Internet-of-Vehicles intrusion detection system based on hidden Markov model
An intrusion detection system and Internet of Vehicles technology, applied in the field of intrusion detection systems for Internet of Vehicles based on hidden Markov model, can solve the problems of Internet of Vehicles hazards, solutions are no longer easy, and Internet of Vehicles performance is different
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
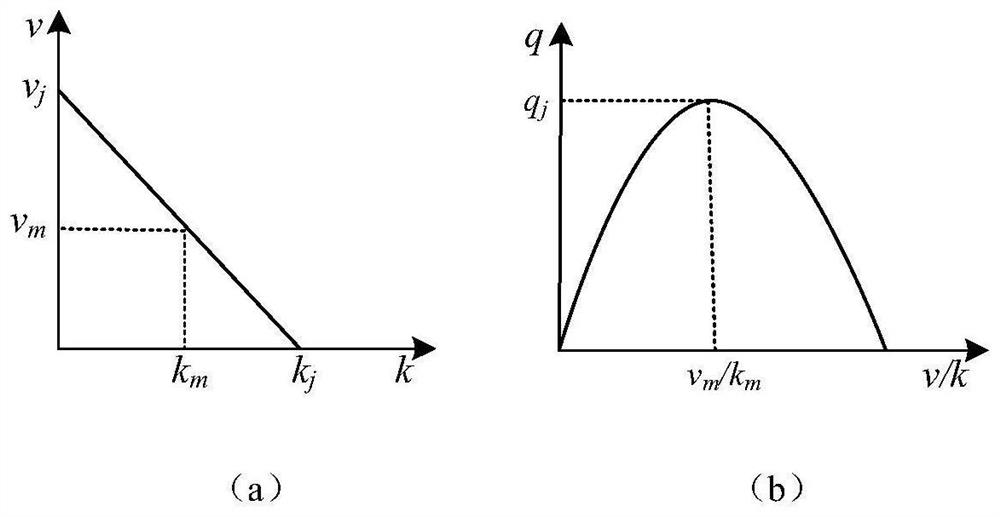
[0082] figure 2 Demonstrates the relationship between vehicle speed and density and traffic flow in the Green shield model
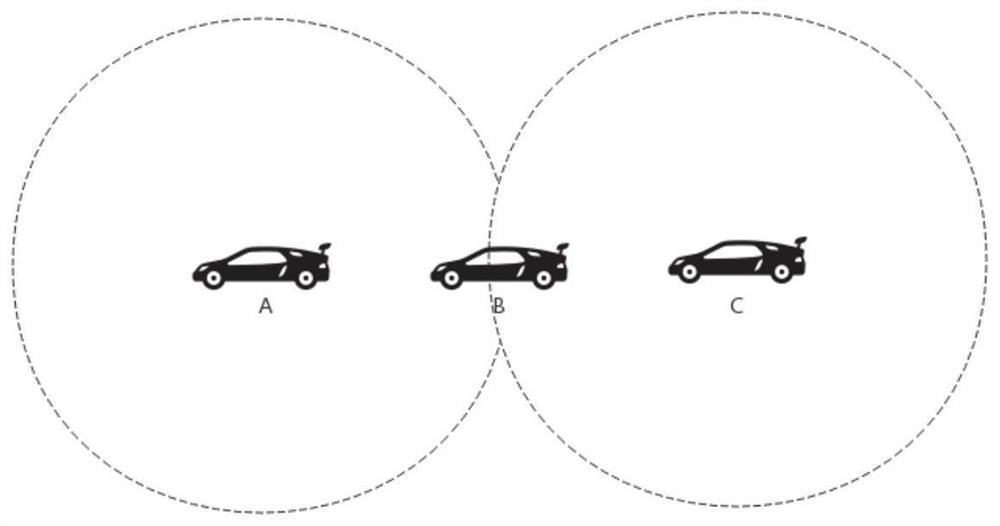
[0083] image 3 Schematic diagram of a black hole attacking vehicle
[0084] Figure 4 Shows the structure of the DNN
[0085] Figure 5 The simple and easy-to-operate system designed by the present invention is shown.
[0086] The graph structure of the hidden Markov model is as follows: Image 6 shown.
[0087] The hidden Markov model in the Internet of Vehicles proposed by the present invention is as follows: Figure 8 as shown,
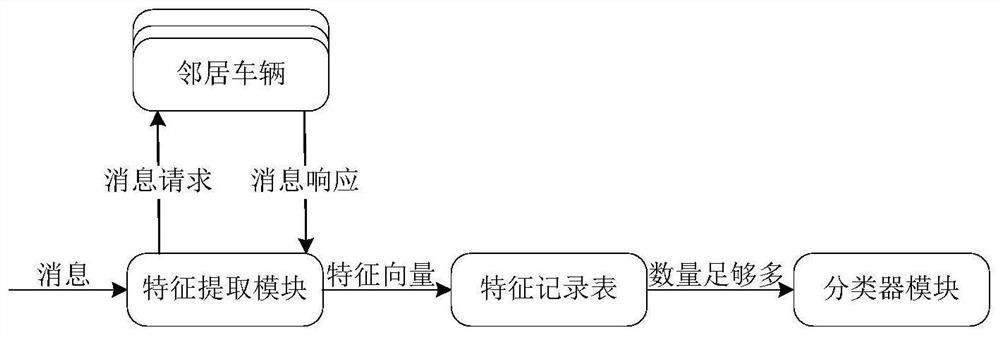
[0088] Figure 9 In the flow chart, the pre-detection module will obtain the prediction chain from the update module in real time and update it to its own prediction table. When receiving a message, the pre-detection module will judge whether the ID of the message exists in the prediction table. Update the hidden Markov model, and then judge whether the ID is a "normal" node or an "abnormal" node according to the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com