Log processing method and device, computer equipment and storage medium
A processing method and log technology, applied in the computer field, can solve problems such as difficulty in configuration file management and maintenance, and achieve the effect of improving flexibility and applicability, and improving rationality and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
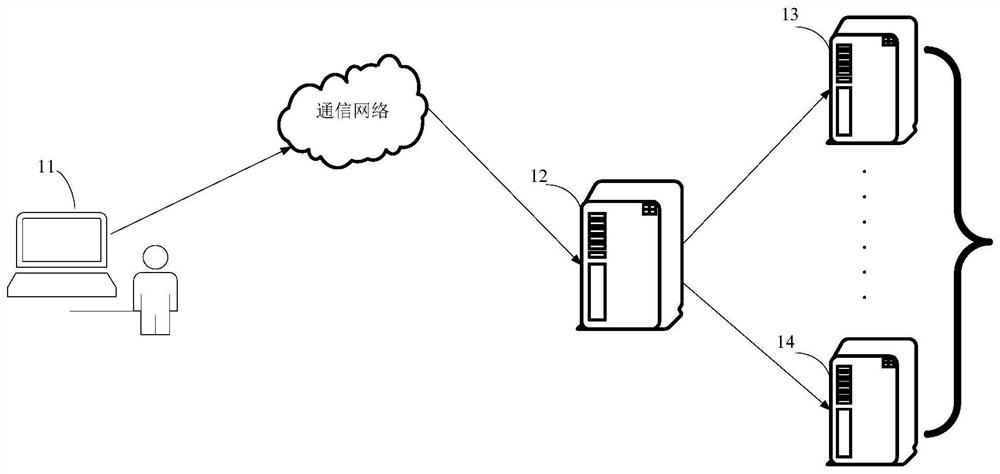
[0080]In order to facilitate the understanding of this embodiment, an application scenario of a log processing method disclosed in an embodiment of the present disclosure is firstly introduced, for example figure 1 As shown in , it is a schematic diagram of an application scenario of a log processing method provided by an embodiment of the present disclosure. The user logs in to the application server 12 through the application client installed in the terminal device 11, wherein the application client can be a web browser, or an application client installed in a terminal device, such as a mobile phone, a tablet computer, etc., or Web pages or applets embedded in applications, etc. The communication connection between the terminal device 11 and the application server 12 is through a network, and the network may be a local area network, a cellular network, a wide area network, or the like. The terminal device 11 can be a portable device (such as a mobile phone, a tablet, a note...
Embodiment 2
[0084] The log processing method provided by the embodiment of the present disclosure will be described below by taking the execution subject as a computer device as an example.
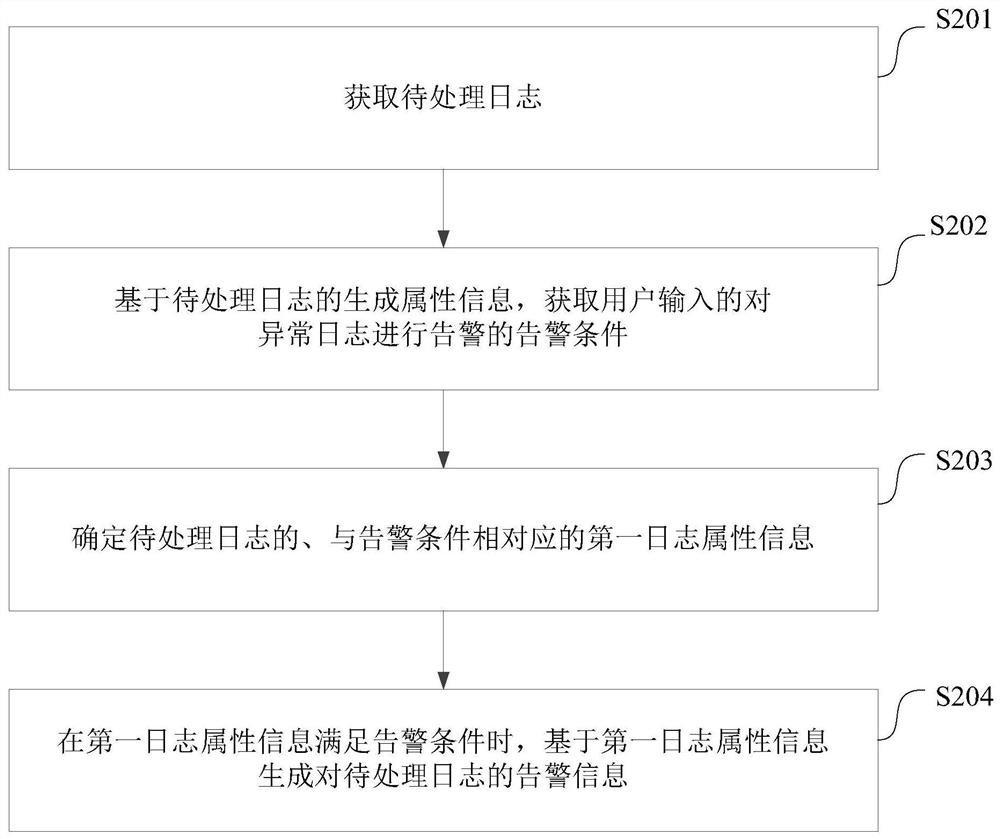
[0085] like figure 2 As shown, it is a flow chart of a log processing method provided by an embodiment of the present disclosure, which may include the following steps:
[0086] S201: Obtain logs to be processed.
[0087] During specific implementation, when the application generates abnormal pending logs during operation, the local log collector Filebeat collects each abnormal pending log generated by the application and sends it to the Kafka message queue for storage, wherein, The purpose of storing pending logs in the Kafka message queue is to prevent the application from generating too many abnormal pending logs within a certain period of time. Sending them directly to the application server may cause the application server to go down and cause confusion in application functions. Furthermore, ...
Embodiment 3
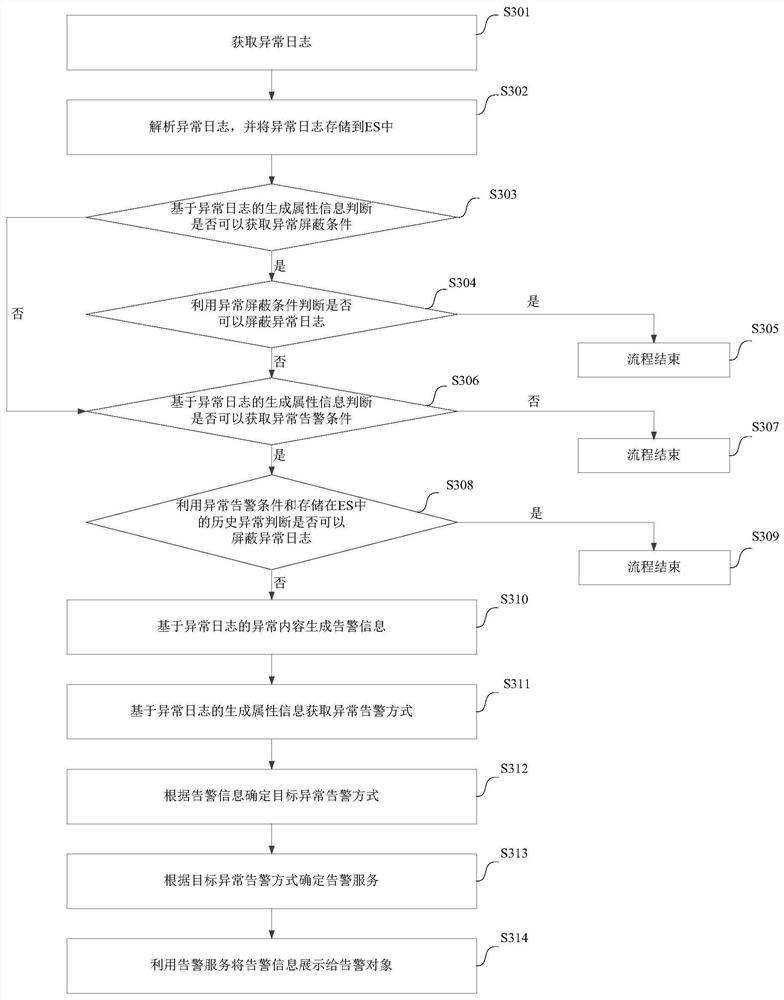
[0125] like image 3 As shown, it is a flowchart of a specific implementation process of a log processing method provided by an embodiment of the present disclosure, which may include the following steps:
[0126] S301: Obtain an exception log.
[0127] In this step, when the application generates abnormal logs during operation, filebeat collects them and sends them to the Kafka message queue for storage. Further, the application server obtains the abnormal logs stored in the Kafka message queue.
[0128] S302: Parse the exception log, and store the exception log in the ES.
[0129] During specific implementation, the acquired exception log is analyzed to obtain the generation attribute information and exception content of the exception log.
[0130]S303: Determine whether an exception shielding condition can be acquired based on the generation attribute information of the exception log.
[0131] During specific implementation, if the abnormality masking condition can be ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com