Network attack tracing method based on behavior portraits
A network attack and behavior technology, applied in the computer field, can solve the problem of defense situation lag and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
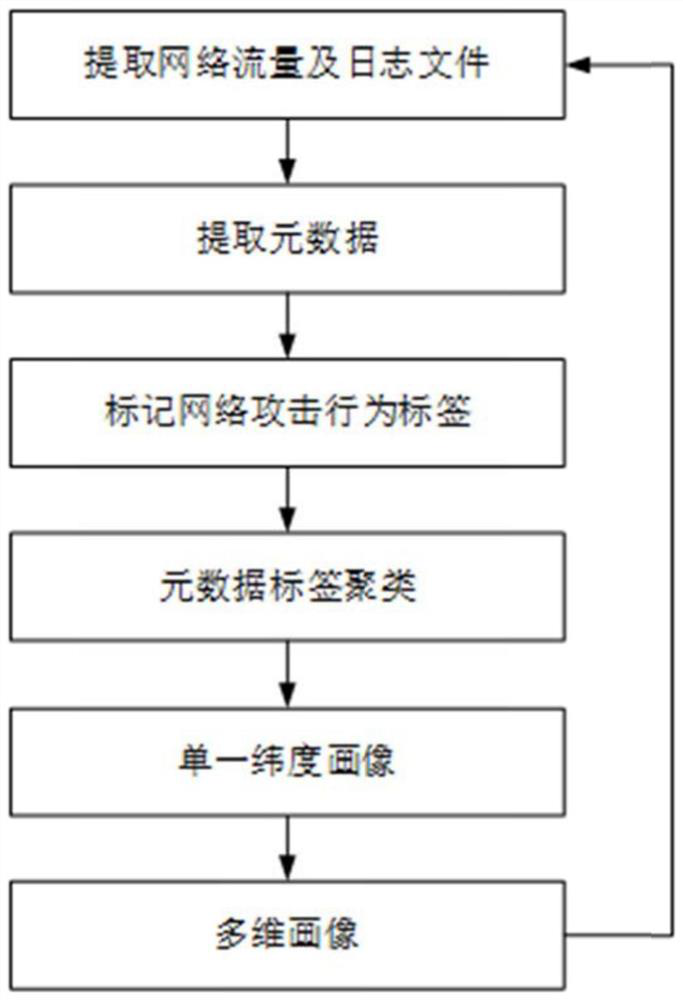
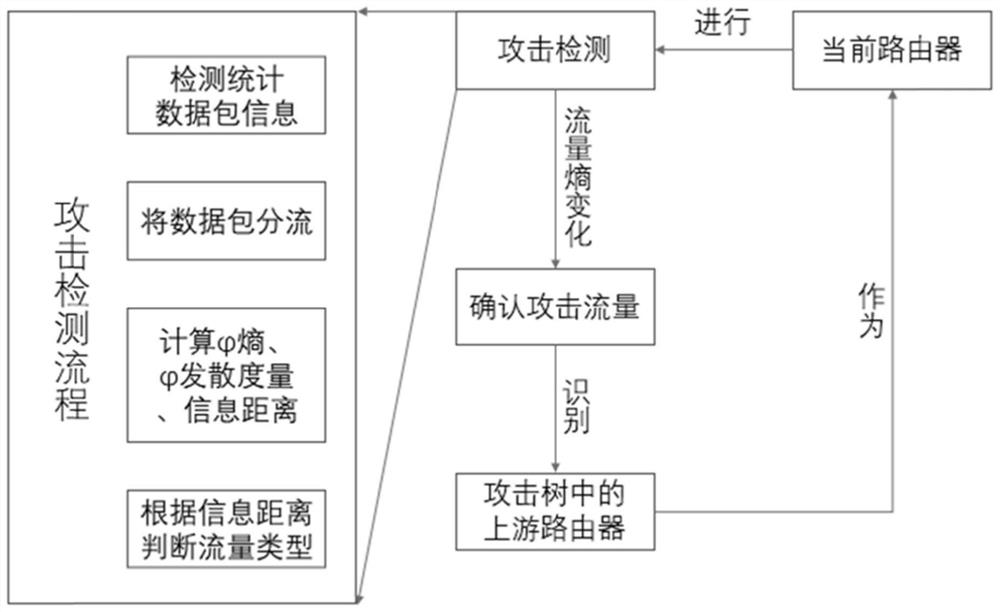
[0085] refer to figure 1 , figure 2 with image 3 , further describe the implementation steps of the present invention.
[0086] Step 1, extract network traffic and log files in real time.
[0087] (1a) Deploy a shunt at the specific port used by the business system, use port mirroring technology to bypass the business traffic, and at the same time, read the login log of the business system, firewall and IDS (Intrusion Detection System, intrusion detection system) detection log.
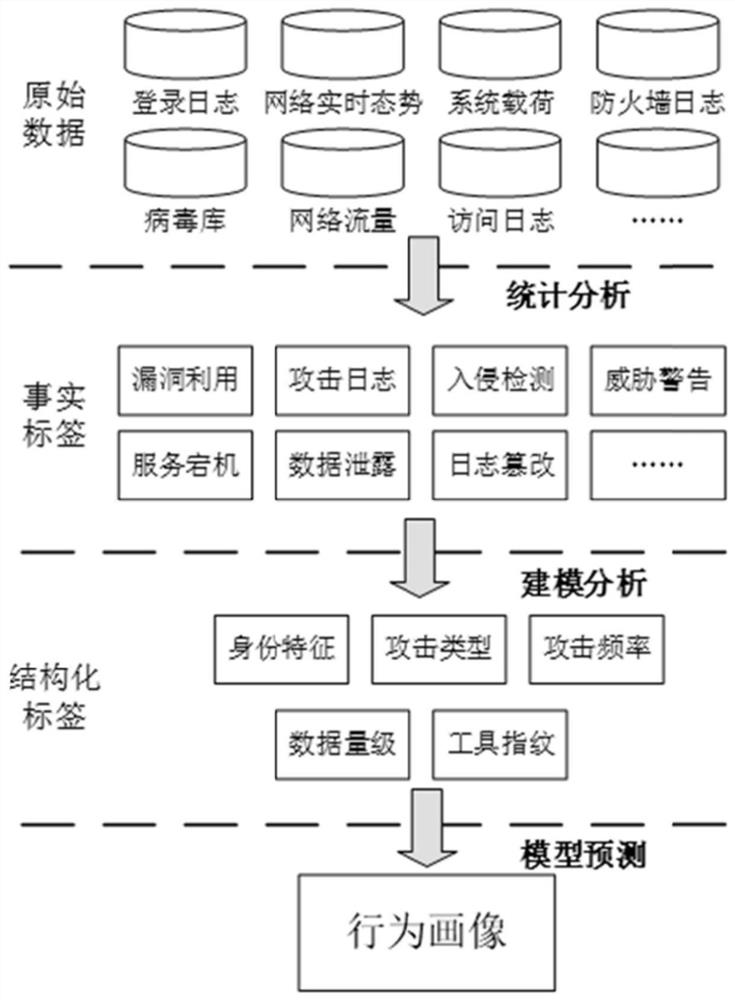
[0088] The extraction of network traffic and log files not only collects information from the current network status and traffic, but also extracts from related historical records such as access logs and firewall logs. The sources of original data include service login logs, real-time network situation data, System load, firewall log, virus database file status word, network traffic, access log, etc.
[0089] (1b) Deploy a load balancer on the periphery of the splitter in (1a), distribute a lar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com