Method and system for constructing large-scale trapping scene based on cloud computing
A large-scale, cloud computing technology, applied in the field of network security, to achieve the effect of improving security, enhancing uniqueness, and high classification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] like figure 1 Shown, the method for constructing a large-scale trapping scene based on cloud computing, the method performs the following steps:
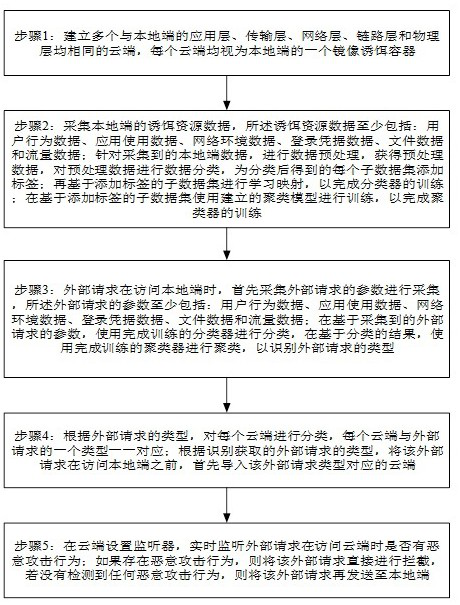
[0035] Step 1: Establish multiple clouds with the same application layer, transport layer, network layer, link layer and physical layer as the local side, and each cloud is regarded as a mirror decoy container on the local side;
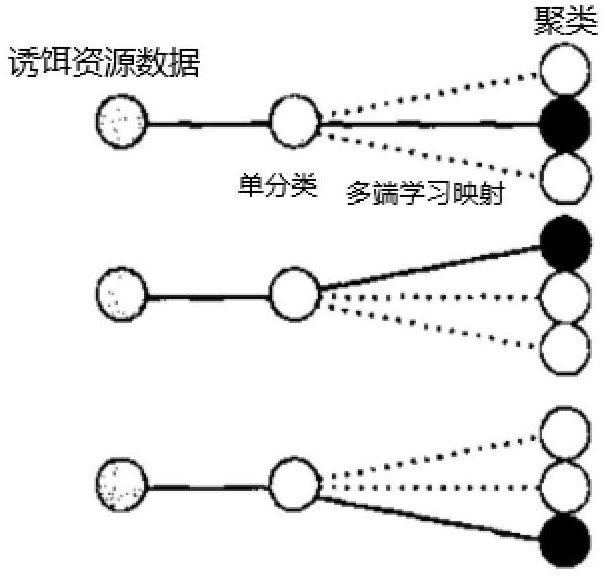
[0036] Step 2: Collect local-side bait resource data, which at least includes: user behavior data, application usage data, network environment data, login credential data, file data, and traffic data; Preprocessing, obtain the preprocessing data, classify the preprocessing data, and add labels to each sub-dataset obtained after classification; then perform learning mapping based on the sub-datasets with labels to complete the training of the classifier; based on adding The sub-dataset of the label is trained using the established clustering model to complete the training of the clusterer;
[0037]...
Embodiment 2
[0042] On the basis of the previous embodiment, in the step 1, the method of setting up the same cloud as the application layer, transport layer, network layer, link layer and physical layer of the local end performs the following steps: Execute on the remote cloud server Builder application program, the remote cloud server includes processor, memory, operating system, and storage space for storing software application program and creating cloud image; providing said software application program, which includes application program code and application program data; reading a device configuration file indicating configuration settings for use with the software application, including one or more virtual machines, class paths, and environment variable settings; receiving information about the type of manager to be used with the application instructions; write the interface device of the virtual machine that is specific to the manager type and conforms to the configuration settings...
Embodiment 3
[0045] On the basis of the previous embodiment, the method for data preprocessing in step 2 performs the following steps: for the collected local end data, remove unique attributes, process missing values and abnormal value detection and processing; and then perform data processing Reduction processing, including: removing the mean value, calculating the covariance matrix, calculating the eigenvalues and eigenvectors of the covariance matrix, sorting the eigenvalues from large to small, retaining the largest eigenvector, converting the data to a new space constructed by the eigenvector In; finally the new data after processing.
[0046] Specifically, data reduction refers to minimizing the amount of data while maintaining the original appearance of the data as much as possible (the necessary prerequisite for completing this task is to understand the mining task and be familiar with the content of the data itself). For small or medium-sized datasets, general data preproce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com