Multi-user security energy-saving resource allocation method in mobile edge computing network
An edge computing and resource allocation technology, applied in the field of multi-user security and energy-saving resource allocation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
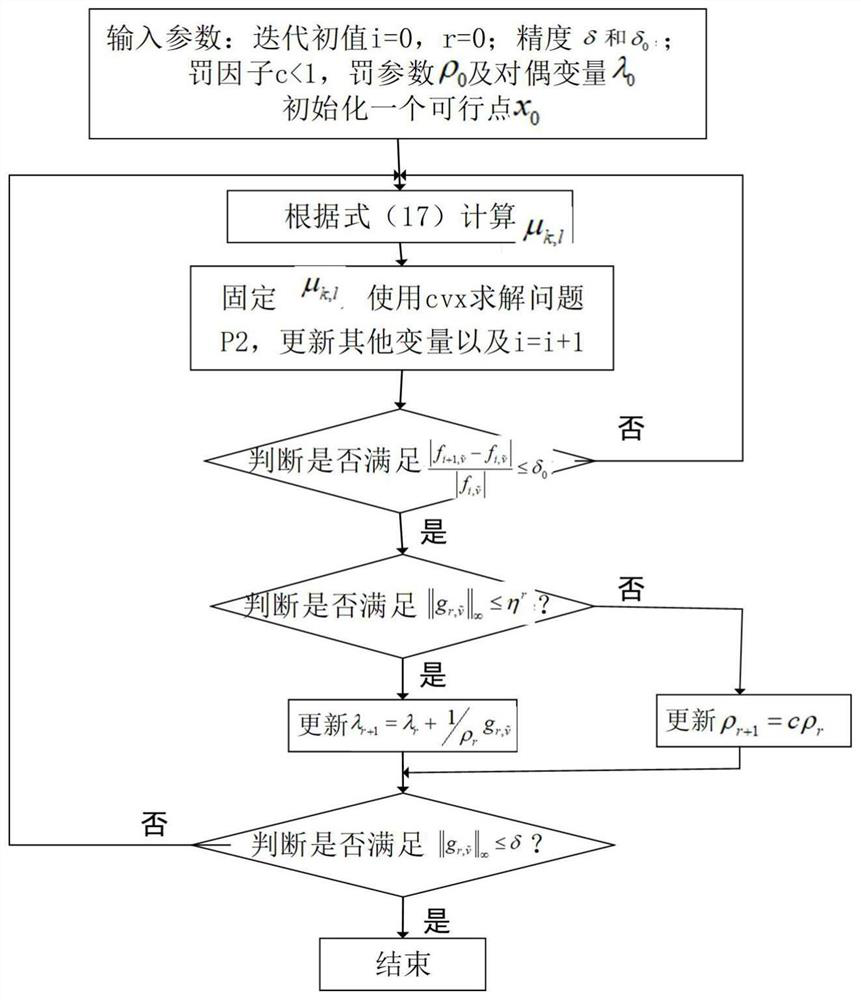
[0048] The present invention will be described in further detail below in conjunction with the accompanying drawings.
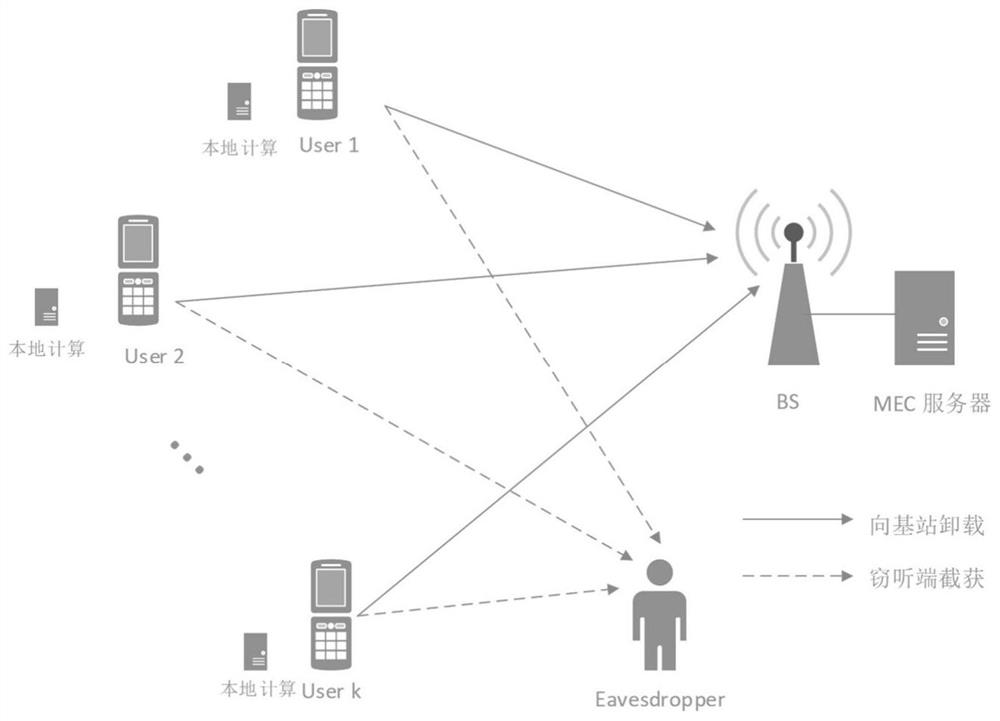
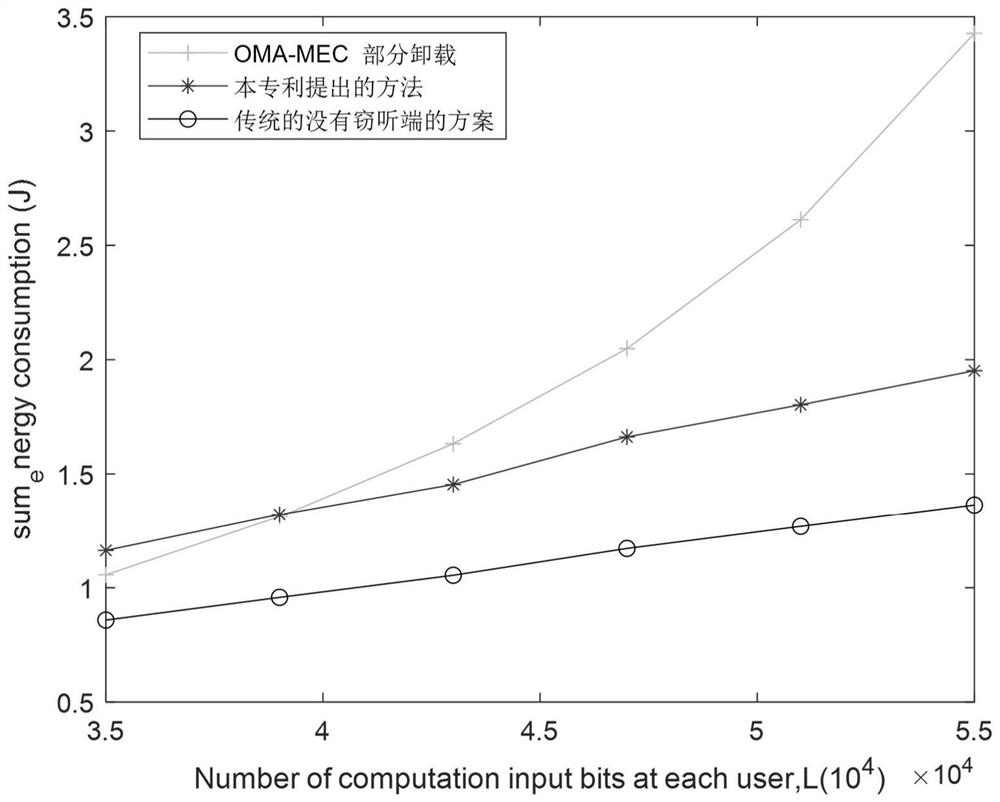
[0049] The system used in the multi-user security and energy-saving resource allocation method in the mobile edge computing network proposed by the present invention, such as figure 1 Shown:
[0050] It is assumed that there are K users who need to perform their respective computing tasks in a period T, and the task amount of each user is L k >0bits, k=1,...K.
[0051] Divide the amount of tasks corresponding to the kth user into l k and L k -l k Two parts, among them, setting l k Part of the tasks are calculated locally, while L k -l k Part of it is offloaded to a base station equipped with a mobile edge computing (MEC) server through non-orthogonal multiple access (NOMA).
[0052] At the same time, there is an illegal eavesdropping party set up in the system, trying to intercept the user's offloading tasks to the base station.
[0053] The base sta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com