Attack data packet traceability method and system based on dynamic probabilistic dual-domain packet marking
A data packet and marking technology, applied in the transmission system, complex mathematical operations, electrical components, etc., can solve the problems of difficult to accurately reconstruct the attack path, too large log information, difficult to store, etc., to achieve calculation pressure balance and reduce errors , the effect of roughly balancing the number of marks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be described in further detail below in conjunction with the accompanying drawings.
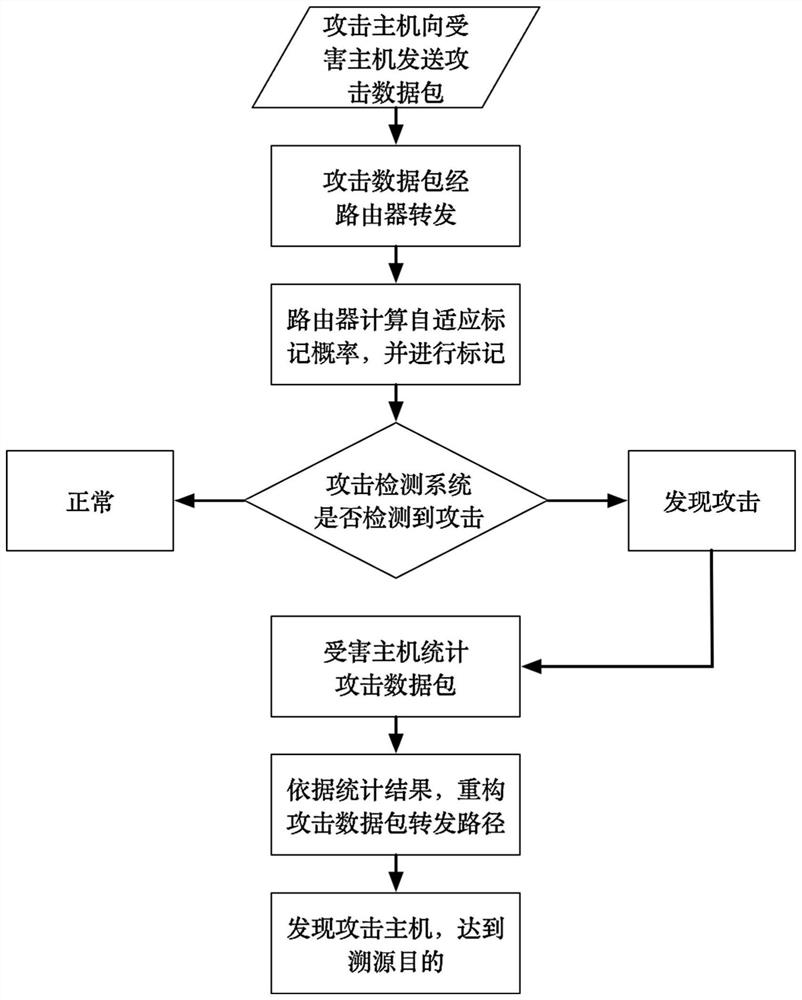
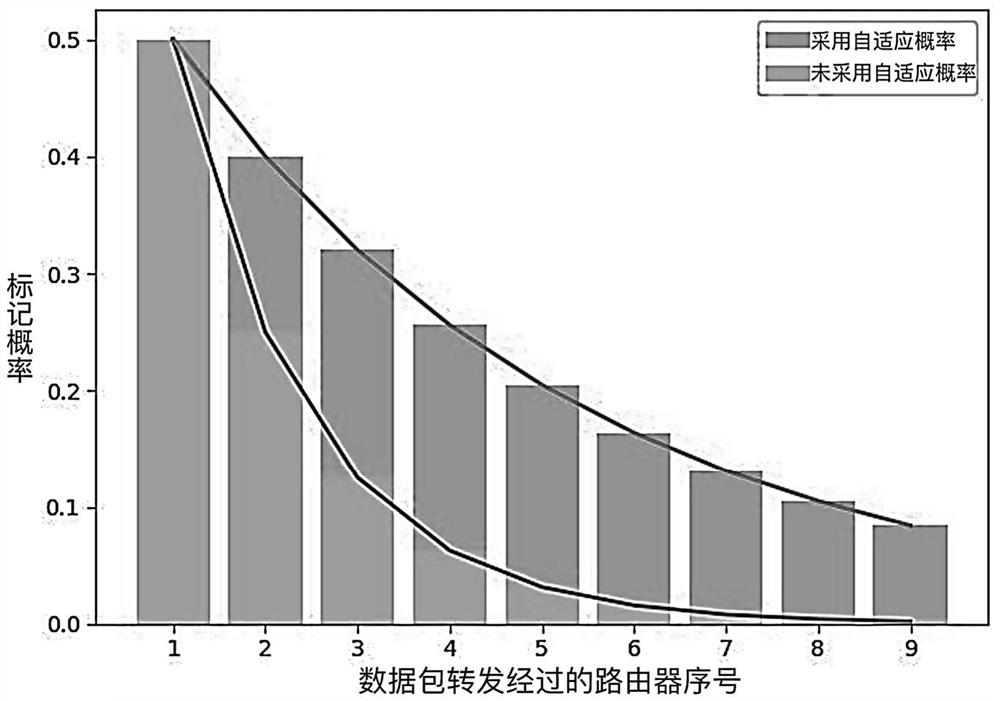
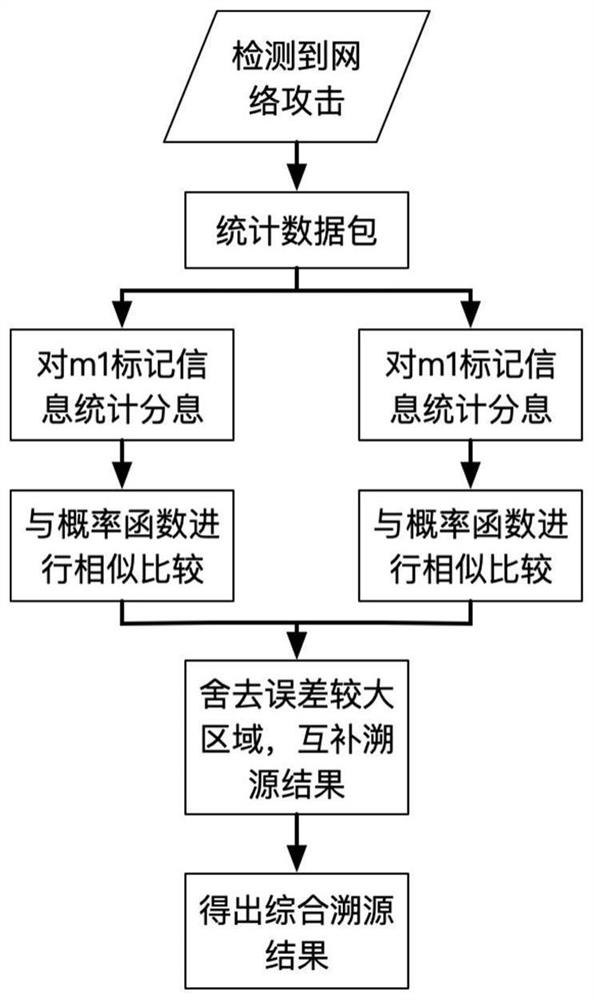
[0032] The attack data packet tracing method based on dynamic probabilistic dual-domain packet marking in the present invention combines the advantages of the dynamic probabilistic packet marking algorithm in the probabilistic packet marking algorithm, and sets two marking fields in the packet header of the IP message, and the router calculates the marking probability revision Parameters and record its own information to the two marking domains through two marking strategies. The overall flow chart is as figure 1 shown. When a network attack is detected, the victim host can count the attack data packets and effectively trace the attack path of the data packets.
[0033] 1. Mark space settings;
[0034]For the setting of the mark space, use the idle data packet in the head of the IP message as the record space of the mark. The current network is constantly...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com