Asymmetric image encryption method based on quantum chaotic mapping and SHA-3
A technology of chaotic mapping and encryption method, which is applied in the direction of encryption device with shift register/memory, usage of multiple keys/algorithms, public key for secure communication, etc., which can solve key distribution and storage difficulties, image information Issues such as poor security hiding effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The accompanying drawings are for illustrative purposes only and cannot be construed as limiting the patent;
[0083] For those skilled in the art, it is understandable that some well-known structures and descriptions thereof may be omitted in the drawings.
[0084] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
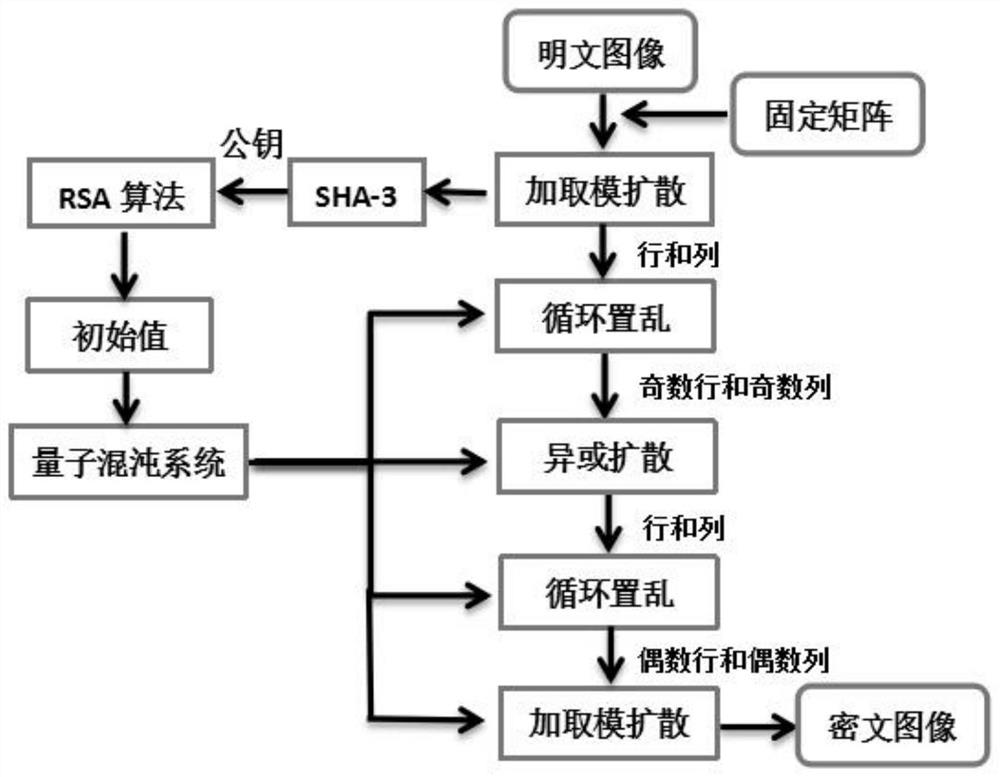
[0085] This embodiment proposes an asymmetric image encryption method based on quantum chaotic mapping and SHA-3, such as figure 1 As shown, it is a flow chart of the asymmetric image encryption method based on quantum chaotic mapping and SHA-3 in this embodiment.
[0086] In the asymmetric image encryption method based on quantum chaotic mapping and SHA-3 proposed in this embodiment, its specific steps are as follows:
[0087] S1: Use the RSA algorithm to randomly generate a key pair; the specific steps are as follows:
[0088] S1.1: Randomly select two differ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com