration device includes a resource layer traffic transceiver module, a vSwitch virtual switch module, a security function virtual machine module, and a security function template management module of the management layer, a security service chain template management module, and a log Management module, user management module, and SDN controller module of the control layer; in addition, the control layer also includes a traffic classification module, a security function virtual machine management module, a lightweight virtual security resource management platform, a network management module, and a flow table generation module ;in:
[0037] The traffic classification module is used to perform traffic classification according to the five-tuple information of the traffic received by the traffic tran...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com