Fast and safe hardware multiplier for SM2 and application thereof
A multiplier and security technology, applied in the field of information security, can solve the problems of long operation time, complex hardware structure, no SM2 parameter design, etc., and achieve the effect of shortening the delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
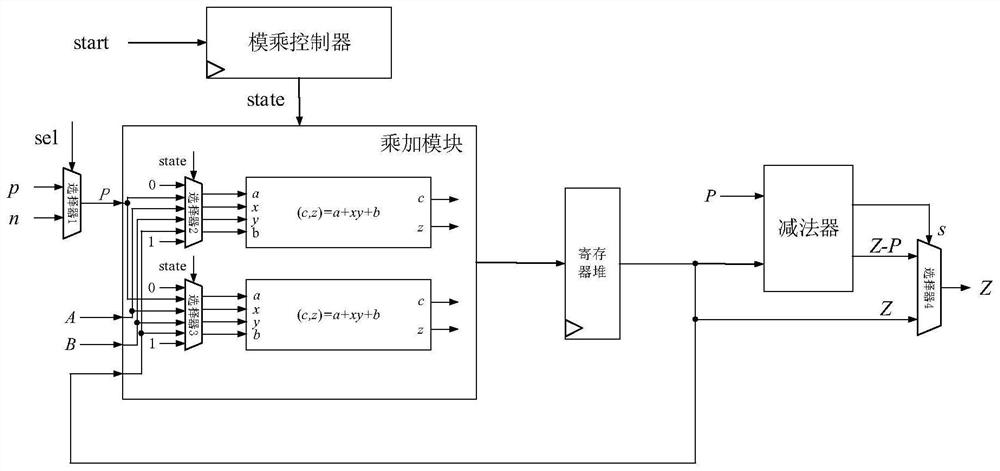
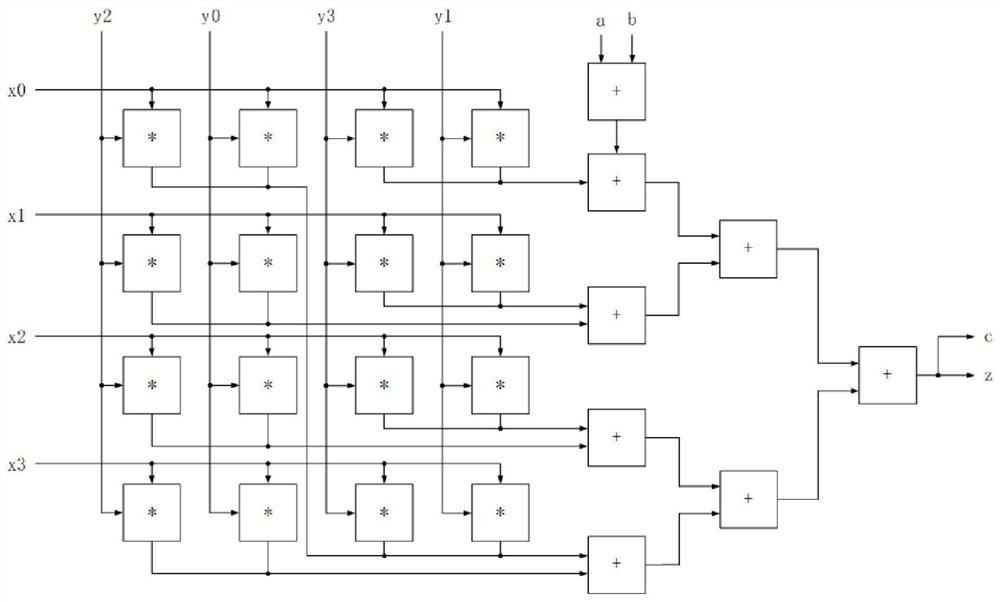
[0017] Such as figure 1 As shown, the present embodiment relates to a kind of multiplier that realizes Montgomery modular multiplication operation, including: multiplication and addition module, modular multiplication controller, register files and subtractors and some selectors for storing intermediate results of calculation, wherein: modular The multiplying controller and the first selector are all connected with the multiplying and adding module and input the state information state and the algorithm input data P respectively, and the multiplying and adding module performs (c, z)=a+ according to the input data A, B, P and the state information state The operation of xy+b and output the result to the register file, the register file outputs the intermediate result of data Z to the fourth selector, and outputs the intermediate data t i , c a , c b , v, Z to the multiplication and addition module, the subtractor outputs the calculation result Z-P and the borrow flag s to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com