System resource anti-tampering method based on block chain and national secret digital fingerprint technology
A digital fingerprint and system resource technology, applied in the direction of digital transmission system, transmission system, digital data protection, etc., can solve the problem of inability to ensure the uniqueness and credibility of original resources, the inability to form large-scale remote monitoring, and the easy location of files Problems such as theft and exposure, to achieve the effect of improving uniqueness and credibility, improving anti-tampering and anti-repudiation performance, and avoiding repeated investment problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention is described in further detail now in conjunction with accompanying drawing. These drawings are all simplified schematic diagrams, which only illustrate the basic structure of the present invention in a schematic manner, so they only show the configurations related to the present invention.
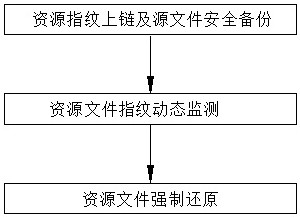
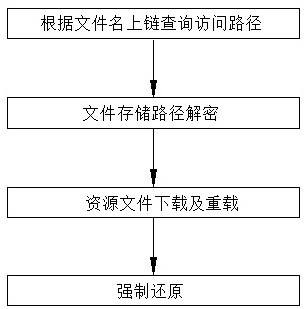
[0058] Such as figure 1As shown, the anti-tampering method of system resources based on block chain and national secret digital fingerprint technology of the present invention comprises the following steps:
[0059] Step a: Resource fingerprint on-chain and source file security backup
[0060] Step a1: File fingerprint on-chain:
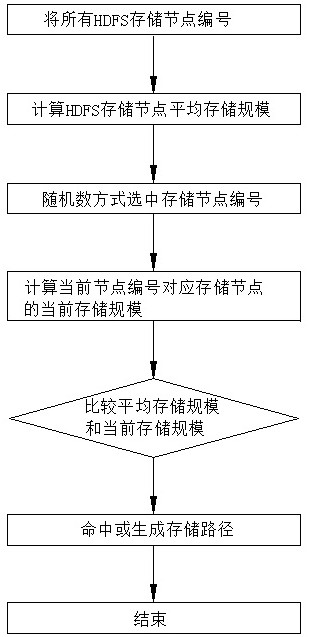
[0061] Step a1.1: Set the Genesis module in the target system to generate a policy file; the policy file includes a scanning policy file, a monitoring policy file, an identification policy file, an alarm policy file, a forced restoration policy file and a super administrator intervention policy file, The policy file is generated d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com