Method for improving throughput of block chain based on fragmentation technology
A blockchain and throughput technology, applied in the field of improving blockchain throughput based on sharding technology, can solve problems such as insufficient satisfaction, and achieve the effect of improving transaction throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
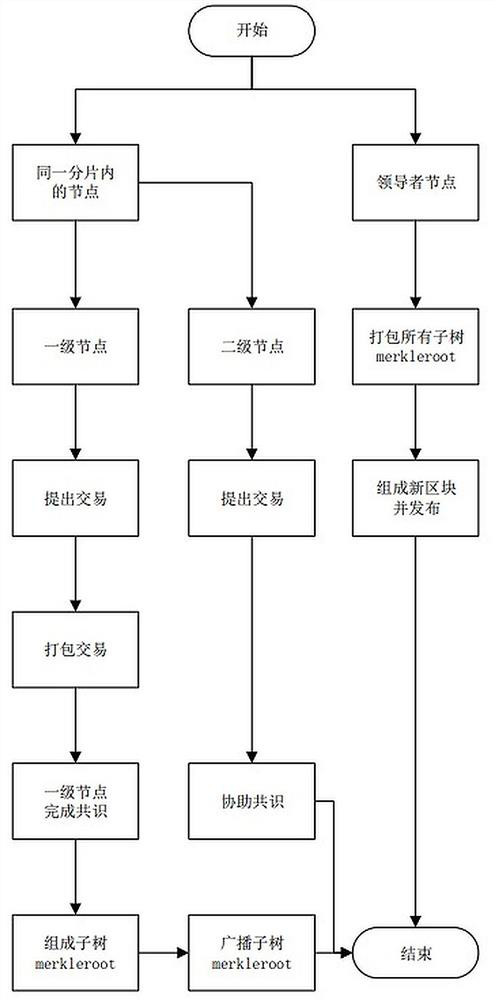
[0029] This embodiment discloses a method for improving blockchain throughput based on sharding technology, such as image 3 , including the following steps:
[0030]Step 1. When each node in the blockchain joins the blockchain, an asymmetric encryption algorithm is added to the source code of the new node created in the blockchain, thereby generating a pair of asymmetric keys locally, which are the public key Pk and Private key Sk.
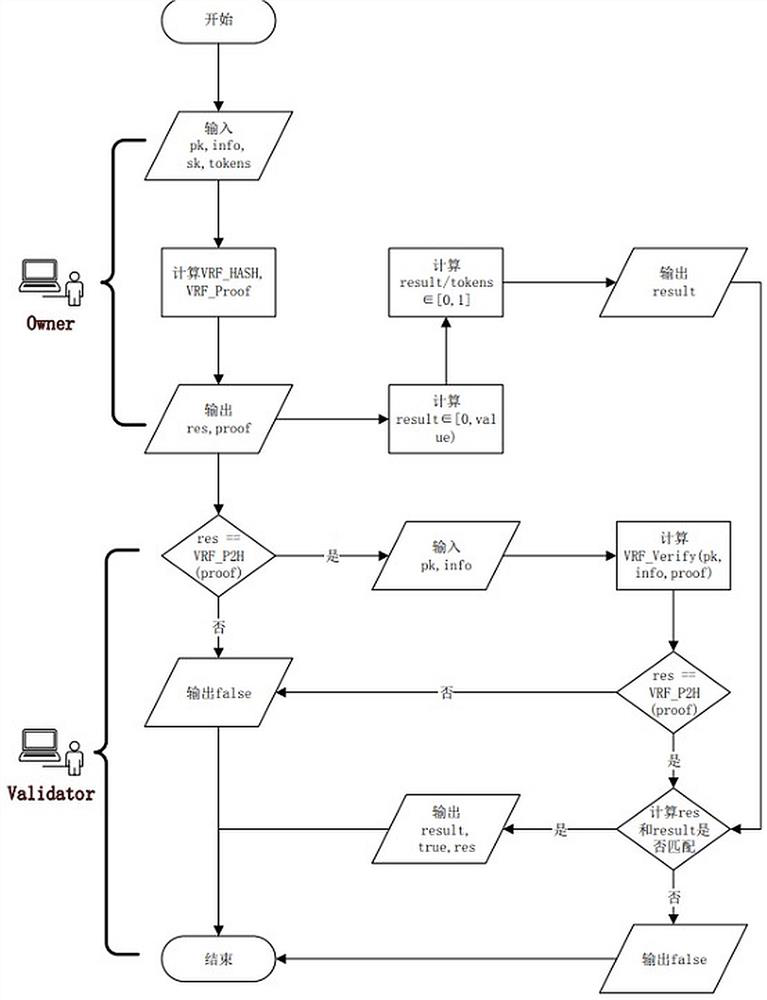
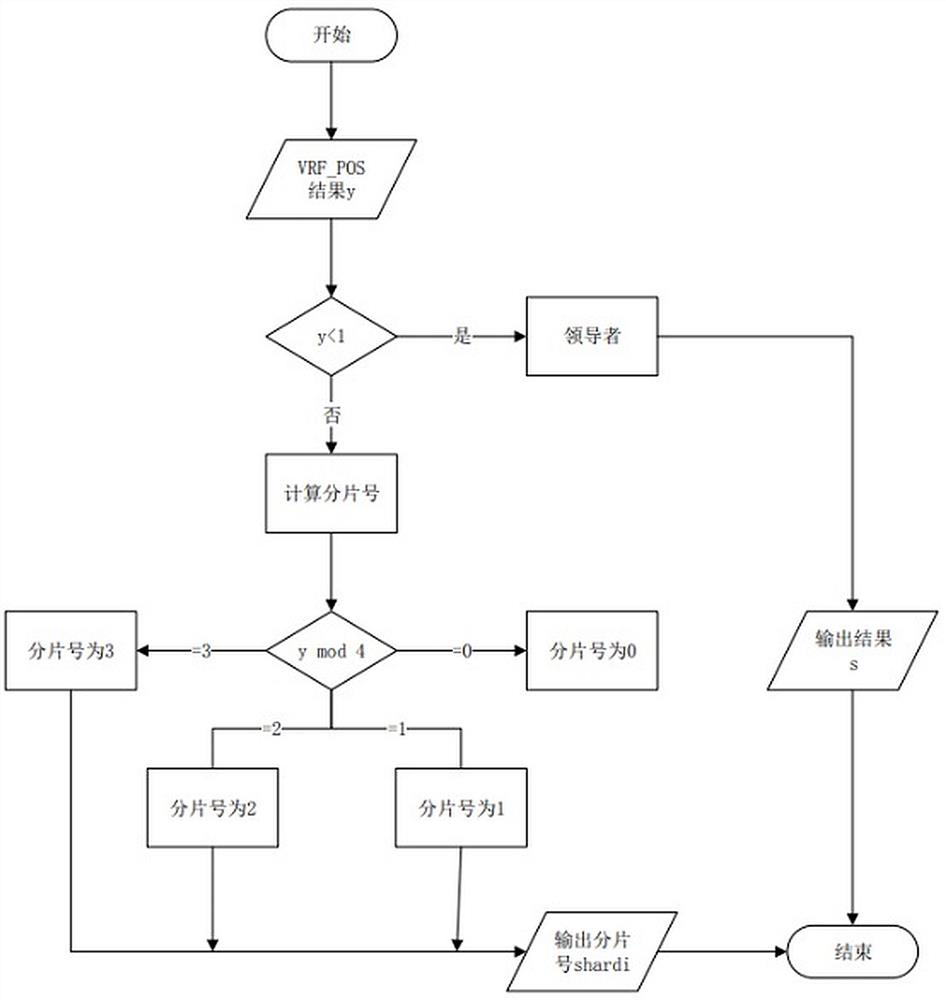
[0031] Step 2, input the public key Pk and private key Sk generated by each node in step 1, and the verifiable parameter information of the converging node in the blockchain into the VRF_Pos algorithm, and the VRF algorithm random function in the VRF_Pos algorithm follows the set Random value range, generate an intermediate result proof and a random number res for each node, and then use the POS equity proof algorithm in the VRF_Pos algorithm to prove that the random number res of each node is correct, so as to achieve the goal of joining the bl...
Embodiment 2
[0041] To apply sharding technology to the blockchain, there are two main sections, one is network sharding and the other is transaction sharding. Network sharding is mainly a strategy of randomly sharding nodes in the blockchain according to certain rules. Transaction sharding is to divide different transactions into different network shards, so that different shards can process different transactions at the same time, so as to improve transaction efficiency. throughput method.
[0042] Specifically, the idea of network sharding is to divide the entire blockchain network into multiple sub-networks, each sub-network contains a part of nodes, so that transactions can be processed in parallel by nodes of different sub-networks, and malicious nodes are in each network Inevitably, in order to prevent a sub-network from being controlled by a large number of malicious nodes, the best way is to perform random sharding.
[0043] In this embodiment, an improved VRF (Verifiable Rando...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com