Data security audit model device and method based on knowledge graph and terminal equipment
A knowledge graph and data security technology, applied in the field of data security audit model devices based on knowledge graph, can solve the problems of low security audit efficiency, inaccurate audit results, and complex audit data.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
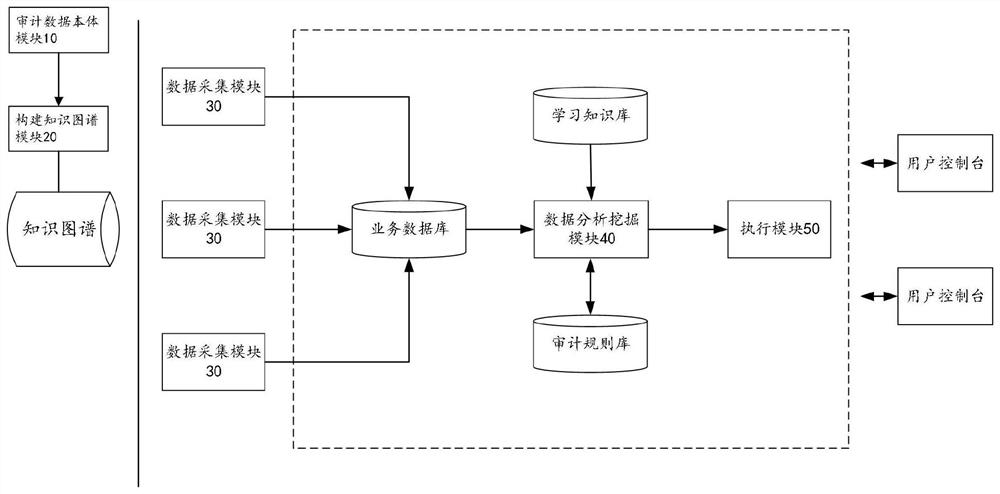
[0052] figure 1 It is a frame diagram of the data security audit model device based on the knowledge map described in the embodiment of the present invention.
[0053] Such as figure 1 As shown, the embodiment of the present invention provides a data security audit model device based on a knowledge map, including an audit data ontology module 10, a knowledge map building module 20, a data collection module 30, a data analysis and mining module 40, and an execution module 50;
[0054] The audit data body module 10 is used to obtain the first audit data from the database, and divide the first audit data into entity data and entity relationship data;
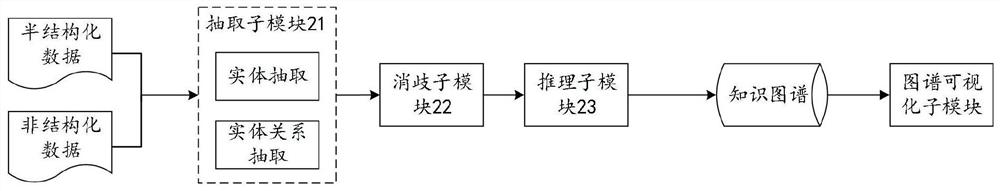
[0055] Build a knowledge map module 20, which is used to extract entities and entity relationships from entity data and entity relationship data respectively, convert unstructured and semi-structured audit data into structured data, and perform entity disambiguation on structured data , After knowledge reasoning, the knowledge ma...
Embodiment 2
[0116] Figure 8 It is a flow chart of the steps of the knowledge graph-based data security audit model method described in the embodiment of the present invention.
[0117] Such as Figure 8 As shown, the embodiment of the present invention provides a knowledge map-based data security audit model method, including the following steps:
[0118] S1. Obtain the first audit data from the database, and divide the first audit data into entity data and entity relationship data;
[0119]S2. Perform entity extraction and entity relationship extraction on entity data and entity relationship data respectively, and transform unstructured and semi-structured audit data into structured data, and perform entity disambiguation and knowledge reasoning on structured data to obtain Knowledge graph of audit data;
[0120] S3. Collect the second audit data from the knowledge map, and preprocess the second audit data to obtain audit record data;
[0121] S4. Analyze the audit record data and r...
Embodiment 3
[0126] An embodiment of the present invention provides a computer-readable storage medium. The computer storage medium is used to store computer instructions. When the computer is run on a computer, the computer executes the above knowledge graph-based data security audit model method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com