Encrypted malicious traffic detection device and method supporting variable-length input
A malicious traffic and detection device technology, applied in the field of network security, can solve problems affecting the detection accuracy of encrypted malicious traffic, loss of traffic characteristics, etc., and achieve the effect of improving detection accuracy and reflecting completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further explained below in conjunction with accompanying drawing and specific embodiment:
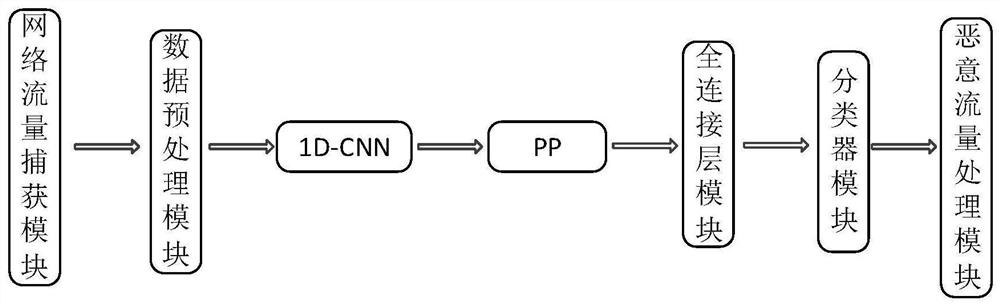
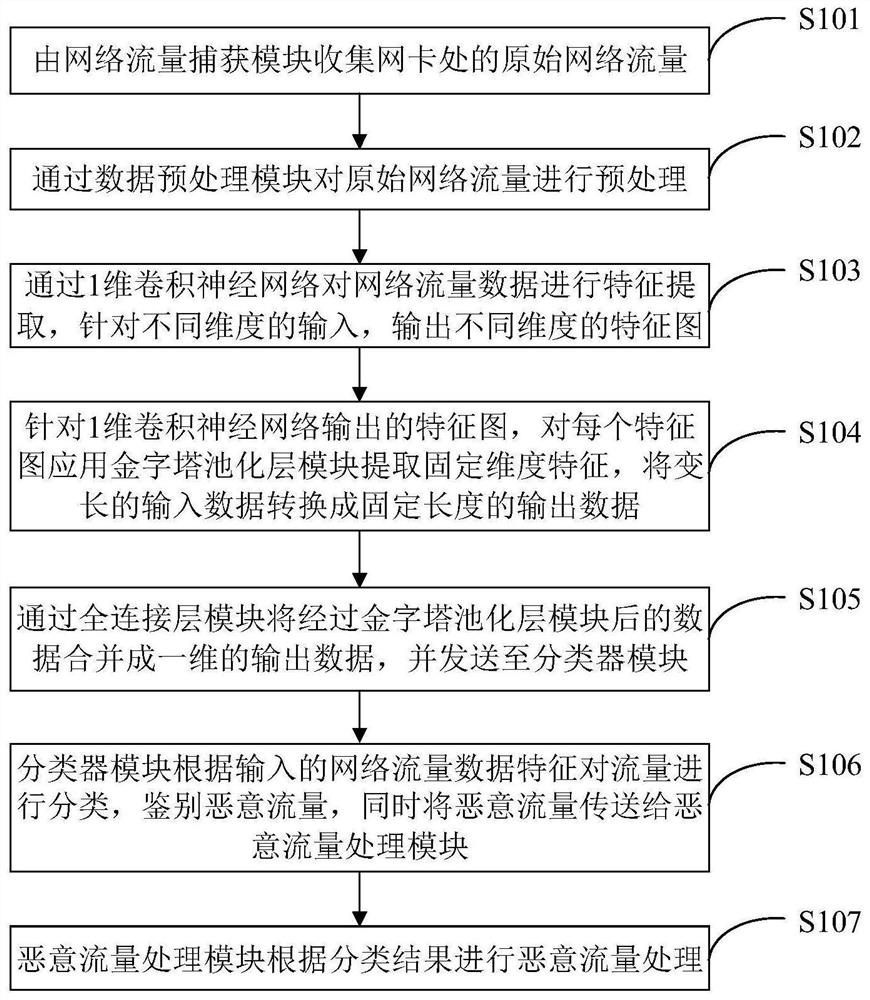
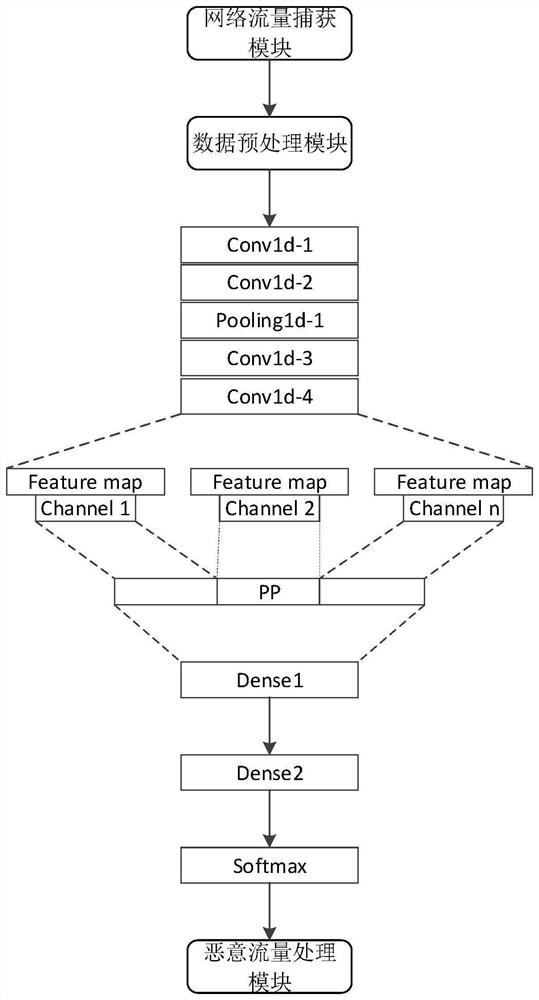
[0035] Such as figure 1 As shown, an encrypted malicious traffic detection device that supports variable-length input includes: a network traffic capture module, a data preprocessing module, a 1-dimensional convolutional neural network (1D-CNN) module, a pyramid pooling layer (PP) module, Fully connected layer module, classifier module and malicious traffic processing module.
[0036] The network flow capturing module is used to collect original network flow at the network card node; the data length of the original network flow is not fixed.
[0037] The data preprocessing module is used to clean the original network traffic data, remove invalid traffic data, and at the same time divide the traffic data into dimensions according to bytes, convert it into a data format suitable for 1-dimensional convolutional neural network input, and obtain a variab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com